Add Exclusions from NGAV Protection (Legacy)
Note
In versions 23.2.65 and later, sensor policy exclusions can be managed in the Policy exclusions screen. Contact your Customer Success Manager to gain access to this feature.
In some cases, different parts of your sensor policy configurations may result in false results or prevent some of your legitimate programs from operating successfully.
To help with these cases, you can add exclusions for specific items in the sensor policy. For example, you can exclude folder paths from Anti-Malware scans, or exclude domain names from analysis by Fileless protection.
Note
If an item (e.g. a file hash) is added to the Custom Reputations allowlist, NGAV features will not detect or prevent this item, even if this item does not appear on that feature’s exclusions list.
Note
If an item is on an NGAV feature’s exclusion list, but it does not exist on the Custom Reputations allowlist, it will not be prevented, but it may trigger a MalOp. To stop it from triggering a MalOp it should also be added to the allowlist. For details on how to use the allowlist, see Manage Reputations.
In this topic:
Exclude files and paths from Anti-Malware
If you find that Anti-Malware continues to generate false positive detections for a specific folder or file or cause performance problems on your machine, you can add an exclusion for a specific file or folder.
To add an Anti-Malware exclusion, follow these steps:
In your sensor policy, navigate to the Anti-Malware screen.
In the Anti-Malware screen, locate the Exclusions section.
In the Exclusions section, under Exclude path or file, click Add New.
In the File/folder name column, type the path to the file or folder.
You can also use wildcard characters or environment variables:
Method
Details
Wildcards
You can use the following wildcard characters:
Asterisk (*): When used in a path, the asterisk can match any amount of characters and any value. For example, *:/folder can match dijorgidrg:/folder or C:\folder.
When using wildcard characters, Cybereason recommends using file or folder names that are as complete as possible. For example, adding a exclusion with *.docx or *scriptname.ps1 will exclude the file. Using a format like xxxx-*-yyyy, myfile*.docx, *-yyyy, file_* will not exclude the file or folder.
Note
Previous versions of the documentation used double asterisks (**) in a wildcard example. Using a double asterisk is still valid, however using a single asterisk accomplishes the same task.
Question mark (?): Can match one character and any value. For example, ?:/folder can match C:\folder or D:\folder.
Important
Cybereason does not recommend the use of file extension wildcards to exclude all files under a file extension (such as *.exe) as this may expose your system to attacks or breaches. In addition, using file extension wildcards might affect performance. Cybereason recommends to exclude specific folders instead of using file extension wildcards as shown in the following example.
Environment variables
On Windows endpoints only, you can use environment variables in file and folder exclusions.
For example, the following exclusion excludes the file.exe file and uses the %ALLUSERSPROFILE% variable to specify the user profile folder on all machines.
%ALLUSERSPROFILE%\CustomLogFiles\file.exe
In this example, %ALLUSERSPROFILE%\CustomLogFiles indicates the %PROFILESFOLDER%\Public or %PROFILESFOLDER%\all users folder.
For more information on environment variables, see the Microsoft documentation.
Note
You cannot add forward slashes and backslashes in the same exclusion.
Click the checkmark (✓) to save the exclusion.
Click Save and Publish.
Exclude processes from Anti-Malware
The Cybereason platform excludes a predefined list of trusted processes that are commonly used by compilers, integrated developer environments (IDEs), security products, and so on. These exclusions improve performance in scenarios where legitimate tools or products trigger multiple alerts. The Cybereason platform excludes these processes by default, and no additional action is required.
In addition, you can exclude a specific process from Anti-Malware scans. This capability is not generally available. To enable and use this capability, contact your Customer Success Manager.
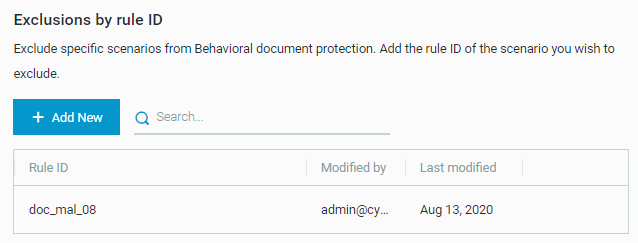
Exclude Behavioral document protection using a rule ID
When Behavioral document protection analyzes a document, the Cybereason platform triggers rules that indicate whether any malicious content was found. For example, the doc_mal_08 rule indicates that the Cybereason platform detected malware in a document. Each rule includes information on a very specific use-case that may apply to several files. Alternatively, the same file may trigger several rules.
With Behavioral document protection rule exclusions, you specify rule IDs to disable Behavioral document protection in the specific scenario indicated by the rule.
For example, a document named GeneralCompany_Salaries_2020.xlsx triggered two rules:
doc_mal_08, which indicates that the Cybereason platform detected malware in the file.
doc_obf_23, which indicates that the Cybereason platform detected an obfuscated macro in the file.
If you add both of the rule IDs in the Exclude behavioral document rule ID area, Behavioral document protection ignores these specific scenarios or behaviors for the GeneralCompany_Salaries_2020.xlsx document and for other documents with similar behaviors. Behavioral document protection may analyze this or similar documents in the future, but the code that was previously found malicious is now ignored.
Note
When your organization begins using Behavioral document protection, we recommend to initially set Behavioral document protection to Detect, and then retrieve all of the rule IDs for the rules triggered in your environment. You can then use the rule exclusions to indicate which files are trusted and reduce false positives.
To add an exclusion for a rule ID, follow these steps:
From in your sensor policy, in the nti-Malware screen, find the Behavioral document protection section.
In the Behavioral document protection section, in the Exclude behavioral document rule ID area, click Add New.
A new row is added to the table.
In the Rule ID field, type the rule ID.
To retrieve the rule ID, in the relevant Malop, click the Document evidence, and locate the Properties > Detection value field. For example, the Detection value field displays the [“doc_aut_09”,”doc_obf_15”] value, where the rule IDs are doc_aut_09 and doc_obf_15.
To save, click the check mark (✓). To cancel, click x.
The Modified by and Last modified fields display the user name and date for this rule.
To add more rule IDs, repeat steps 1-2 for each additional rule.
Exclude behavior ID from Behavioral Document Protection
You can add exclusions for Behavioral document protection using the behavior ID displayed in the MalOp. The behavior ID is a SHA-256 hash value.
To add an exclusion for a behavioral ID, follow these steps:
In your sensor policy, navigate to the Anti-Malware screen.
In the Anti-Malware screen, find the Behavioral document protection section.
In the Behavioral document protection section, in the Exclusions by behavior ID table, click Add New.
Add the Behavior ID you wish to exclude. Optionally, add a Comment.
Click the checkmark (✓) to save the exclusion.
Click Save and Publish.
Exclude paths from Fileless Protection
To add a process exclusion by path, follow these steps:
In your sensor policy, navigate to the Fileless Protection screen.
In the Fileless Protection screen, navigate to the Process exclusions section.
In the Process exclusions table, click Add New.
In the Process/Path to process column, do one of the following:
Type the name of the process including the file extension, for example: processname.exe.
Enter the path to the process. You must include the path: prefix, for example: path:c:\temp\file.exe.
The path exclusions can be regex-based. See the example below:
Regular expression:
c:\john\.*\doe.exe
Test string:
c:\john\example\doe.exe
Note
It is recommended to validate your regex using a regex validator.
Click the checkmark (✓) to save the exclusion.
Click Save and Publish.
Exclude domains from Fileless Protection
If a legitimate PowerShell activity needs to access certain domains, you can add exceptions for these domains.
To add a domain exclusion, do the following:
In your sensor policy, navigate to the Fileless protection screen.
In the Fileless protection screen, locate the Domain exclusions section.
In the Domain exclusions section, click Add New.
In the URL/Domain column, enter the domain name.
Important
The Cybereason platform currently supports exclusions for domains only, and not for full URLs. For example, exclude the domain s3.amazonaws.com and not the full URL http://s3.amazonaws.com/example/example. If you type a full URL, the Cybereason platform does not apply the exclusion.
Exclude detection patterns from Fileless protection
If Fileless protection blocks a legitimate command as part of script analysis, you can add a pattern exclusion to prevent this problem.
You can find the detected pattern to exclude in the Malicious command alert in the Malware alerts screen, or in the Pattern field in the MalOp details screen.
To add a pattern exclusion, follow these steps:
In your sensor policy, navigate to the Fileless protection screen.
In the Fileless protection screen, locate the Script analysis section.
In the Script analysis section, locate the Pattern exclusions option.
Above the grid, click Add New.
In the Pattern name column, enter the pattern to exclude.
Click the checkmark icon to save the exclusion.
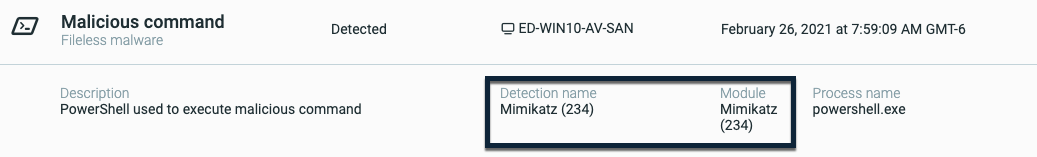
Exclude modules from .NET protection
If the Cybereason platform is raising false-positive alerts for those modules or namespaces you identified as non-malicious, you can exclude the module or namespace.
To add a module exclusion, follow these steps:
In the Malops management screen, locate a Malicious use of PowerShell Malop
Open the Details screen for that MalOp.
In the Details screen, click the Loaded modules field and locate the name of the module.
For example, the name of the module might be program.inception.
In your sensor policy, navigate to the Fileless protection screen.
In the Fileless protection screen, locate the Module exclusions section.
In the Module exclusions section, above the grid, click Add New.
Enter the module to exclude, for example, program.inception.
Click the checkmark (✓) to save.
Exclude processes from Fileless protection with regular expressions
We recommend using this feature primarily to exclude PowerShell commands and not the PowerShell process (since PowerShell is usually only the enabler and not the actual malicious process).
To add a regular expression process exclusion, follow these steps:
In your sensor policy, navigate to the Fileless protection screen.
In the Fileless protection screen, locate the Process exclusions section.
Above the grid, click Add New.
In the Process name column, add the regular expression exclusion or regular expression pattern exclusion.
Your exclusion must be at least five characters long.
To add an exclusion for a script named unnamed_arguments_example_3.ps1, you add the exclusion rgx:unnamed_arguments_example_3.ps1.
Likewise, to add a regular exclusion pattern exclusion for a process named internatltool_v107.exe, you add rgx:(InternalTool_v)*(.exe*). This format enables the exclusion to apply to other versions of the tool.
Note
Ensure that you use specific values (process name, script, etc.) and not common values to ensure that only the specific process is excluded.
Click tbe checkmark (✓) to save the exclusion.
The rgx: exclusions analysis is applied at the beginning of the command line for the first 250 characters.
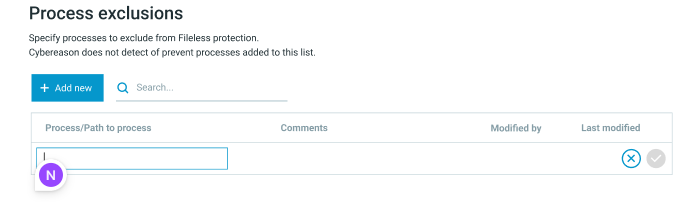
Exclude processes from Fileless protection
If Fileless protection reports a process as malicious, but you know that the activity is non-malicious, you can add an exclusion for the process.
To add a process exclusion, follow these steps:
In your sensor policy, navigate to the Fileless protection screen.
In the Fileless protection screen, locate the Process exclusions section.
In the Process exclusions section, above the grid, click Add New.
In the Process name column, type the name of the process including the file extension, for example: processname.exe.
Click the checkmark (✓) to save the exclusion.
Exclude processes or paths from Behavioral execution protection
If Behavioral execution protection or Variant payload prevention prevents a legitimate process or processes under a specific folder, you can add an exclusion for that process or folder.
To add a process or path exclusion, follow these steps:
In your sensor policy, navigate to the Behavioral execution protection screen.
In the Behavioral execution protection screen, locate and expand the Exclude process or path section.
Click Add New.
In the File/folder name column, enter one of the following:
The process name to exclude, for example: processname.exe.
The full path to the process to exclude, for example: C:\ExampleFolder\processname.exe.
The path to the folder under which you want to exclude all processes, for example: C:\ExampleFolder.
Note
The process name and folder path exclusions are not case-sensitive.
Click the check mark (✓) to save the exclusion.
Note
To obtain the process name or path, copy the process name or locate and copy the path to the relevant process. The Command line field in the Malop might not include the process name and should not be used for exclusions.
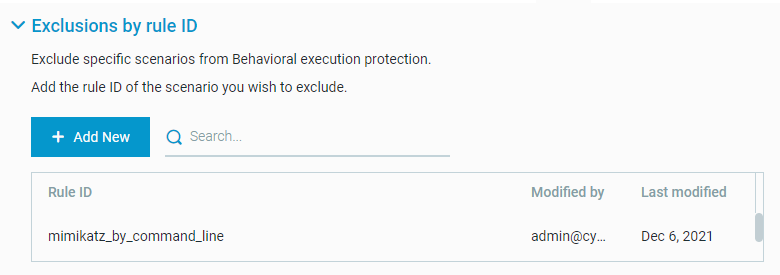
Exclusions by rule ID for Behavioral execution protection
If a specific rule is causing false positive alerts for you, add an exclusion for this rule ID>
To add an exclusion for a rule ID, follow these steps:
To find the ID for the rule you want to exclude, do one of the following:
Locate the relevant Malicious process behavior MalOp, and in the Malop details screen, copy the rule ID from the Signature field.
Select and copy the relevant rule ID from the Rule IDs and descriptions section.
In the sensor policy, in the Behavioral execution prevention section, in the Exclusions by rule ID area, click Add New.
A new row is added to the table.
In the Rule ID field, type the rule ID.
Click the check mark (✓) to save the rule.
The Modified by and Last modified fields display the user name and date for this rule.
To add more rule IDs, repeat steps 1-3 for each additional rule.
You can also delete ( ) or search rule IDs. To search rule IDs, type the rule ID in the search box and press ENTER.
) or search rule IDs. To search rule IDs, type the rule ID in the search box and press ENTER.
Behavioral execution prevention includes the following rule IDs:
Rule ID |
Description |
|---|---|
accessibility_features |
Behavioral execution prevention detected an attempt to use accessibility features for persistence. |
cmstp_abnormal_execution |
Behavioral execution prevention detected an attempt to use the CMSTP.exe utility process for malicious purposes. |
fileless_mshta_rundll32 |
Behavioral execution prevention detected an attempt to execute a fileless script with the MSHTA.exe or RunDLL32.exe utilities. |
lolbin_credential_dump_reg |
Behavioral execution prevention detected an attempt to use reg.exe for credential dump activity. |
mimikatz_by_command_line |
Behavioral execution prevention detected an attempt to execute the mimikatz script. |
msexchange_owapool_webshell |
Behavioral execution prevention detected an attempt to exploit the Microsoft Exchange application pool (MSExchangeOWAAppPool). |
Exclude commands from Anti-Ransomware/Predictive Ransomware protection
Note
This section is relevant to the Anti-Ransomware screen and the Predictive ransomware protection screen. To learn which ransomware protection type to use according to your sensor version, see Ransomware protection types per version.
Sometimes, if the Cybereason platform blocks the use of legitimate programs or commands, you can exclude legitimate files or commands from Anti-Ransomware or Predictive Ransomware protection.
To add an command exclusion, follow these steps:
In your sensor policy, navigate to the Anti-Ransomware or Predictive ransomware protection screen
In the Anti-Ransomware/Predictive Ransomware protection screen, locate the Exclusions section.
In the Exclusions section, above the grid, click Add New.
In the Command column, enter the command name and an optional description.
The command name must include the exact command line syntax. For example: “C:\Users\12345\AppData\Local\Microsoft\OneDrive\OneDrive.exe” /background.
Note
From version 23.2.44 and later, you can use Regex-based expressions for the command name.
To find the command line syntax, locate the MalOp that was triggered by your legitimate files or commands, and from the Processes tab, click Investigate.
Then, in the query results, the command line syntax is visible in the Command line column for each of the suspicious processes.
Click the checkmark (✓) to save the exclusion.
Exclude processes from Exploit protection
If you have enabled Exploit protection, you can add an Exploit protection exclusion to instruct the Cybereason platform not to apply mitigations to the process. The Cybereason platform then does not detect or block exploit attempts for the excluded process.
You cannot add Exploit protection exclusions if you are using the Existing endpoint configuration mode. The Process exclusions area is grayed out unless you select either the Cautious (OS recommended) or the Aggressive (Cybereason recommended) mode.
Important
Exploit protection exclusions are relevant in cases where Exploit protection blocks a legitimate process or the process otherwise incorrectly triggers Exploit protection due to unexpected behavior. However, excluding a process might expose the process to potential attacks. Before you exclude a process because the process seems to be functioning incorrectly when Exploit protection is enabled, make sure that the process is not under attack.
To add a new Exploit protection exclusion, follow these steps:
In your sensor policy, navigate to the Exploit protection screen.
In the Exploit protection screen, locate the Process exclusions area.
In the Process exclusions area, click Add New.
In the Process name column, enter the process name:
If you are using Windows versions released prior to Windows 10 Fall Creators Update (Windows 7 SP1, Windows 8, Windows 8.1, or Windows 10 versions released prior to the Fall Creators Update), enter the full path of the process.
If you are using Windows 10 Fall Creators Update and later versions, enter the full process name or the full path of the process. The process name is not case-sensitive.
Click the check mark (✓) to save the exclusion.
Exclude by fingerprint for Variant File Prevention
You can add exclusions for Variant File Prevention by fingerprint, to exclude specific scenarios. The fingerprint name is displayed in the MalOp details screen in the Description area (e.g. BOF Payload, Conti_Ransomware).
In your sensor policy, navigate to the Anti-Malware screen.
In the Variant file prevention section, under Exclusions by fingerprint, click Add New.
Enter the fingerprint to exclude.
Exclusion examples
The sections below show use-cases or specific examples of how to add exclusions.
Anti-Malware exclusions
When you add an exclusion, you can exclude a specific folder, or use wildcards to exclude files within specific folders, nested folders, file extensions, and more.
See the following examples for common exclusion scenarios:
Exclude files in a specific folder
Exclude any folder path that contains a specific string
Exclude files in a path that ends with a specific folder
Exclude files with specific folders within the path
Excludes files with a specific file extension in a specific folder
Note
Folder, file, and process names are not case-sensitive.
Scenario |
Description |
Exclusion |
Result |
|---|---|---|---|
1 |
Option 1: Exclude files under specificfolder, without nested folders. Option 2: Exclude a specific folder and its nested folders, on Windows endpoints using Anti-Malware > Signatures mode only. |
Option 1: Type the folder path, ending with a forward slash. For example: /foldera/folderb/folderc/specificfolder/. Option 2: Type the folder path in the following format, ending with a backslash: C:\storage\temp\ |
Option 1 excludes only files located directly under specificfolder. Option 2 excludes files located under the temp folder, including nested folders. This option includes a minor performance improvement compared to wildcard exclusions. |
2 |
Exclude all paths that contain the /foldera/specificfolder/ string. |
*/foldera/specificfolder/* |
This excludes all files and folders that contain /foldera/specificfolder/ in their path. For example:
|
3 |
Exclude files and folders under any path that ends with /program files/. |
*/program files/ |
This excludes files under the program files folder, where the program files folder can be at any nesting level. For example, this exclusion excludes:
|
4 |
Exclude files under any path that begins with the program files folder, and includes the somefolder folder in the middle of the path. |
/program files/*/somefolder/* |
This excludes files under somefolder, at any nesting level, as long as the path begins at the program files top level folder. For example, the /program files/folder20/somefolder/foldera/folderb/folderc/test.txt file. |
5 |
Exclude all files with the .pkg extension in any Folder1 folder. |
Use one of the following formats. The ? wildcard character is supported in version 21.1.244 and later.
|
This excludes the following files:
|
Anti-Ransomware exclusions
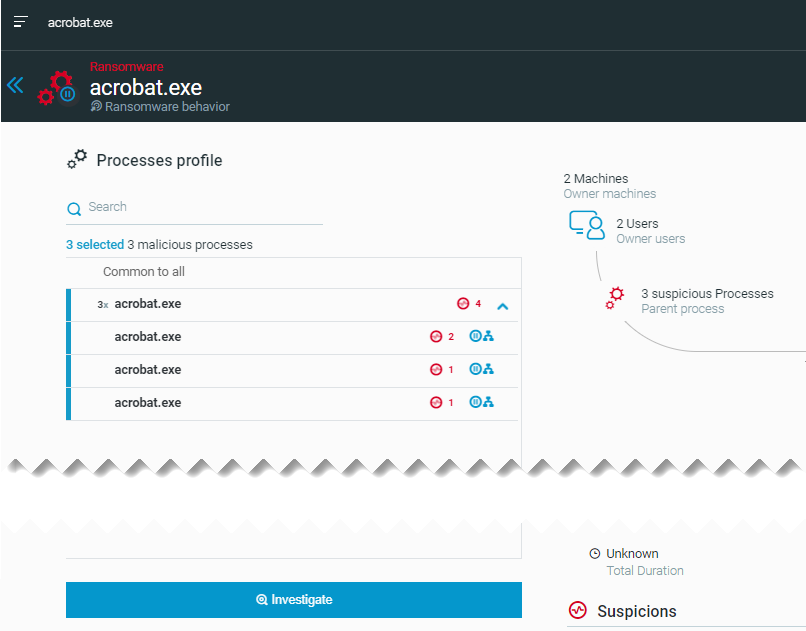
In this example, the acrobat.exe process triggered a Ransomware MalOp, and the following suspicious processes are visible:
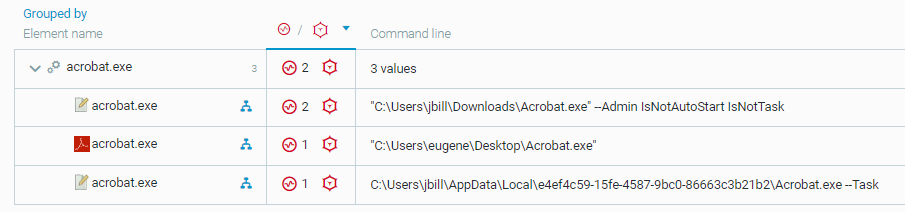
When you investigate the acrobat.exe process, four suspicious processes are visible in the query results.
In this scenario, you must add three exclusions, using each of the following command line values:
“C:\Users\jbillDownloads\Acrobat.exe” –Admin IsNotAutoStart IsNotTask
“C:\Users\eugene\Desktop\Acrobat.exe”
C:\Users\jbill\AppData\Local\e4ef4c59-15fe-4587-9bc0-86663c3b21b2\Acrobat.exe –Task