Endpoint Data Collection
Cybereason sensors collect data about the events and operations occurring on each endpoint throughout your organization to aid in identifying patterns of malicious behavior. The platform uses and analyzes this data to discover potentially or definite malicious behavior. Many of these data collections are available out-of-the-box without additional configuration, while other collections require additional configuration through Technical Support. For details on those collections not available by default, see Features Disabled by Default.
In this topic:
Data retention
By default, the Cybereason platform retains MalOp core data for one year and MalOp triage data for 30 days. MalOp core data includes the key points in the MalOp, visible in the Malops management screen. MalOp Triage includes all data related to the attack to empower security analysts to perform efficient triage and investigation and to enhance the attack scoping and quick remediation. MalOp Triage data includes the timeframe and Element relations, such as a Parent process, Child process, File events, and so forth.
In addition, to assist with data storage and availability for all collected events and operations, Cybereason offers multiple extended data retention packages for telemetry data (non-malicious data collected from endpoint sensors and sent to the Detection servers). Contact your Customer Success Manager to learn more about these data retention packages.
Collected System-Level data
Cybereason sensors collect the following system-level data:
Note
OS support varies for different system-level data collections are supported. For details on the supported operating systems for each collection, see Endpoint machine data collection features.
Data Type |
Description |
Information Collected |
|---|---|---|
Connections |
Any connection opened on a machine. |
|
DNS query (all types) |
Requests to a particular site or address to get the domain name. |
DNS queries can also be called Domain request and response. Collected information includes:
|
Drivers |
All drivers currently installed on the machine. |
|
Files |
Details about the file, its properties, internal details, and behavior. |
|
File events |
CREATE, RENAME, and DELETE operations on files. |
|
Hosts file |
Details translating IP addresses or domain names into other names on a specific machine. |
|
IP Address |
IP addresses for connections. |
|
IP Range Scans |
IP addresses retrieved from scan process. |
|
Listening Connection |
Any listening connection opened on a machine. |
|
Local Network |
Information on the local network |
|
Logon Sessions |
Details for logon sessions. |
|
Machine |
Machine details |
|
Modules |
All modules running on the machine. |
|
Mount Points |
Associated mount points. |
|
Network Interface |
Information on the network interface. |
|
Network Machine |
Information on the network machine. |
|
Processes |
Short-lived and long-lived process information. On Linux machines, these processes may display as aggregated processes. |
|
Proxy |
All proxies configured on the machine. |
|
Quarantine File |
The version of a file after it has been quarantined by the Cybereason platform. |
|
Registry Entry |
Specific registry keys associated with autoruns. |
|
Registry Events |
Specified registry keys that you select. |
|
Remote Logon Sessions |
Information on remote logon sessions. |
|
Remote Procedure Calls |
Information about select Remote Procedure Call (RPC) operations associated with the machine (in the MS-RPC Element. |
|
Scheduled Task |
Information on scheduled tasks. |
|
Scheduled Task Actions |
Information on scheduled task actions. |
|
Service |
All services currently running on a machine. |
|
Users |
Information on all users. |
|
WMI Activity |
Information on both local WMI activity and remote WMI activity. While this is information is collected separately from other Elements, the WMI activity is reported under Process activity details. |
|
WMI Persistent Objects |
Information on WMI persistent objects. |
|
The Cybereason platform collects data in all languages. The data is displayed according to the endpoint sensor OS language.
Note
Sensors do not collect the file content, or network packet information. Analysts can Search for Files on Machines to gain further insight into potentially malicious files.
Collected Active Directory data
Each sensor gathers the following Active Directory information for the machine and its users every 30 minutes:
User attributes:
SID
Display name
User principal name
Department
Company
Email
sAMAccountName
Primary GroupId
Member Of (multiple values)
Organizational Units (multiple values)
Country
Title
Created Time
Machine attributes:
SID
Description
Organizational Units (multiple values)
DNS Host Name
Location
Office
YOU can use the Investigation screen to search for specific Active Directory data. The following screen shot displays the User Element’s Active Directory filters.
Note
Not every Active Directory-related filter has the term ‘Active Directory’ in the title.
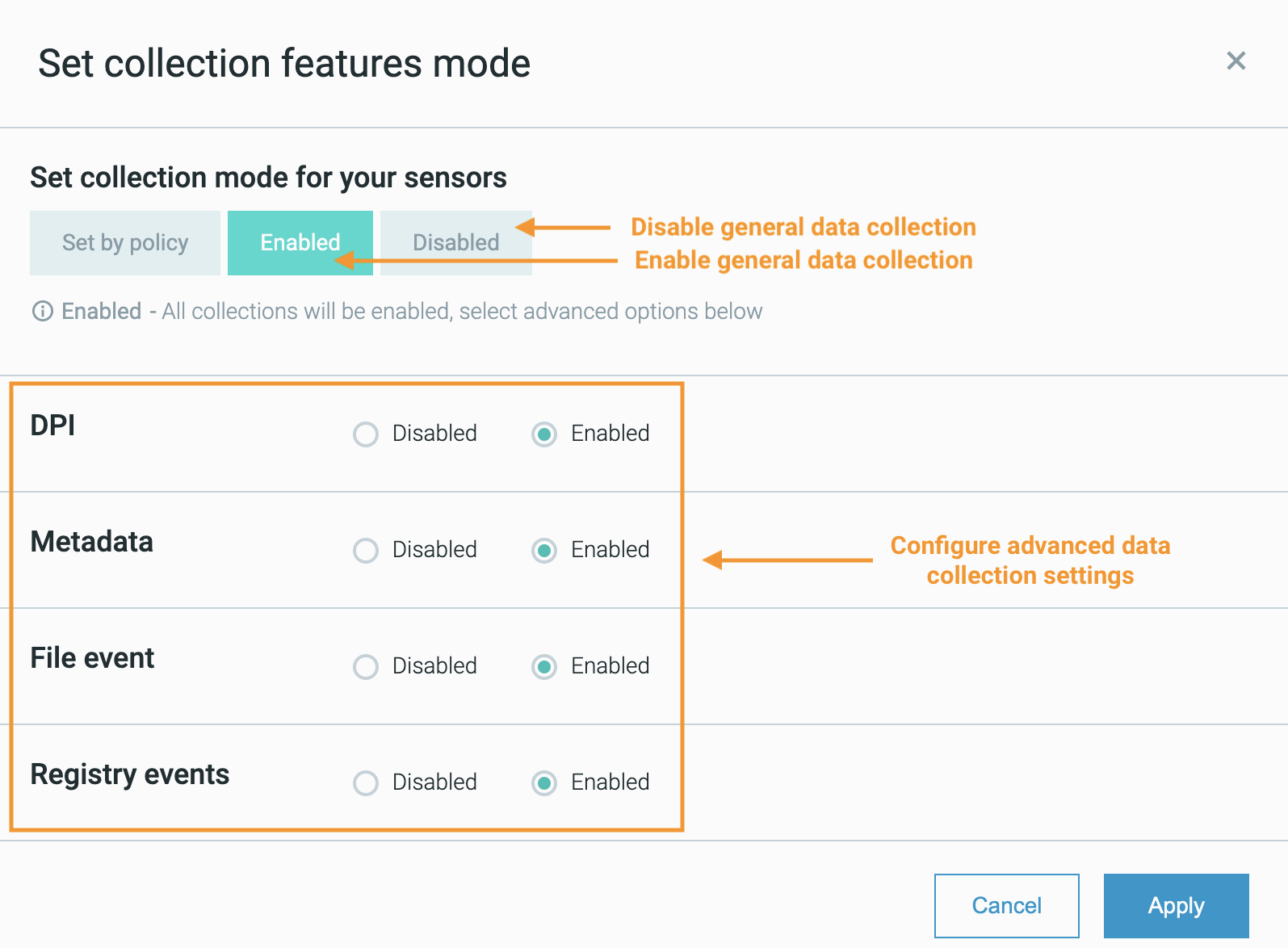
Enable or disable collections
You can enable or disable data collection processes at the sensor level from the System > Sensors screen:
Note
To enable or disable data collection, you must ensure that the sensor not assigned to a sensor group and does not have an assigned sensor policy to enable/disable data collection on that sensor.
Select the sensor or sensors whose data collection processes you want to enable or disable.
Click the Actions button.
Select Set Collection modes.
Select one of the following:
To specify that the selected sensors apply the data collection settings in their associated sensor security policies, select Set by policy.
To enable general data collection processes on the selected sensors, select Enabled
To disable general data collection processes on the selected sensors, select Disabled
If necessary, adjust the advanced data collection settings. See Configure Additional Endpoint Data Collections for information on advanced data collection options.
Click Apply.