Hunting Use-Case Example
In this example scenario, we will use search for evidence of internal reconnaissance. This behavior is part of the scanning part of the Attack lifecycle.
In this topic:
Step 1: Plan the goals of the hunt
Performing internal reconnaissance may include the following:
Discovery of information about hosts and their purposes (host enumeration)
Discovery of information about users, groups, and shares on a network (network enumeration)
Discovery of information about processes (process enumeration)
Scanning of the network to find addresses, ports, and so forth
Leaving artifacts that show evidence of host, network, or process enumeration
Performance of scanning activities outside normal business hours
Note this is not an exhaustive list of techniques used for internal reconnaissance.
In this hunt, we want to find evidence of host enumeration, network enumeration, process enumeration, or general network scanning.
Step 2: List your indicators of malicious behavior
Now that we know we want to find, we can list the indicators for which we want to search.
For each type of activity, there are different indicators to use.
Behavior |
Indicators |
|---|---|
Host enumeration |
Attackers can perform host enumeration with many commands. These differ between each operating system, but include:
This is not an exhaustive list of all commands, but these are commonly used. |
Network enumeration |
Like host enumeration, network enumeration uses some basic commands on each operating system:
|
Process enumeration |
Attackers also use commands for process enumeration, which differ on each operating system:
|
From these indicators, we can now explain exactly for what we want to search:
We want to find evidence of commands performing host enumeration.
We want to find evidence of commands performing network enumeration.
We want to find evidence of commands performing process enumeration.
We want to find evidence of processes performing network scanning.
We want to find evidence of user activity at irregular times of the day.
Step 3: Construct hunting queries
Use the statements above to construct queries.
Statement 1: We want to find evidence of commands performing host enumeration.
Because of our indicators of host enumeration use commands, we will use the Command line feature filter on the Process Element. This filter enables you to specify text used in the command line of a process and then search for this text.
Since the commands are different for Windows operating systems and Mac/Linux operating systems, we will need to run separate queries for the different operating systems. We add the Machine Element first to ensure that the query only returns results from a certain operating system.
You construct these queries:
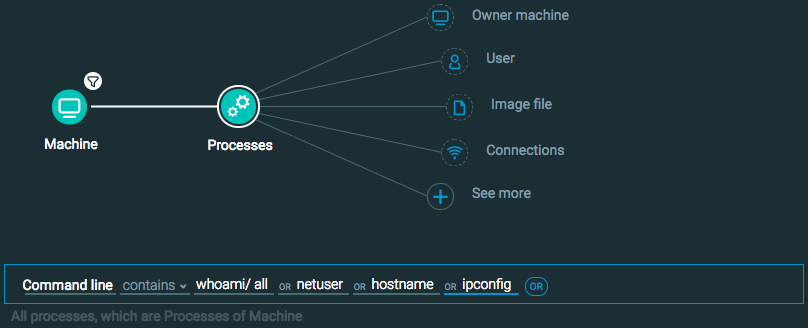
Machine Element -> Filter for OS Type is Windows THEN
Processes Element -> Filter for Command line contains whoami// all OR netuser OR hostname OR ipconfig
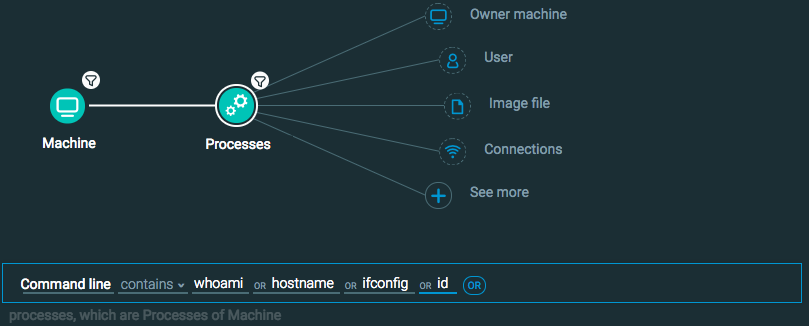
Machine Element -> Filter for OS Type is Mac OR Linux THEN
Processes Element -> Filter for Command line contains whoami OR hostname OR ifconfig OR id
Statement 2: We want to find evidence of commands performing network enumeration.
Like for statement one, our indicators are the use of certain commands. As a result, we will use the Command line feature on the Process Element. We will again need to run separate queries for the Windows operating systems and Mac/Linux operating systems.
You construct these queries:
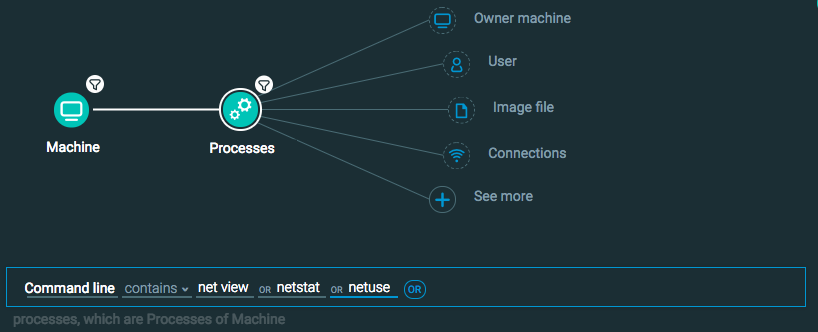
Machine Element -> Filter for OS Type is Windows THEN
Processes Element -> Filter for Command line contains net view OR netstat OR netuse
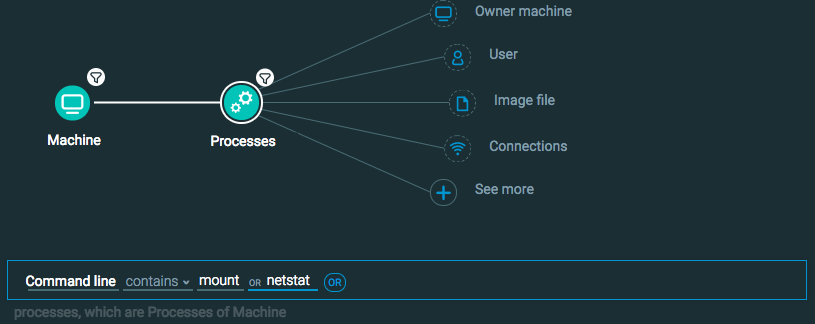
Machine Element -> Filter for OS Type is Mac OR Linux
Process Element -> Filter for Command line contains mount or netstat
Statement 3: We want to find evidence of commands performing process enumeration.
Like the first two statements, we are using commands as the indicator. We will use a similar query with the Command line feature filter on the Process Element with separate queries for Windows, Mac, and Linux.
You construct these queries:
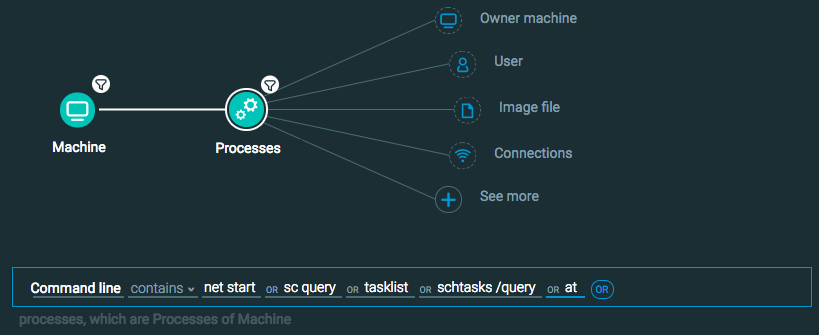
Machine Element -> Filter for OS Type is Windows THEN
Processes Element -> Filter for Command line contains net start OR sc query OR tasklist OR schtasks //query OR at
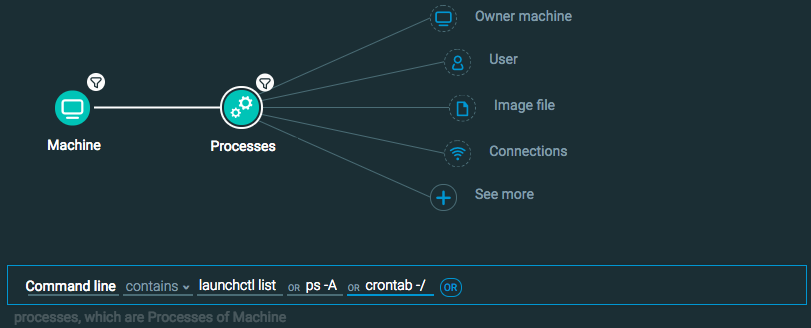
Machine Element -> Filter for OS Type is Mac THEN
Processes Element -> Filter for Command line contains launchctl list OR ps -A OR crontab -//
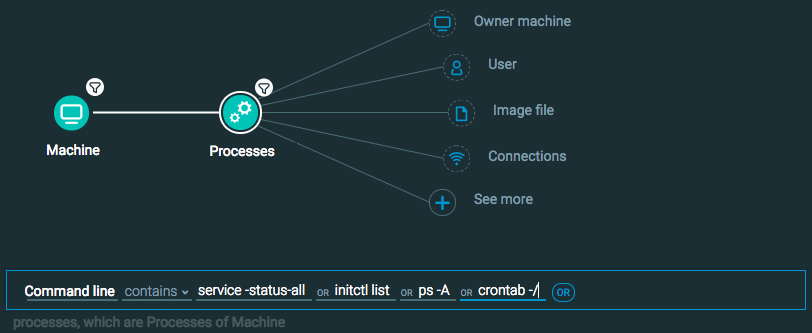
Machine Element -> Filter for OS Type is Linux THEN
Processes Element -> Filter for Command line contains service -status-all OR initctl list OR ps -A OR crontab -//
Statement 4: We want to find evidence of processes performing network scanning.
In this case, we have a detection rule for network scanners that will return any process thought to be performing activities classified as network scanning or possibly associated with network scanning.
You construct this query:
Process Element -> filter for Network Scanner is True
Statement 5: We want to find evidence of user activity at irregular times of the day
For this, we must look at users to see activity on their machines. On the User Element there is a filter for evidence on Irregular time of day activity.
You construct this query:
User Element -> filter for Irregular time of day activity is True
Step 4: Analyze your results
Now that you have the queries, you can run them. Analyze the results that have been returned to see if any evidence of internal reconnaissance is found.