Hunt with the Attack Tree
To assist analysts with hunting and investigation activities, Cybereason provides an interactive Attack Tree. The Attack Tree is a hunting tool that displays a specific process chain of execution from start to finish. The functionality provides better insight into malicious behavior, and helps narrow down large data sets to focus on processes with security relevance.
In this topic:
Attack Tree overview
The following graphic shows a typical Attack Tree for a process.
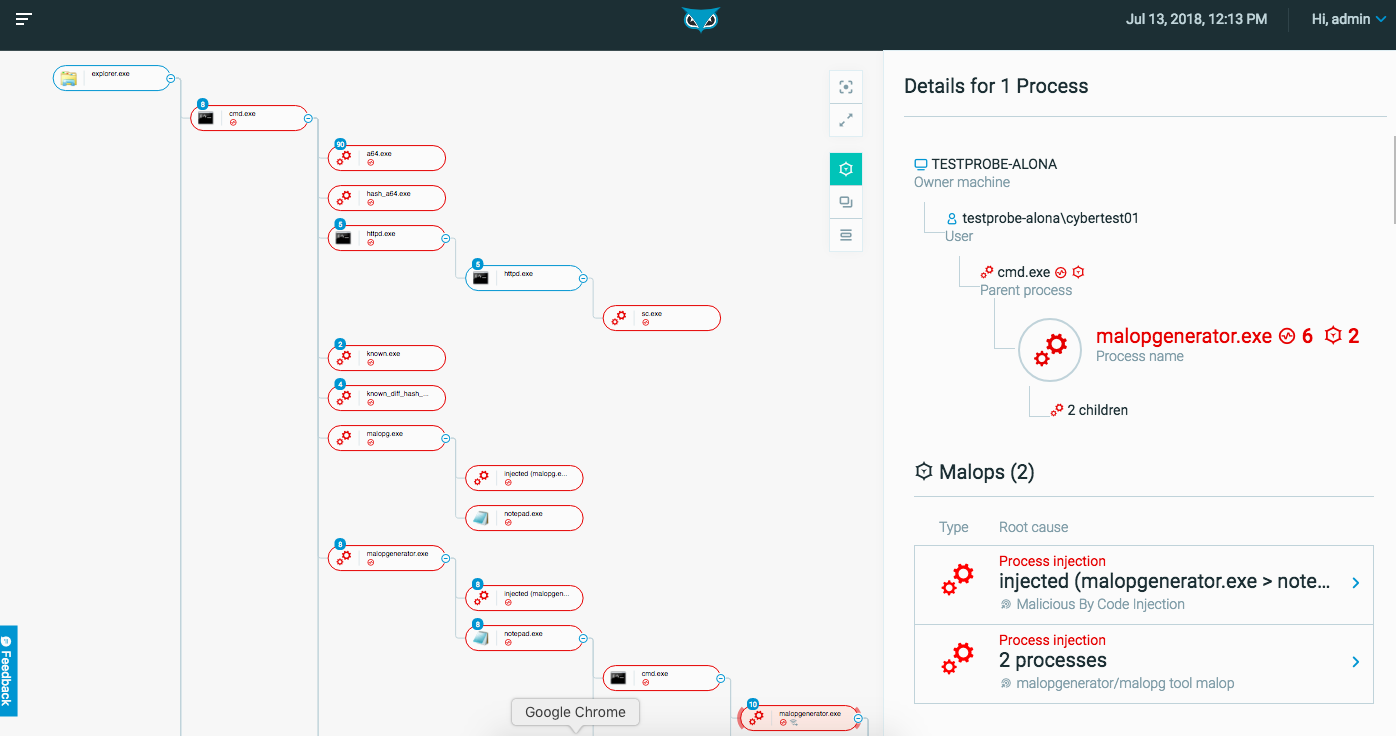
Analysts can use the Attack Tree to:
Understand what happened before and after a process was deemed malicious
Investigate what additional activity occurred in a suspicious execution chain
Quickly view all properties of every process in an execution chain
Gain contextual awareness for every process
Watch this video to learn how to use the Attack Tree.
Access the Attack Tree
You can access the Attack Tree for a process by clicking the attack tree icon ![]() in the following areas of the Cybereason UI:
in the following areas of the Cybereason UI:
The Investigation screen results table
The left side of the Malop details screen Process profile portion
From the list of processes displayed when you click a process in the Malop details screen
Viewing options
To help you navigate the Attack Tree, choose a viewing option from the top right of the Attack Tree screen.
Use the top two options to adjust the view of the tree within the UI:
Center selection: Adjust the view so the root process is in the center of the screen
Full screen: Toggle in and out of a full screen view
Use the lower three options to adjust the level of detail displayed in the tree:
Insight: Focuses on the Cybereason platform insights with regards to items in the specific execution tree. The Insight view displays the first process in the execution chain, all processes that Cybereason deemed suspicious or malicious, and their direct relatives (i.e. parent and child processes). Processes with the same name are grouped together for better viewing.
Aggregated: Provides a high-level view of the entire tree, including items displayed in the Insight view. Processes with the same name are grouped together for better viewing.
Full: Expands all processes that appear in the Aggregated view. Child processes remain collapsed for better viewing.
In all views, scroll to zoom in and out.
Elements of the Attack Tree
Each bubble in the Attack Tree represents a process, or a group of processes with the same name. Each process displays connections to its direct relatives (i.e. parent and child processes).
The process for which you chose to view the tree is highlighted and the details of the process are displayed on the right. Suspicious processes are outlined in red and appear higher in the tree than other processes. Subsequent top-to-bottom ordering is alphabetical by process name.
The following graphic describes a process bubble in greater detail.
Each process bubble contains:
The name of the process.
A plus or minus icon on the right of the process bubble to expand or collapse child process bubbles.
A suspicions icon
 indicating if the process is connected to one or more suspicions, and a MalOp icon
indicating if the process is connected to one or more suspicions, and a MalOp icon  if the process is associated with a MalOp.
if the process is associated with a MalOp.A number indicating how many processes are aggregated into that bubble.


