Set the Fileless Protection Modes
The Cybereason platform’s Fileless protection feature enables you to stop and detect the malicious use of fileless attacks, including:
Detect and prevent download commands and the execution of malicious content
Examine PowerShell scripts to identify malicious code
Detect and prevent payloads from .NET floating modules
Detect and prevent .NET to JScript attacks
Detect and prevent attacks using the AMSI module, including from Jscript, VBScript, WMI, Office macros and more
For supported operating systems for Fileless protection, see Endpoint machine prevention features.
In this topic:
Enable Fileless protection
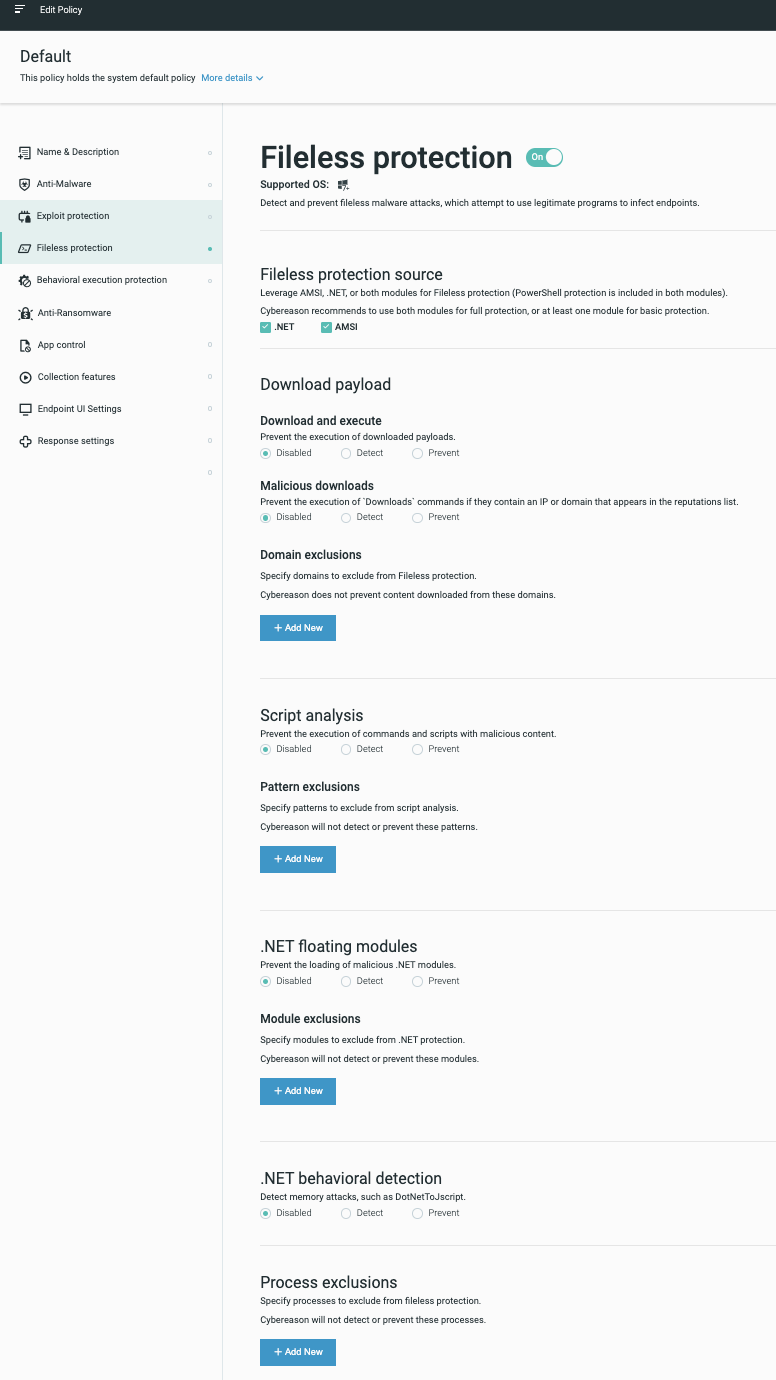
In your sensor policy, navigate to the Fileless protection screen and set the toggle to On.
Select the Fileless protection module
To help you better tailor your Fileless protection options, the Cybereason platform uses both the AMSI and .NET modules, which allow you to choose the type of protection suitable for your organization. Select the AMSI checkbox, .NET checkbox, or both checkboxes.
Note
Cybereason recommends that you use both modules for full protection, or at least one module for basic protection.
When you select a checkbox for a module, you instruct Fileless protection to protect your environment from attacks launched by specific programs and frameworks relevant to that module. Each module includes PowerShell protection. For more information about the frameworks and programs that each module protects, see Protected frameworks and programs.
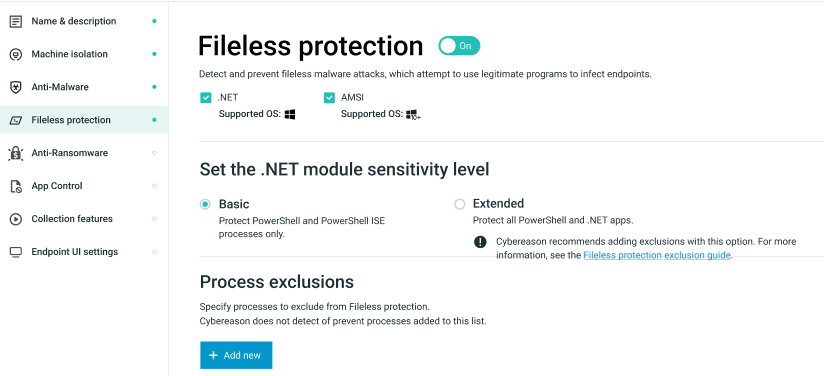
Select the .NET module sensitivity level
Note
This feature is available in versions 23.1.8x and later. Sensors prior to version 23.1.8x will function on Extended mode only.
Select the sensitivity level for the .NET module, as follows:
Mode |
Description |
When to use this setting |
|---|---|---|
Basic |
Select this mode to protect PowerShell and PowerShell ISE processes only, as these processes provide the most security value and the highest security risk. |
When first enabling Fileless protection, Cybereason recommends the following workflow:
|
Extended |
Select this mode to protect all PowerShell and .NET apps, except for those you excluded. |
You want to detect and prevent all processes. Note: Cybereason recommends adding relevant exclusions when selecting this option. |
Detect and prevent download commands and content execution
With Fileless protection, you can analyze activity for specific malicious use of patterns around script download commands.
To detect and prevent download commands and content execution, follow these steps:
In the Fileless protection screen, navigate to the Download payload section.
In the Download payload > Download and execute section, define whether the Cybereason platform should detect or prevent downloaded payloads:
Disabled
Detect: Detect the sequence of download commands but does not prevent the command execution
Prevent (recommended): Detect and prevent the download commands
In the Malicious downloads section, select the option that you want:
Disabled
Detect: Detect the execution of Download commands if they contain an IP or domain that appears in the reputations list.
Prevent (recommended): Detect and prevent the execution of Download commands if they contain an IP or domain that appears in the reputations list.
Analyze scripts
Fileless protection can analyze scripts for potentially malicious activity, including malicious patterns of text or code.
To configure script analysis, follow these steps:
In the Fileless protection screen, navigate to the Script analysis section.
In the Script analysis section, define whether the Cybereason platform should detect or prevent malicious patterns of text or code in various scripts:
Disabled
Detect: Detect malicious commands and scripts but do not prevent script execution
Prevent (recommended): Detect and prevent malicious commands and scripts
Protect against floating module payloads
With Fileless protection, you can prevent floating modules from loading their payloads.
To detect and prevent floating module payloads, follow these steps:
In the Fileless protection screen, navigate to the .NET floating modules section, and then select the appropriate option to prevent the load of malicious floating .NET modules:
Disabled
Detect: Detect the payload that a malicious floating module includes, but do not prevent the payload from running
Prevent (recommended): Detect and prevent payloads in floating modules
Below the .NET floating modules section, navigate to the .NET Behavioral detection section.
In the .NET Behavioral detection section, select the appropriate option prevent .NET to JScript attacks. These attacks use serialization to bypass antivirus tools and run code from memory:
Disabled
Detect: Detect .NET to JScript attacks, but do not prevent the attacks.
Prevent (recommended): Detect and prevent .NET to JScript attacks