Understand Threat Activity
A primary part of your daily workflow likely includes understanding active threat activity in your organization’s network. To help understand threat activity, the Cybereason platform generates MalOps to identity likely malicious behavior. A MalOp, or malicious operation, ties together the attack chain, or the complete, end-to-end story of a cyber attack. Through advanced detection techniques, Cybereason recognizes when multiple suspicious activities are likely part of a single security incident, and generates a MalOp which provides security analysts with a single point of investigation.
This section presents information about how to understand, manage, and remediate MalOps in your Cybereason platform:
View MalOps in the Malops management screen:
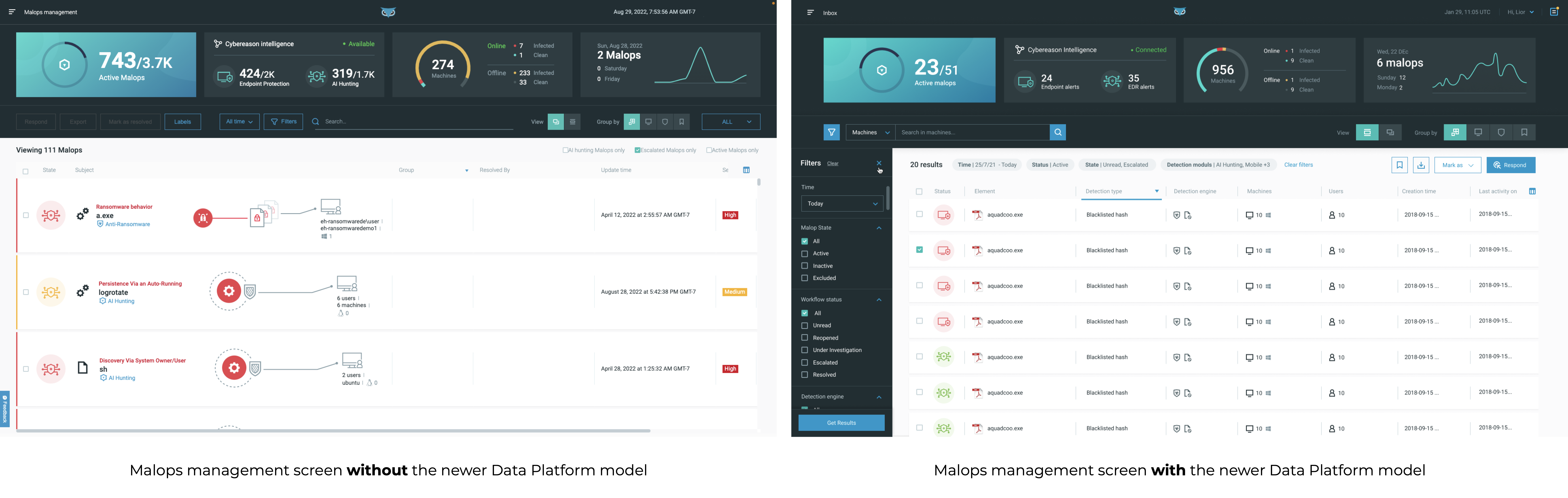
For customers with the newer Data Platform model, see View MalOps with the Data Platform Architecture.
For customers without the newer Data Platform model, see View Malops.
If you are unsure whether your environment is based on the newer Data Platform model, use the following image as a guide:
Learn about the different type of MalOps and their components: Malop Types and Components
Learn how endpoint data becomes a MalOp: Fact to MalOp
Learn how MalOp activity is grouped: MalOp Grouping
Learn how to understand the activity in a MalOp: Examine MalOp Details
Learn how to analyze the MalOp details to determine the malicious nature of the activity: Analyze MalOp properties to determine threat level
Learn how to manage the MalOp workflow: Manage the MalOp Workflow
Choose a response option. The Cybereason platform provides a number of response options, including the ability to:
Looking for XDR MalOps? See Examine XDR Malops.
Malop Response Demo
Watch this video to learn how to respond to MalOps using the Malops management screen:
In this section:
- Fact to MalOp
- Malop Types and Components
- MalOp Grouping
- MalOp Types in Depth
- View MalOps with the Data Platform Architecture
- View Malops
- Examine MalOp Details
- Analyze MalOps and Determine Threat Level
- Manage the MalOp Workflow
- Remediate MalOps
- MalOp Remediation Examples
- Manage False Positives
- Manage Malware Alerts
- View the Global Response History