Configure Additional Endpoint Data Collections
For specific types of endpoint data collection, In your sensor policy you configure settings for the following endpoint data collection features:
Non-executable file metadata collection
Registry event collection
File event collection
The visibility of these sections varies depending on the collection type and Cybereason sensor/server version:
File metadata |
Hidden by default. |
File events |
In versions 22.1.16X and earlier, this section is hidden by default. In versions 22.1.18X and later, this section is available.s |
Registry events |
In versions earlier than 22.1.14X, this section is hidden by default. In versions 22.1.14X and later, this section is available. |
To make these sections available in the sensor policy, open a Technical Support case.
Changes to these options in the sensor policy and the addition of file event exclusions are noted in the syslog.
In this topic:
Enable non-executable file metadata collection
By default, the Cybereason platform collects file metadata information about executable files to help analyze those files for malicious activity. In addition, you can enable the sensor to collect file metadata for other types of files, including Word files, Excel files, PowerPoint files, Adobe Acrobat files, and PowerShell scripts.
To enable file metadata collection, follow these steps:
In your sensor policy, navigate to the Collection features screen.
In the Collection features screen, locate the Non-executable file data collection section and set the toggle to On.
Select the file types you want:
Word documents (.doc, .dom, .dot, and .rtf types)
Excel spreadsheets (.xls, .xltm, .and .csv types)
PowerPoint files (.ppt types)
Adobe Acrobat files (.pdf types)
PowerShell scripts (.ps types)
Enable registry event collection and add inclusions
Because attackers and attack techniques often modify the registry, the Cybereason platform can collect details about registry key creation, deletion, and modification events for specified registry keys. You use this data to enrich other data collected by the Cybereason platform to uncover evidence of a potential attack.
When you use registry event collection, you should understand the following terminology:
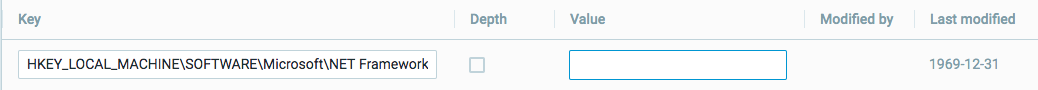
A registry key is the higher level ‘folder’ that contains registry values. For example, a registry key could be HKLM\Software\Microsoft\Windows\CurrentVersions\RunOnce. Registry keys can contain other keys.
A registry value is a ‘file’ under the higher level key. This is a specific entry under the registry key.
The registry path is the combination of the registry key and value.
To enable and configure registry collection, follow these steps:
In your sensor policy, navigate to the Collection features screen.
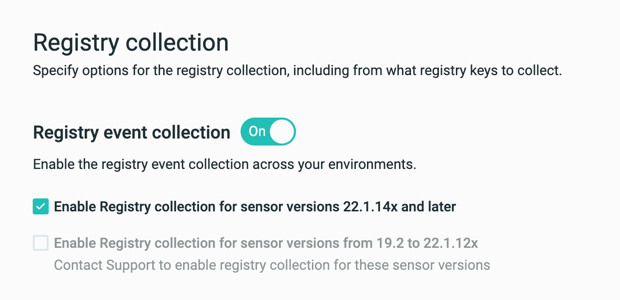
In the Collection features screen, locate the Registry collection section and set the toggle to On.
If you have sensors running versions 22.1.149 and later, select the Enable Registry collection for sensor versions 22.1.14X and later option.
If you have sensors running versions earlier than 22.1.149, select the Enable registry collection for sensor versions from 19.2 to 22.1.12X option.
Note
If you are upgrading your Cybereason environment to version 22.1.149 and later, this option is visible only if you previously enabled Registry Events collection. If you did not have the Registry Events collection section enabled previously, open a Technical Support case.
After you enable the registry events collection, by default, the inclusions grid contains a number of registry keys that relate to autoruns. These registry keys are the default values for registry event collection.
You can keep the existing keys, exclude all keys, or add your own registry keys to collect:
To keep the existing keys, make sure you do not delete the existing registry keys in the grid.
To exclude all registry keys, enter a non-existent registry key path in the grid. The non-existent registry key ensures that the platform does not automatically repopulate the grid with the default system registry keys for collection. If you leave the grid blank, the platform will repopulate these keys.
To restore the default system registry keys automatically, leave the grid completely empty.
In the Add registry key inclusions section, click Add new.
You can add up to 250 registry key inclusions (including the default entries that your Cybereason platform includes).
In the grid, add the registry key to include. The entered key has a maximum length of 200 characters.
When adding a registry key, you must enter the full explicit path to the key. The use of wildcards in registry key paths is not supported.
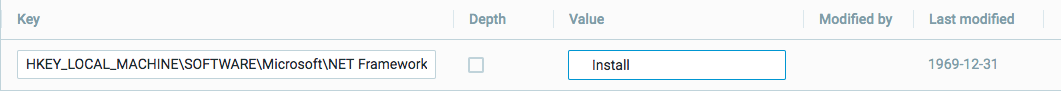
Optionally, to limit the key collection to specific values, in the Value box, enter the values to collect. You can enter up to 5 values.
If you enter multiple values, press the ENTER key after each entry. When you save all your changes, the grid displays these values as a comma-separated list.
If you do not enter values, all values are collected for the specified registry key.
Optionally, to search for a specific value in all keys and subkeys of the specified key, select the Depth checkbox and enter the values in the Value box.
Click the checkmark option to save your changes.
Watch this video to learn more about Registry events collection.
Registry collection inclusion examples
The table below includes examples for creating inclusions:
Outcome |
Procedure |
Example Result |
|---|---|---|
Collect a key and all values |
Add a key but do not add any values. In the Key column, enter the registry key path. Leave the Value column empty. |
|
Collect only a single value |
You add a key and a single value.
|
|
Collect a key and multiple values |
Add a key and the specific values.
|
In the example, note that one of the values set in the Value field is not collected - this is not a valid value for that registry key and was ignored. |
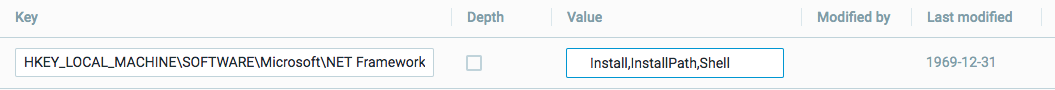
Collect specific values from subkeys |
You add a key, select the Depth option and enter specific values: |
Enable file event collection and add exclusions
The sensor can collect details on file events for specific types of files related to security needs. The sensor collects details when a file is created, renamed or deleted.
To enable the file event collection, follow these steps:
In your sensor policy, navigate to the Collection features screen.
In the Collection features screen, navigate to the File collection section and set the toggle to On.
If you have sensors running versions 22.1.18X and later, select the Enable collection for sensor versions 22.1.18X and later option.
If you have sensors running versions 22.1.16X and earlier, select the Enable collection for sensor versions 22.1.16X and earlier option.
Note
If you are upgrading your Cybereason environment to version 22.1.18X and later, this option is visible only if you previously enabled File events collection. If you did not have the File Events collection section enabled previously, open a Technical Support case.
As needed, in the File event exclusion grids, click Add New and enter the relevant details to add exclusions to not collect any events:
Cybereason recommends that you exclude known legitimate browsers or anti-virus programs because file events from such programs produce a large amount of data.
Process name: The exact process name. To exclude all events that a process initiates, enter the exact name of the process, such as chrome.exe.
The process name must match the name in the exclusion exactly. If the names only partially match, the exclusion does not take effect.
File or folder path: The path to a folder or file to exclude. To exclude events that an item in a folder or file initiate, specify the path to the folder or file, such as C:\Windows\System32\drivers\ or C:\Windows\System32\drivers\driver.dll. This excludes events initiated by items in the folder or the file.
This match is applied against any path that contains the specified path. If there are other paths or subdirectories/folders in the specified exclusion path, the exclusion takes effect on these paths and files also.
Process name and path: A path and a process on that path. To exclude a specific process in a specific path, specify both the path and the process name.
Exclusions apply to all file events, including create, delete, and move/rename events as well as file metadata collection.
Note
Exclusions do not support wildcard characters or the asterisk character.
Watch a video demo of file events collection:
File event collection exclusion examples
The table below includes a number of examples for creating exclusions:
Process name |
Path |
Description |
|---|---|---|
chrome.exe |
Any event initiated by Chrome.exe across the environment will not be collected. |
|
C:\Users\User1 |
Any event associated with this path by any process will not be collected. |
|
chrome.exe |
C:\UsersUser1\Downloads |
Any event initiated by chrome.exe on a file in the Downloads folder will not be collected. |
chrome.exe |
Downloads |
Any event initiated by chrome.exe on a file in the Downloads folder of any user will not be collected. |
chrome.exe |
C:\Users\User1Downloads\myfile.docx |
Any event initiated by chrome.exe on myfile.docx in this specific pah will not be collected. |
chrome.exe |
Downloads\myfile.docx |
Any event initiated by chrome.exe on myfile.docx in the Downloads folder of any given user will not be collected. |
Chrome |
No exclusion added |
|
C |
Any event initiated by any process on a file or folder containing the letter C will not be colledted. Cybereason recommends not using this type of exclusion. |
|
C:\ |
Any event initiated by any process on a file or folder under the C:\ drive across the environment will not be collected. |
|
.exe |
Any event initiated by any process on any .exe file across the environment will not be collected. |
|
.doc |
Any event initiated by any process on a file containing this extension (including .docx, .docm, etc.) will not be collected across the environment. |