Windows Management Instrumentation Queries
The following examples show how to hunt for malicious behavior associated with Windows Management Instrumentation (WMI).
The example queries in this section are meant to be a starting point for your investigations. You may need to update the Features (filters) in each query to use indicators specific to your environment or situation.
Each of these examples is formatted with the individual Element in the query on its own separate line, in bold text. Features (filters) applied to the Element follow the Element name in regular weight text. Each example also contains a description of the goal of the hunt and the explanatory statement of what you want to find.
In this topic:
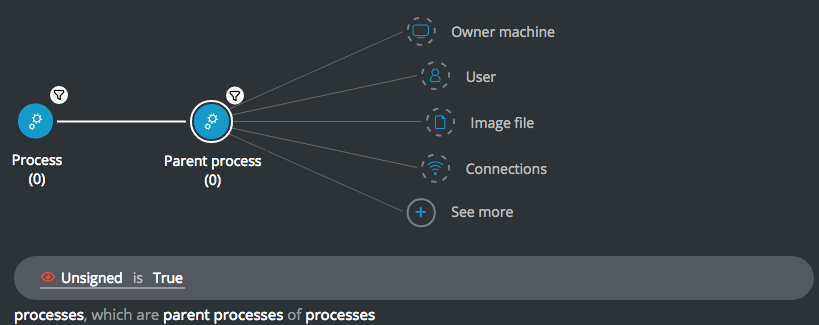
Wmiprvse.exe with unsigned parent process
Goal: Find wmiprvse processes executed by an unsigned parent process
Explanatory statement: I want to find WMI processes that are run by a parent process that was not signed.
Construct this query:
Process Element -> filter for Process name is wmiprvse.exe THEN
Parent process Element -> filter for Unsigned is True
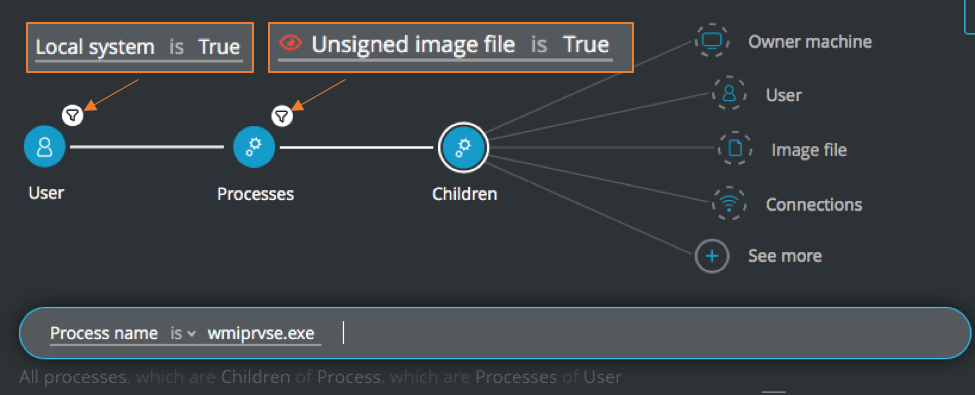
Wmiprvse.exe with unsigned parent process executed by SYSTEM user
Goal: Find wmiprvse processes executed by an unsigned parent process that is executed by SYSTEM user.
Explanatory statement: I want to find WMI processes run by a parent process that is unsigned and the user that is running the process is a SYSTEM level user.
Construct this query:
User Element -> filter for Local system is True THEN
Process Element -> filter for Unsigned image file is True THEN
Children Element -> filter for Process name is wmiprvse.exe
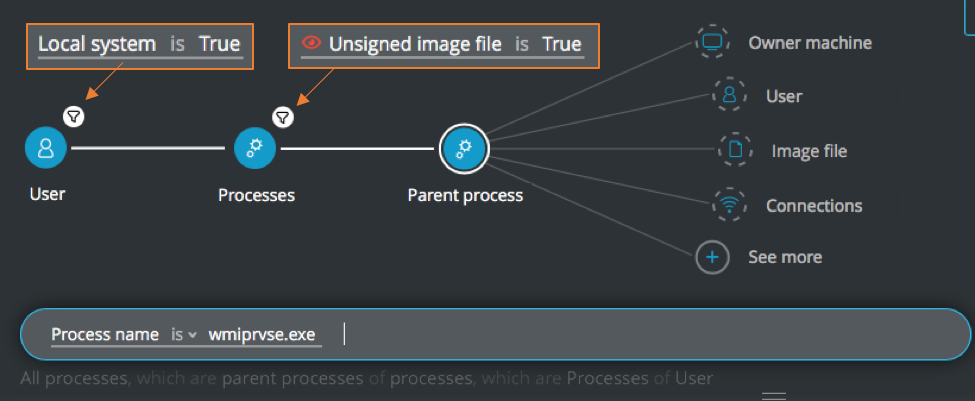
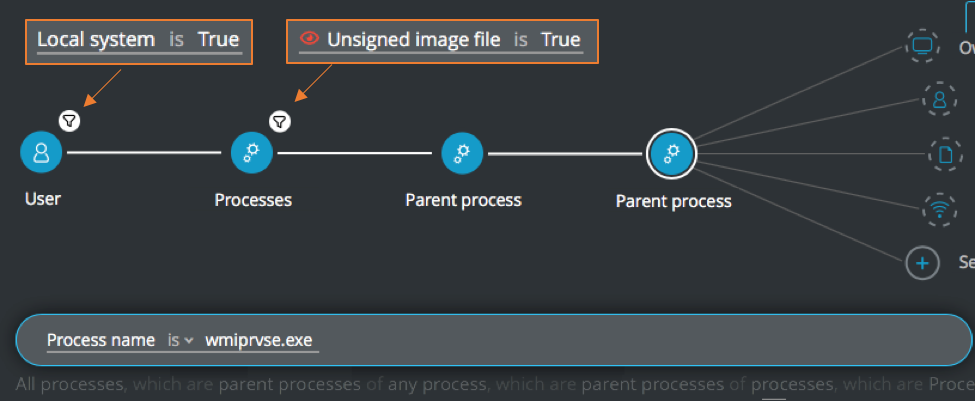
Unsigned child or grandchild process of wmiprvse.exe executed by SYSTEM user
Goal: Find unsigned processed which are children or grandchildren of wmiprvse.exe processes and are executed by SYSTEM user.
Explanatory statement: I want to find descendant processes of WMI that are unsigned and are run by a SYSTEM-level user
Construct this query:
Child processes:
User Element -> filter for Local system is True THEN
Process Element -> filter for Unsigned image file is True THEN
Parent process Element -> filter for Process name is wmiprvse.exe
Grandchild processes:
User Element -> filter for Local system is True THEN
Process Element -> filter for Unsigned image file is True THEN
Parent process Element THEN
Parent process Element -> Process name is wmiprvse.exe
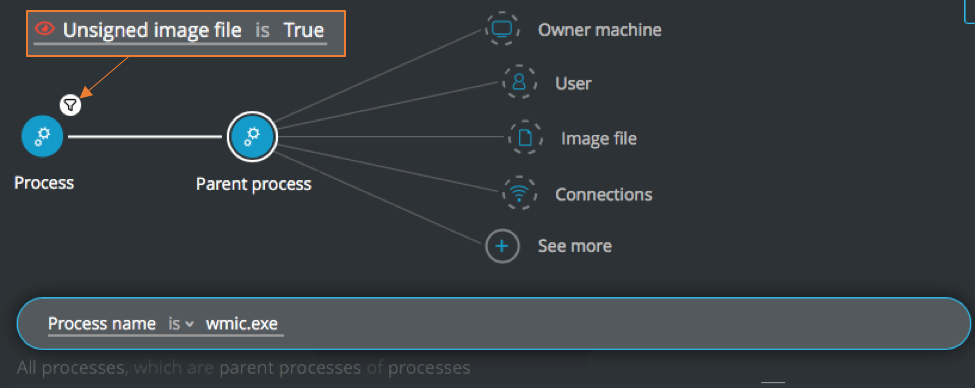
Execution of unsigned child or grandchild process by wmic.exe
Goal: Find unsigned child or grandchild processes executed by wmic.exe.
Explanatory statement: I want to find descendant processes run from WMI activity.
Construct these queries:
Child processes:
Process Element -> filter for Unsigned image file is True THEN
Parent process Element -> filter for Process name is wmic.exe
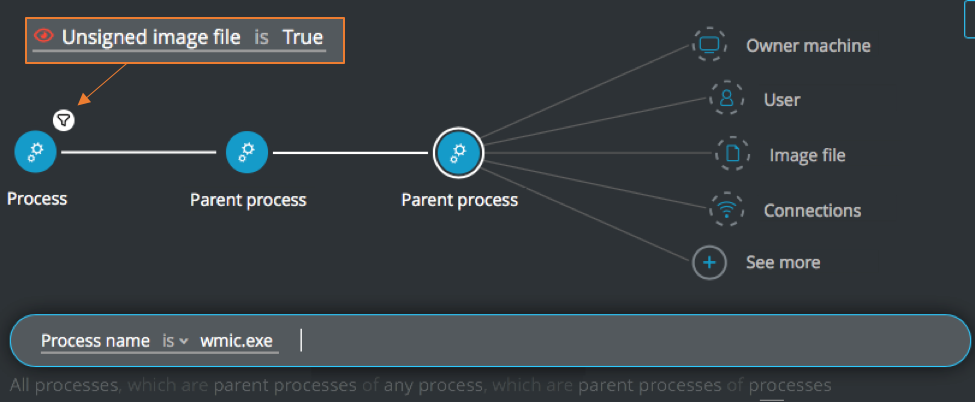
Grandchild processes:
Process Element -> filter for Unsigned image file is True THEN
Parent process Element THEN
Parent process Element -> Process name is wmic.exe
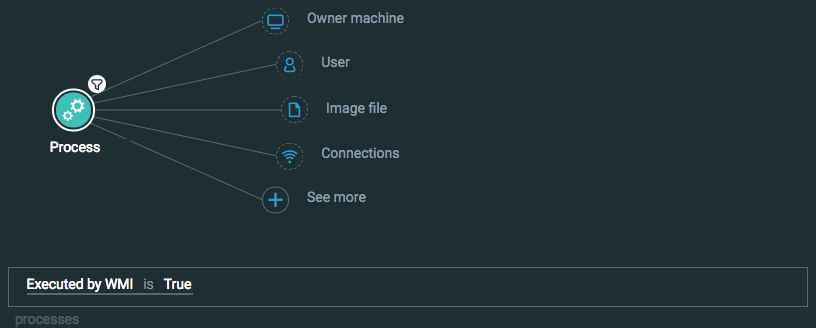
Find processes executed by WMI
Goal: Find processes that have been executed by WMI on your machines.
Explanatory statement: I want to find processes that have been run because of WMI activity on my environment.
Construct this query:
Process Element -> filter for Executed by WMI is True
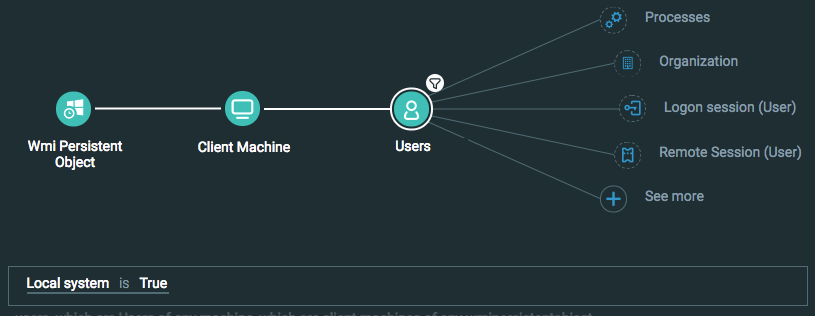
Find a WMI Persistent Object created by a local system user
Goal: Find a WMI persistent object that has been created by a local system user
Explanatory statement: I want to find WMI persistent objects that local users have created
Construct this query:
Process Element THEN
Client Machine THEN
Users Element -> filter for Local system is True