Understand and Find Collected Data and Detected Activity
The Cybereason platform’s detection abilities are built on the “pyramid” approach, starting with the foundation of data (Facts) from the endpoint machines. The platform’s CMC Engine then analyzes and classifies these facts and triggers evidence, suspicions, and MalOps. For details on how data is used from the collection (fact) level to the MalOp, see Fact to MalOp.
After the Cybereason platform collects and correlates data collected from the sensors as well as from XDR log sources, the platform analyzes and correlates the data. Then, you can view collected data and detected evidence, suspicion, and MalOps.
The data is displayed differently, depending on whether the data is collected data (a property of an Element), and whether the data is a generated evidence, suspicion, or MalOp.
Watch the following video to see a discussion of collected data and detected activity:
In this topic:
Data collection to detection
Facts, or the data that the platform collects, include but are not limited to information about processes, files, machines, users, connections, or modules. For example, Facts may include properties such as the name of a process, file, or machine. Facts may also include information such as the connections that a process has opened, or the machine on which a process runs.
From the collected and analyzed data, based on a combination of behavioral analysis, classification, and proprietary detection rules, the Cybereason platform generates “detections”. These detections are visible in your Cybereason platform as evidence, suspicions, or MalOps.
The logic behind these detections combines some or all of the following:
Properties such as the name of a specific process
Classification, such as threat intelligence sources classifying a file as ransomware
Specific behaviors, such as a process opening connections to a malicious domain
View collected data
Data collected from sensors is telemetry data on the properties of items on a machine and data on what items are doing on the machine.
The Cybereason platform presents collected data as properties of an Element.
If the Element is associated with a MalOp, the Cybereason platform displays the associated data for that Element in different parts of the Malop Details screen:
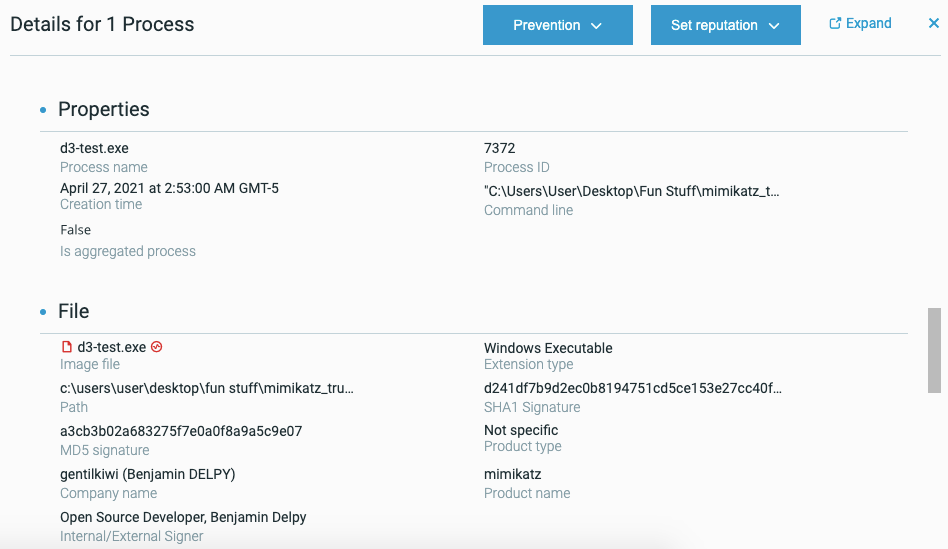
For example, here are some process details in a MalOp, including the command line, and times:
If the Element is not associated with a MalOp, you see the Element’s associated data in the Element Details screen when you run an investigation query:
Process name and ID
Process times
Command line for the process
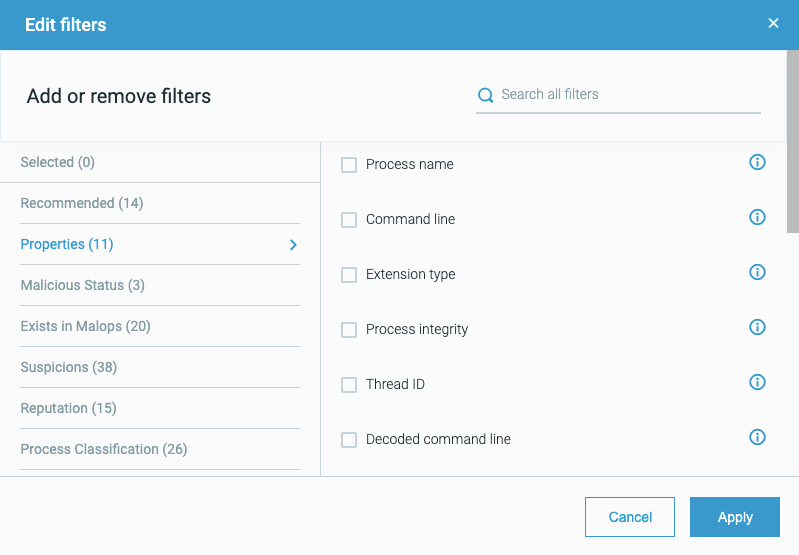
You can build an investigation query to report numerous pieces of collected data, using filters such as an Element’s properties:
For details on what data the Cybereason platform collects from a sensor, see Collected System-Level data. For a full list of all Elements and Features, see Query Elements and Features.
View and understand detected activity
The Cybereason platform reports detected activity, represented by evidence, suspicions, and Malops, in several ways.
MalOps
The Cybereason platform’s “operation-centric” view centers on MalOps, or “malicious operations”. MalOps represent a definite pattern of malicious activity that requires multiple conditions and behaviors. Requiring a pattern of behavior instead of one condition helps reduce the number of “false positive” MalOps that the platform generates.
MalOps are visible in the Malops management screen. From this screen, you can open the MalOp Details screen for each MalOp to view the evidence and suspicions that the Cybereason platform associates with that MalOp.
For example, this MalOp displays the evidence and suspicions that the platform detected directly in the Malop Details screen for that MalOp:
In the Malop Details screen, you can investigate each evidence and suspicion associated with the MalOp. You can also look for other items that have the same evidence and suspicions.
Additional suspicions and evidence
The Cybereason platform reports not just MalOps, which require multiple “events” or conditions to be present, but also potentially malicious individual activities.
To locate evidence and suspicions that are not related to a MalOp, you can build a query based on the Element for which the platform generated the evidence or suspicion.
The results return items that exhibit the same behavior as the evidence or suspicion.
If query results return multiple instances of items for a specific evidence or suspicion, or you see that the same evidence or suspicions occurs multiple times over a long period of time, you can create a custom detection rule that will generate a MalOp in your environment.