Reconnaissance Queries
As part of their attack cycle, attackers will attempt to learn more about your environment.
The example queries in this section are meant to be a starting point for your investigations. You may need to update the Features (filters) in each query to use indicators specific to your environment or situation.
Each of these examples is formatted with the individual Element in the query on its own separate line, in bold text. Features (filters) applied to the Element follow the Element name in regular weight text. Each example also contains a description of the goal of the hunt and the explanatory statement of what you want to find.
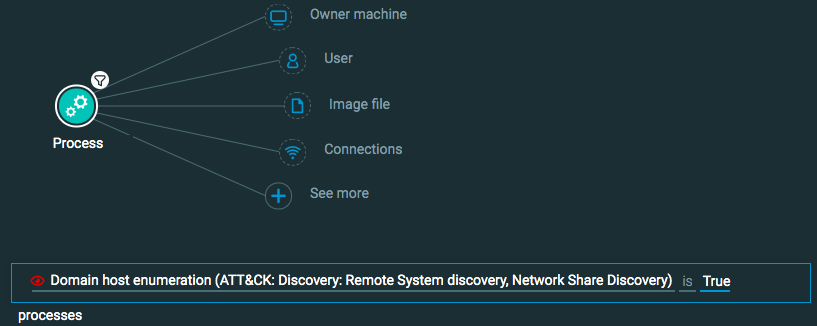
Host enumeration
Goal: Find evidence of host enumeration.
Explanatory statement: I want to find examples of processes performing host enumeration techniques.
Construct this query:
Process Element -> filter for Domain host enumeration is True
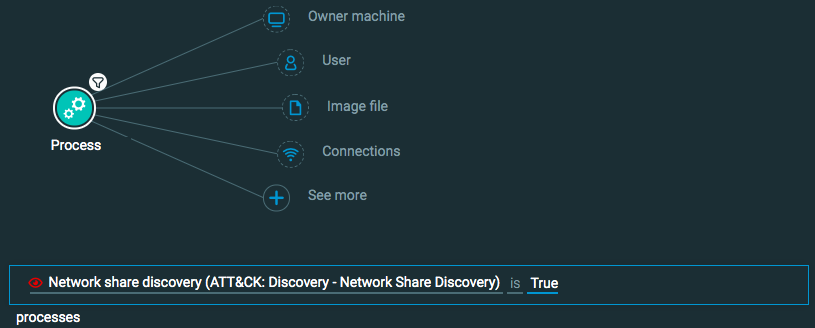
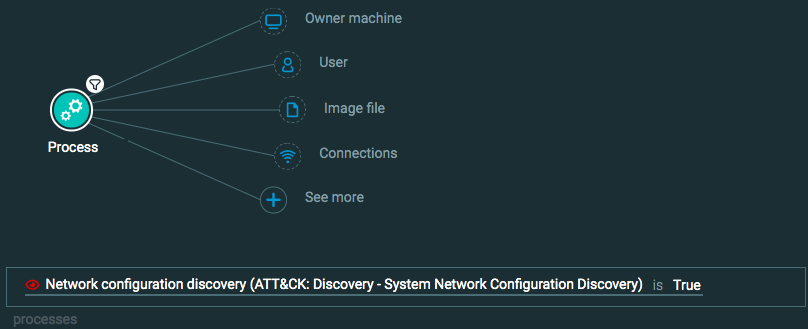
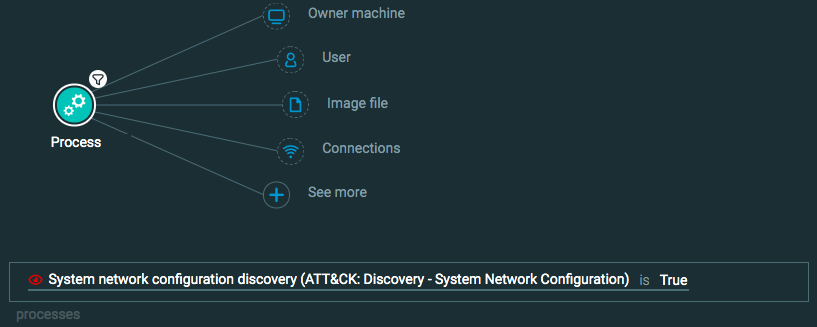
Network enumeration
Goal: Find evidence of a process performing network enumeration.
Explanatory statement: I want to find examples of processes performing network enumeration techniques.
Construct one of the following queries:
Query 1:
Process Element -> filter for Network share discovery is True
Query 2:
Process Element -> filter for Network configuration discovery is True
Query 3:
Process Element -> filter for System network configuration discovery is True
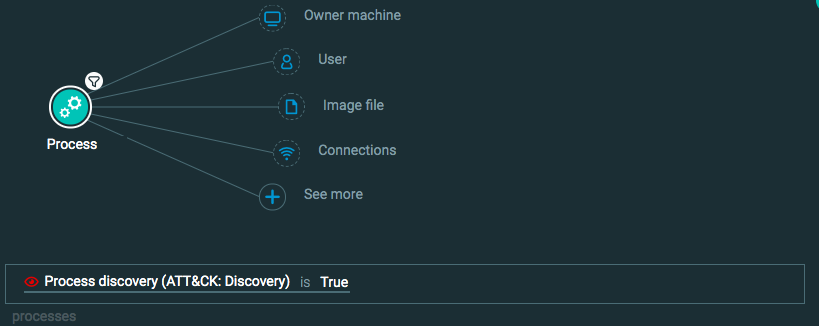
Process enumeration
Goal: Find evidence of a process performing process enumeration to gain more information about running processes.
Explanatory statement: I want to find details of processes that are using process enumeration techniques.
Construct this query:
Process Element -> filter for Process discovery is True
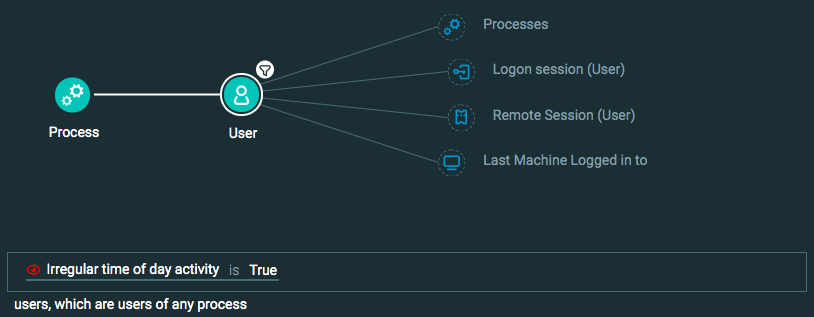
Abnormal hour activity
Goal: Find users performing activities at a strange hour.
Explanatory statement: I want to find users whose activity is outside the normal hours of activity.
Construct one of the following queries:
Query 1:
Process Element
User Element -> filter for Irregular time of day activity is True
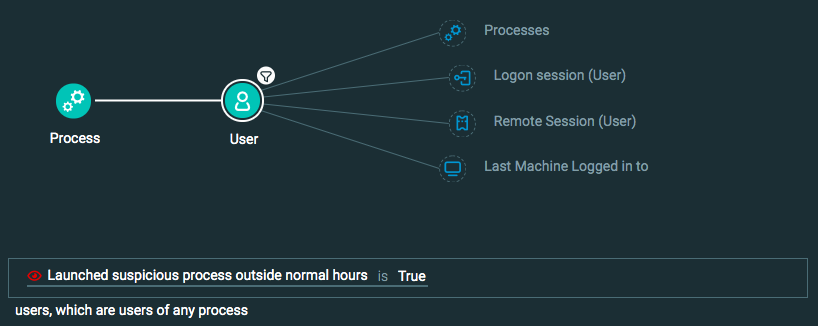
Query 2:
Process Element
User Element -> filter for Launched suspicious process outside normal hours is True