Malicious Process Execution Queries
As part of their attack cycle, attackers will attempt to run malicious process activities.
The example queries in this section are meant to be a starting point for your investigations. You may need to update the Features (filters) in each query to use indicators specific to your environment or situation.
Each of these examples is formatted with the individual Element in the query on its own separate line, in bold text. Features (filters) applied to the Element follow the Element name in regular weight text. Each example also contains a description of the goal of the hunt and the explanatory statement of what you want to find.
In this topic:
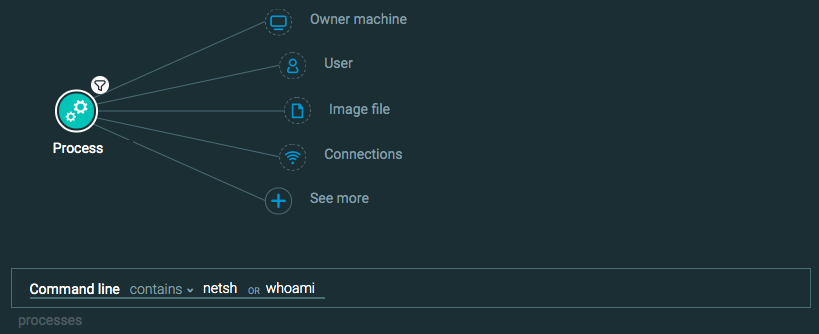
Command line process execution
Goal: Find processes running malicious commands.
Explanatory statement: I want to find an example of <<command>> running in my environment.
Construct this query:
Process Element -> filter for Command line contains _______
Renamed processes
Goal: Find renamed processes.
Explanatory statement: I want to find examples of processes that were renamed or had their image file/binary file renamed
Construct one of the following queries:
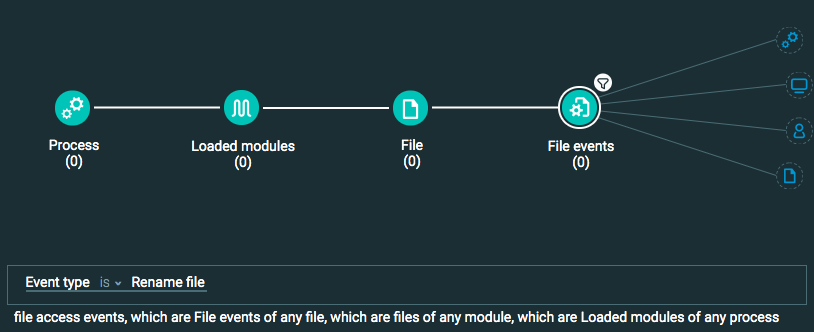
Query 1:
Process Element
Loaded modules Element
File Element
File Event Element -> filter for Event type is Rename file
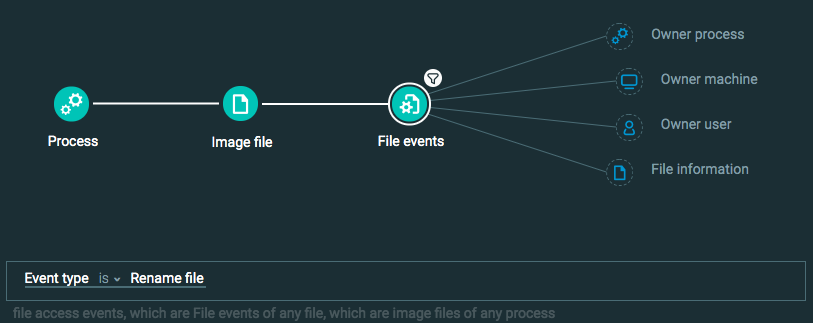
Query 2:
Process Element
Image File Element
File Event Element -> filter for Event type is Rename file
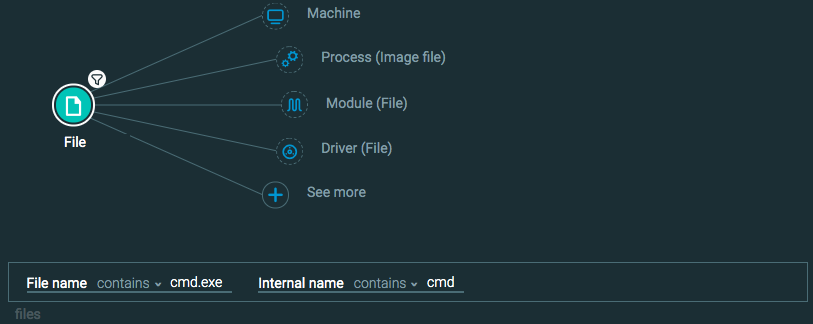
Query 3:
File Element -> filter for File name contains ______ Internal name contains ______
Legitimate applications repurposed for malicious use
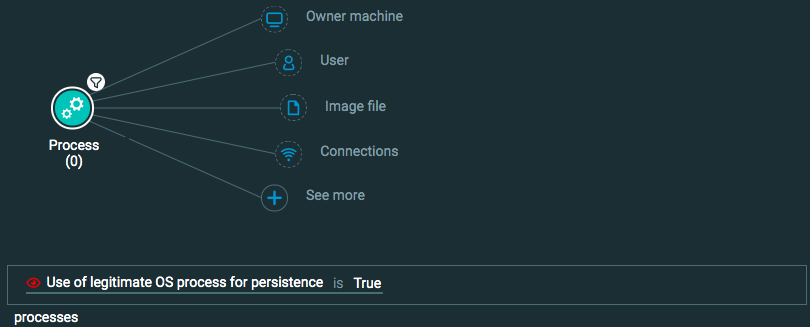
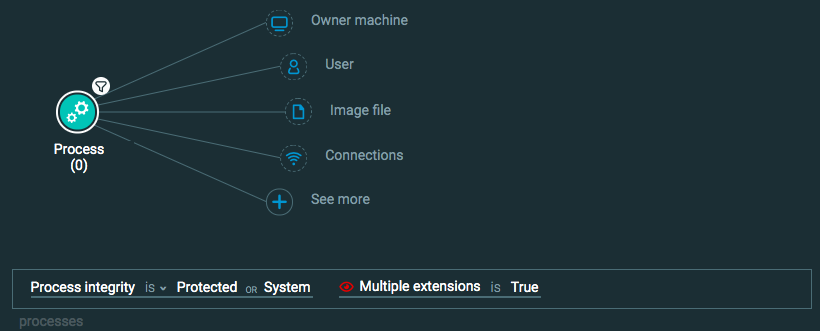
Goal: Find when a legitimate application (such an operating system process or application) is used in a malicious manner.
Explanatory statement: I want to find instances where processes that are considered legitimate are used in an unusual and malicious way
Construct one of the following queries:
Query 1:
Process Element -> filter for Use of legitimate OS process for persistence is True
Query 2:
Process Element -> filter for Process integrity is Protected or System AND (select Feature filter for malicious behavior)
Script execution
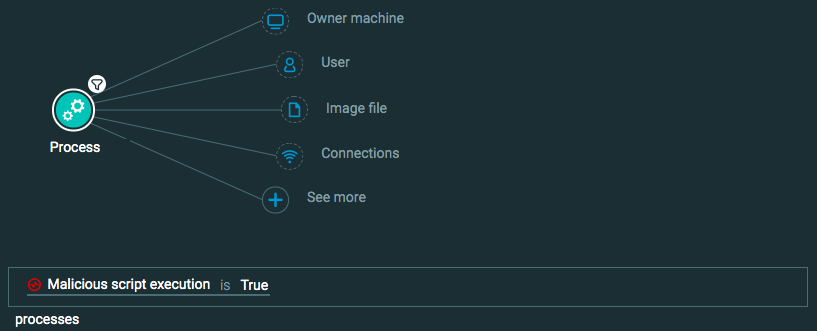
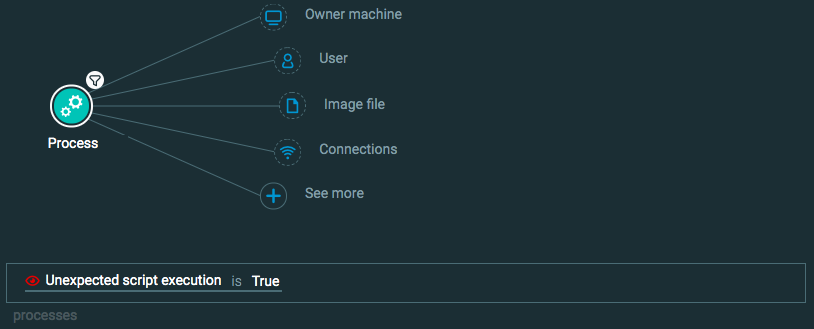
Goal: Find malicious script execution.
Explanatory statement: I want to find instances where a process ran a script marked as malicious or ran a script that was not expected.
Construct one of the following queries:
Query 1:
Process Element -> filter for Malicious script execution is True
Query 2:
Unexpected script execution is True
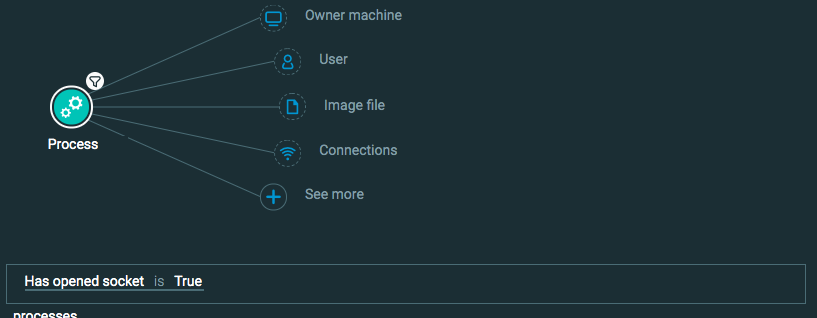
Process has a listening port
Goal: Find applications that have opened listening ports
Explanatory statement: I want to find instances and details when a process opens a listening connection.
Construct this query:
Process Element -> filter for Has opened socket is True
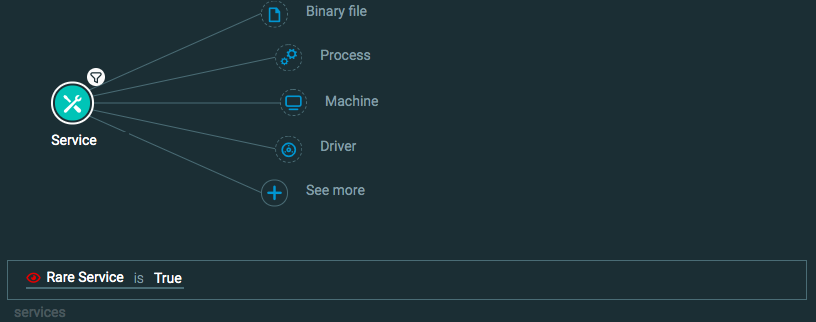
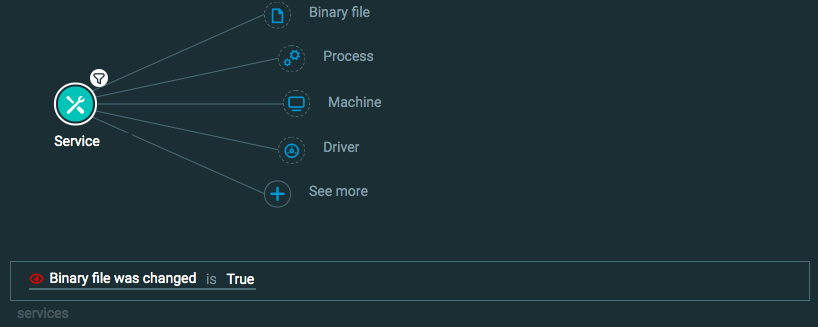
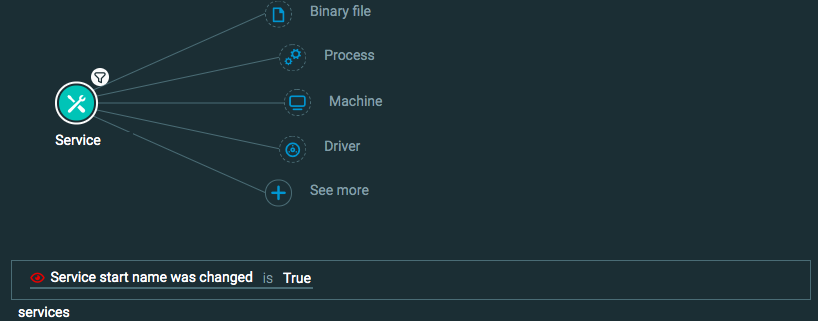
Malicious services for a process
Goal: Find malicious services.
Explanatory statement: I want to find instances of malicious services due to their rare nature or changes in the service characteristics.
Construct one of the following queries:
Query 1:
Process Element
Service Element -> filter for Rare service is True
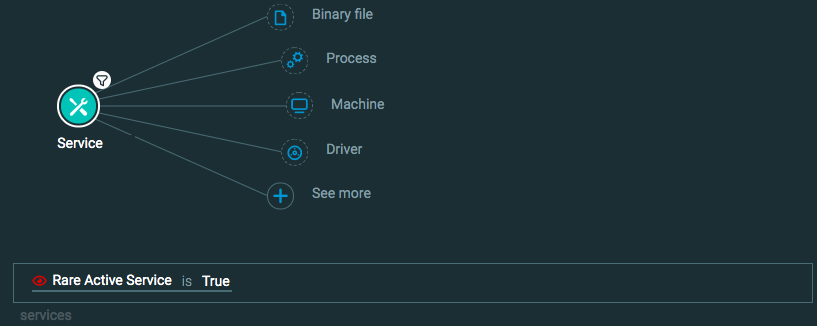
Query 2:
Process Element
Service Element -> filter for Rare active service is True
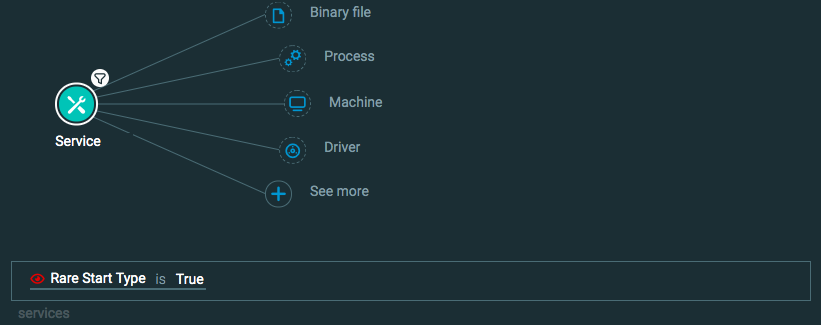
Query 3:
Process Element
Service Element -> filter for Rare start type is True
Query 4:
Process Element
Service Element -> filter for Binary file was changed is True
Query 5:
Process Element
Service Element -> filter for Service start name was changed is True