Use the MITRE ATT&CK Matrix with the Cybereason Platform
The MITRE ATT&CK matrix is a collection of more than 200 types of behaviors and techniques used by attackers during an attack. The framework combines legacy detection techniques, indicators of compromise (IoCs), and events into different categories reflecting both general and specific items that an attacker may use.
When you understand the different MITRE ATT&CK techniques, you can then search in your Cybereason platform for potential activities related to techniques that are important to you.
In this topic:
What is the MITRE ATT&CK matrix?
The MITRE ATT&CK matrix organizes the numerous activities involved in an attack into:
Tactics that reflect the portion of the attack lifecycle in which an event, action, or behavior occurs
Techniques that represent specific actions or behaviors that an attacker would use
Sub-techniques that represent examples of the behavior
Each tactic and technique has its own dedicated page in the MITRE ATt&CK site describing the tactic or technique details.
Tactic pages contain a list of all the techniques associated with the tactic. Technique pages contain an overview of the technique, examples of the technique’s use, and most importantly, suggestions for how to detect and mitigate instances of the technique.
While all the items in the matrix may be involved in malicious activity, not every item in the MITRE framework may be malicious by itself. For example, the matrix includes a technique for user account creation (Create Account). Marking every user account creation as malicious wastes an analyst’s time as they would investigate every user creation event, most of which are benign. However, the MITRE ATT&CK matrix helps you identify when a specific technique that by itself is often benign is used in conjunction with other techniques.
ATT&CK details in the Cybereason platform
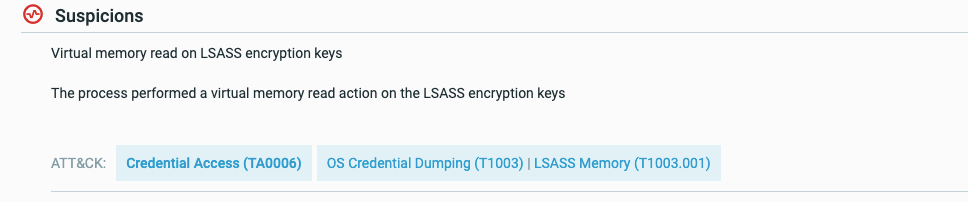
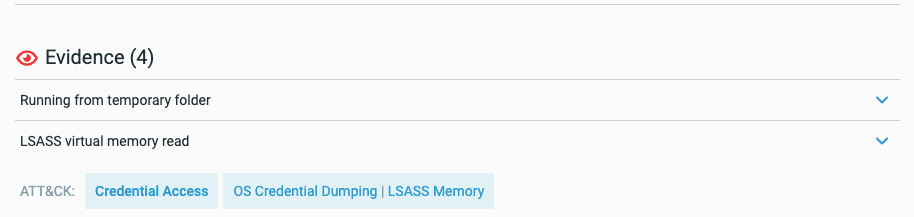
The Cybereason platform provides coverage and visibility to many parts of the ATT&CK matrix through detected MalOps, suspicions, and evidence, and through collected telemetry data.
To help you understand when MalOps, suspicions, or evidence correspond to a specific technique, the Cybereason platform adds tags with the corresponding tactic, technique, or sub-technique:
Hover over the tag to see the technique numbers:
For each of the tags, you can then click the tag name to open the relevant page in the MITRE ATT&CK site to learn more.
Watch the following video for an overview on how Cybereason displays MITRE ATT&CK tactics and techniques in Malops.
For a full listing of the tactics and techniques included in the MITRE ATT&CK matrix, see the MITRE ATT&CK Knowledge Base.
Search for ATT&CK techniques
You can search for instances of techniques using the Cybereason platform Investigation screen.
For evidence and suspicions that correspond to a tactic or technique, you can build a query based on the tactic or technique number assigned by MITRE. These numbers are represented by a string that begins with T followed by the technique number:
In addition, the reference page for every MITRE ATT&CK technique or sub-technique contains a wide variety of information to help search further:
An extensive description on how the technique or behavior works on the machine, including examples of what processes, files, and so forth that are used.
Real world malicious frameworks that use the technique.
A section on Mitigation that includes steps to respond to the technique.
A section on Detection that discusses different ways to find the technique in your organization’s environments.
You can use this information in a number of ways:
Use the keywords included in the technique’s reference page to search in the Search bar of the Investigation screen. For example, for the Account discovery technique (Discovery > Account Discovery), you can search in the Investigation screen for this keyword and find an appropriate filter:
You can analyze the Detection section and find the relevant indicators or behaviors you should detect. From these suggestions, you can write an investigation goal/statement and then build a query.
Watch the following video for an overview on creating queries to identify MITRE ATT&CK tactics and techniques.
For details on building a query and statement, see Plan a Hunt and Hunting Use-Case Example.
Search for ATT&CK techniques - example
To illustrate how to discover instances of behavior corresponding to ATT&CK techniques using the Cybereason platform, let’s look at an example of how this is done. For this example, you can use the Process Injection technique.
In the Process Injection specification, you can see that Process Injection is done in a number of ways:
Injecting DLL files to another process and then running a remote thread
Using malicious code inside a process through portable executable injection
Injecting malicious code or a DLL through a process thread
Adding malicious code through an asynchronous call to a process thread
Updating pointers inside a process to run malicious code instead of the process’s legitimate code
Using specific libraries or commands in Linux and Mac machines
You can also see there are numerous examples of malicious tools and frameworks that use process injection, including well-known ones such as Cobalt Strike, PowerSploit, and so forth.
Then in the Detection section, you see many suggestions for detection, including:
Monitor Windows API calls that are commonly used for code injection
Monitor Linux-specific commands
Monitor for named pipe creation and connection events
Analyze command line arguments of processes for actions that sync with code injection
Search for malicious tools like PowerSploit and PowerShell performing injection
Given this information, there are a number of ways to search for code injection using the Cybereason platform:
Method |
Description |
|---|---|
Use the Injection keyword |
The Cybereason platform contains a large number of detection rules around code injection: |
Search by command line |
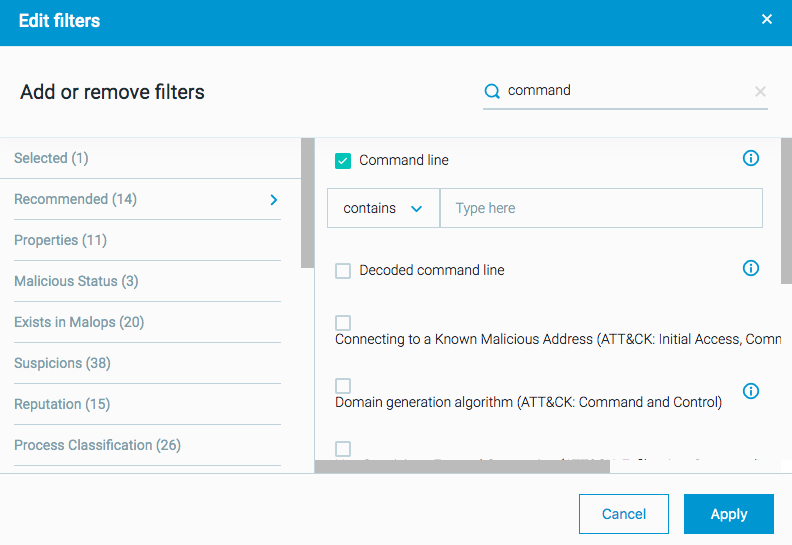
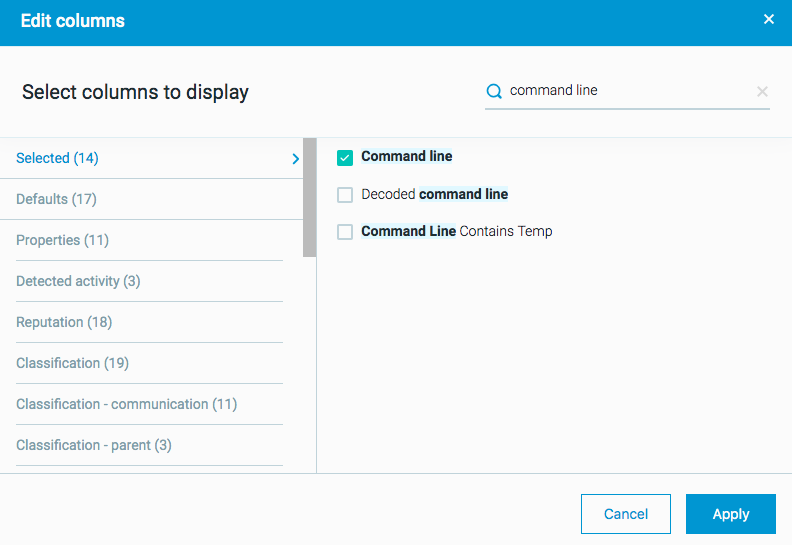
For Process Elements, there is a filter (Feature) to search for a specific command line. If you know of specific command line arguments used for code injection you can search for those: In addition, if you do not have a specific command line argument, you can return a list of all processes, and add the command line column to the results list in the Investigation screen. This enables you to see and analyze all command line arguments for all running processes: This method may be much more time-consuming so it is recommended that you research specific command line arguments relevant to your organization. Furthermore, the Element Details for each process report the command line details as part of the collected details. |
Search for instances of malicious tools |
The Cybereason platform contains detection rules about some malicious frameworks. |