Perform a Hunt or Investigation
The Cybereason platform provides various intuitive screens you can use to hunt for malicious behavior or investigate behaviors the Cybereason platform has already deemed malicious. You do this by querying data collected by the sensors and stored in the in-memory graph.
In this topic:
Hunting and investigation tasks
You can hunt or investigate by performing one or more of the following tasks:
Investigate malware alerts by clicking Investigate from a malware alert in the Malware alerts screen.
Investigate a specific MalOp by clicking Investigate from the Processes tab in the Malop details screen.
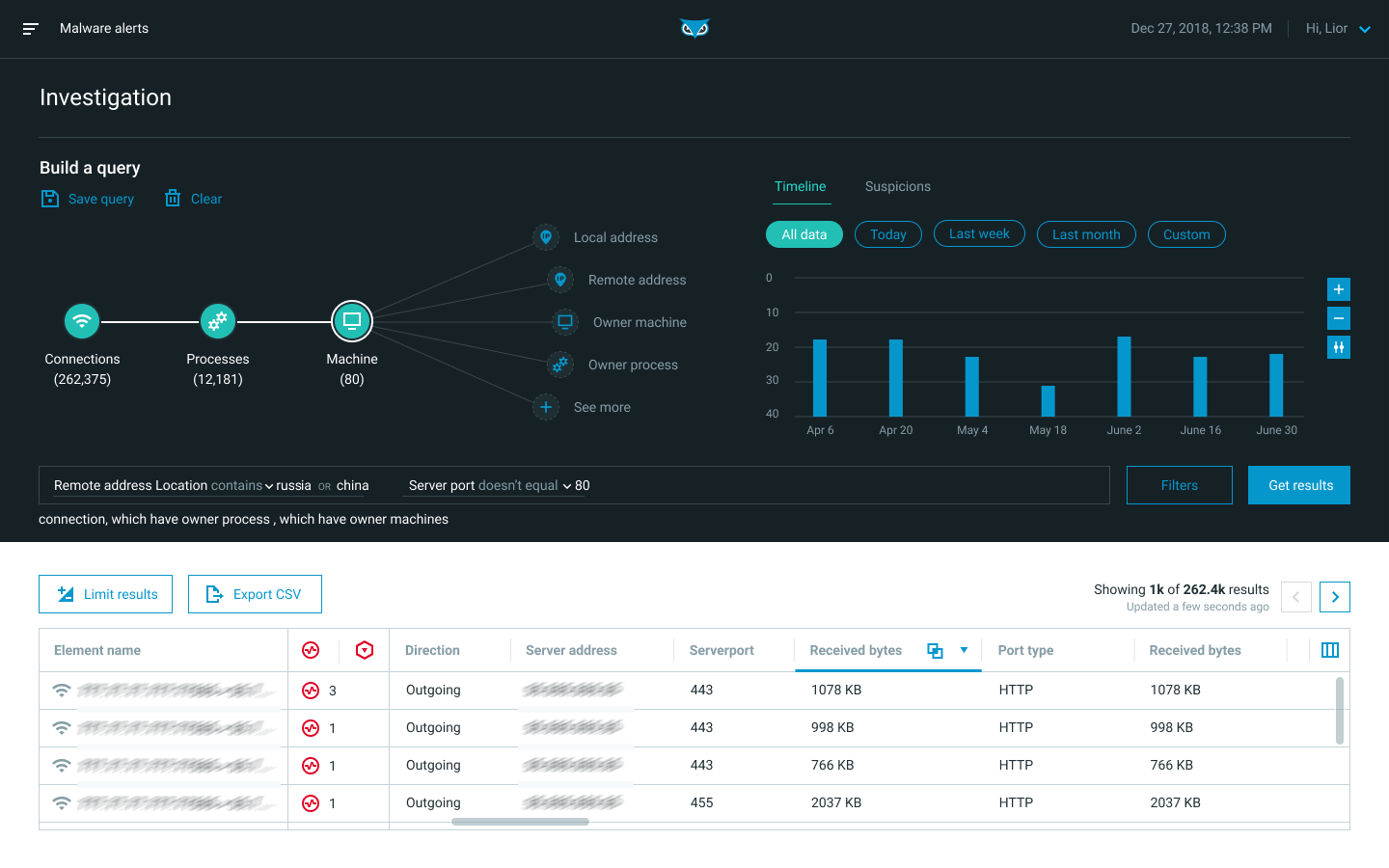
Build a Query from the Investigation screen, as shown in the image below. The Investigation screen lets you construct a query, inspect results in a grid view or timeline view, and dive into specific elements.
Hunt for indicators of malicious activity using the Hunt with the Attack Tree.
Search for Files on Machines from the (optional) Live File Search screen.
The Cybereason Investigation screen:
Begin your hunts and investigations
To start investigating, work through the Investigation Cycle.
To learn how to plan your hunt, read Plan a Hunt.
Hunting and Investigation components
Whatever method or methods you choose to employ when performing your hunts and investigations, you’ll be working with the following components:
Elements
Features
Elements identify components of your Cybereason platform, such as a machine, process, or user. Each Element has related Features that help you focus your investigation. For example, the Machine Element has a Feature called OS Version. See Elements and Features for more information.