Add Exclusions from NGAV Protection
Note
In versions 23.2.65 and later, sensor policy exclusions can be managed in the Policy exclusions screen. Contact your Customer Success Manager to gain access to this feature.
In some cases, due to the modes set in some of your sensor policy configurations, the Cybereason platform may generate false positive detections for activity on endpoint machines or prevent legitimate programs from running successfully.
To help with cases like this or to exempt specific items from the various NGAV protections, you add exclusions in your sensor policy. For example, you can exclude a specific file directory from Anti-Malware scans, or exclude domains from analysis by Fileless Protection.
You can enter all your exclusions in the Policy exclusions screen. Once you add an exclusion in this screen, the Cybereason platform applies the exclusion to all the relevant NGAV protection engines, and also adds the exclusion to the relevant section in the various NGAV screens in the sensor policy.
Note
If a file hash/IP address/domain name is added to your environment’s allowlist, the various NGAV protection engines will not detect or prevent this item, even if the item is not added as an exclusion. Likewise, if you add an item as an exclusion but do not add the same item on the allowlist, the Cybereason platform will not prevent the item, but may generate a MalOp for the same item.
In this topic:
What exclusions can I add?
When you consider whether to add an exclusion, you often have a specific program, file, domain, or other item you know can be exempt from detection and prevention of malicious activity, or that is causing problems due to false positive detection or prevention.
When you add an exclusion, you can add the following exclusions for specific types of NGAV detection and prevention:
Item |
Description |
NGAV Engines |
|---|---|---|
File |
A file or directory |
Anti-Malware |
Process |
A process (identified by process name or directory) |
Exploit Protection Fileless Protection Behavioral Execution Prevention |
Process command line |
A command in a process’s command line |
Predictive Ransomware Protection |
Domain |
A name of a domain (but not specific URLs in the domain) |
Fileless Protection |
Loaded module |
A module loaded by a process, identified by module name |
Fileless Protection |
Script pattern |
A pattern in a script file |
Fileless Protection |
Fingerprint |
A genetic fingerprint for a binary file found by file analysis |
Anti-Malware (Variant File Prevention) |
Rule I |
A Rule ID for a specific detection rule used by Behavioral Document Protection |
Anti-Malware - Rule-based Behavioral Document Protection |
Behavior ID |
An identifier for a behavior identified by Behavioral Document Protection |
Anti-Malware - AI-based Behavioral Document Protection |
View and filter exclusions
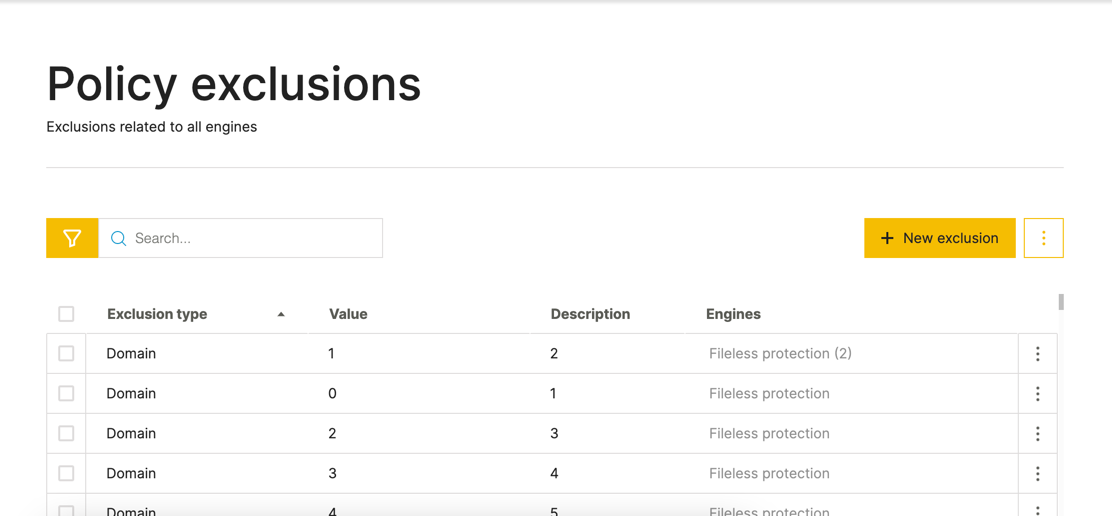
When you open the Policy exclusions screen, you can see all your exclusions that you add (both exclusions that you added previously and exclusions you add in the Policy exclusions screen).
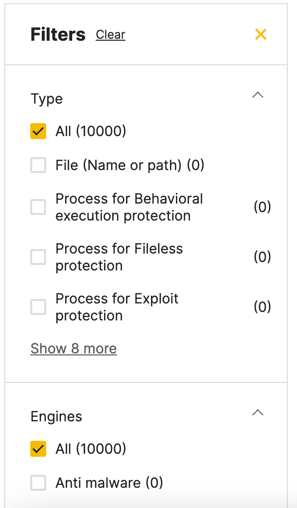
You can filter these exclusions as needed, both by the Type of exclusion, as well as the protection Engine:
Add an exclusion manually
You can add each exclusion individually as needed in the Policy exclusions screen:
To add an exclusion, follow these steps:
In your sensor policy, open the Policy exclusions screen.
Note
If you previously added exclusions in the other sensor policy screens, you will see the existing exclusions already displayed in the Policy exclusions screen.
In the Policy exclusions screen, click New exclusion.
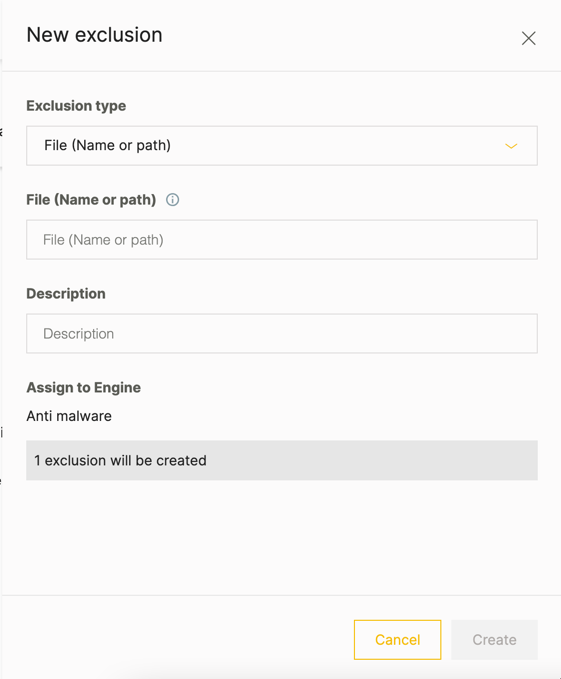
In the New exclusion dialog box, in the Exclusion type field, select the type of exclusion to add.
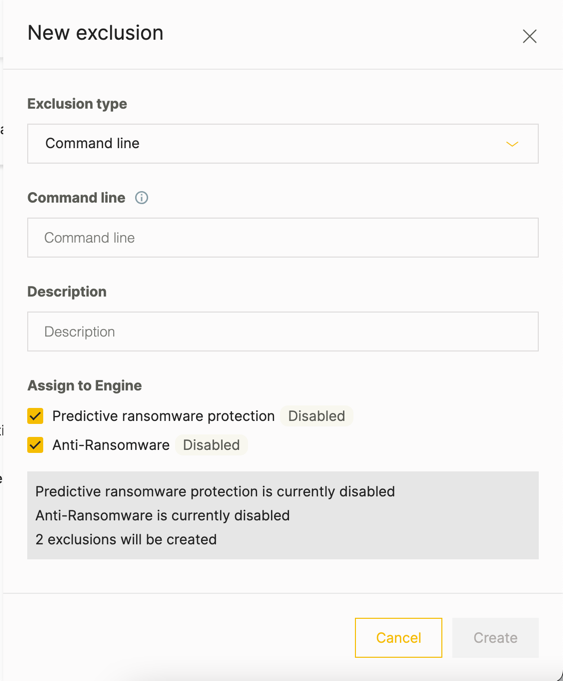
As you select an exclusion type, the Cybereason platform selects the type of protection engine to which to apply the exclusion.
If you are adding an exclusion for a protection engine that you have not enabled yet, the Cybereason platform informs you that the protection engine is not enabled:
In the value field, enter the syntax for the exclusion.
Note
The name of this field updates depending on the type of exclusion. For example, for a File (Name or path) exclusion, the field is named File (Name or Path). Likewise, for the Command line exclusion, the field is named Command line.
The format of the exclusion differs depending on the type of exclusion
Exclusion type
Syntax
File (name or path)
Enter one of the following:
File name
Path to a specific directory
Full path to a specific file
You can use wildcard characters, including:
Asterisk (*): Add the asterisk in a file path to match any amount of characters and any value. For example, adding an exclusion *:/folder will exclude dijorgidrg:/folder or C:folder.
Note
Previous versions of the documentation used double asterisks in wildcard examples. The double asterisk in wildcard examples. The double asterisk syntax is still valid, but single asterisks still work for the exclusion.
Question mark (?): Add a question mark character to match one character and any value. For example, adding an exclusion ?:/folder matches C:folder or D:folder.
Cybereason does not recommend the use of file extension wildcards to exclude all files under a file extension (such as *.exe) as this may expose your system to attacks or breaches. In addition, using file extension wildcards might affect performance. Cybereason recommends excluding specific folders instead of using file extension wildcards.
For items on Windows machines, you can also use environment variables, in file and exclusions. For example, adding an exclusion %ALLUSERSPROFILE%CustomLogFilesfile.exe will exclude the file.exe file but uses the %ALLUSERSPROFILE% variable to identify the user profile folder on machines.
Process
Enter one of the following:
For Behavioral Execution Prevention: The process name, full path to a process, or a folder path for a specific directory to which to exclude ALL processes.
For Fileless Protection: Enter the name of the process including the file extension (for example, processname.exe), or use a regular expression or regular expression pattern exclusion.
For example, to add an exclusion for a script named unnamed_arguments_example3.ps1, you add the exclusion rgx:unnamed_arguments_example_3.ps1.
Likewise, to add a regular expression pattern exclusion for a process named internaltool_v107.exe, you add rgx:(InternalTool_v)*(.exe*). Using this format applies the exclusion to other versions of the tool or process.
Note
Ensure you use specific values (process name, script, etc.) in regular expression-based exclusions to ensure that only a specific process is excluded.
For Exploit Protection: Enter the full path to the process or the full process name.
Note
If you are using Windows versions before the Windows 10 Fall Creators Update (Windows 7 SP1, Windows 8, Windows 8.1, or Windows 10 before the Fall Creators update), you must enter the full path to the process.
Command line
Enter the exact command line syntax to exclude. For example, you could enter a command line like this in quotes: C:\Users\12345\AppData\Local\Microsoft\OneDrive\OneDrive.exe /background.
If you are unsure of the exact command line syntax, locate the MalOp containing the item you want to excuse. In the Process tab in the MalOp details, click Investigate. In the query results that display, the command line syntax displays in the Command line column for the process.
Domain
Enter the domain name.
The exclusion must be a domain name, but not a full URL. For example, you would enter s3.amazonaws.com instead of the URL https://s3.amazonaws.com/example/example.
If you enter a full URL, the Cybereason platform does not apply the exclusion for the domain in the URL.
Floating module
Enter the full module name. For example, you could enter program.inception.
If you are unsure of the module name, in a Malicious use of PowerShell MalOp, open the MalOp details screen, and find the Loaded modules field. The name of the module you need will be found in that field.
Rule ID (for Behavioral Document Protection)
Add the rule ID the Cybereason platform uses for the rule that triggered the false positive detection.
The rules use a format like doc_aut_09 or doc_obf_15.
If you are unsure of the rule name, in the MalOp in question, navigate to the Document section and find the Properties > Detection value field. The detection rule is in that field.
Behavior ID
Add the behavior ID the Cybereason platform uses for the rule that triggered the false positive detection.
The Behavioral ID is a SHA-256 hash value.
If you are unsure of the rule name, in the MalOp in question, navigate to the Document section and find the Properties > Detection value field. The detection rule will be in that field.
Rule ID (for Behavioral Execution Prevention)
The exact text of the rule ID for the behavior to exclude.
The rule ID uses a syntax like accessibility_features.
If you are unsure of the rule ID, in the Malicious process behavior MalOp details screen, locate the Signature field. The rule ID is in that field.
Fingerprint
The exact name for the fingerprint to exclude.
If you are unsure of the fingerprint name, in the MalOp details for the MalOp, in the Description field, find the fingerprint name.
Pattern
The exact pattern name.
If you are unsure of the pattern name, in the Malicious command alert in the Malware alerts screen or in the Pattern field of the MalOp details for the MalOp, find the fingerprint name.
In the Description, enter a meaningful description.
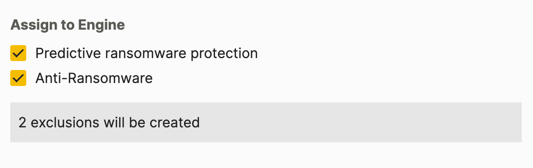
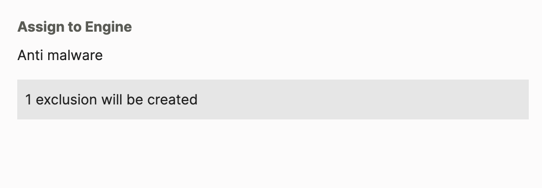
If needed, in the Assign to engine field, select the protection engines to which the exclusion applies.
If the exclusion is valid for only one type of protection engine, you do not need to select an engine value. The Cybereason platform automatically applies the exclusion to the one protection engine type.
Click Create.
In your sensor policy, click Save and publish to ensure the exclusions take effect.
The Cybereason platform adds the exclusion to the list of exclusions in the table. In addition, the Cybereason platform adds the exclusion in the relevant section of the sensor policy, such as adding File exclusions in the Anti-Malware screen.
You can later edit or delete any exclusion. In the row for the exclusion, click the three dot at the right side of the row and select Edit or Delete.
Import exclusions from a CSV file
If you have exclusions that you are adding from a different sensor policy or you want to manage exclusions separately for all sensor policies in your organization, you can import a CSV file containing exclusion details. This enables you to easily add exclusions for all sensor policies at scale, instead of needing to manually create each exclusion in each sensor policy.
To import exclusions, follow these steps:
If needed, in the Policy exclusions screen in the sensor policy from which you want to use the existing exclusions, at the right of the Add exclusion button, click the three dots and select Export to CSV.
A CSV file downloads to your machine.
If you do not have existing exclusions, click Download a CSV template to download the CSV template file you can use to add exclusions.
In the CSV file, ensure the file has a header row with four columns:
type
value
description
engines
In a new row for a new exclusion, in the type column, add the type of exclusion. You must use one of these values:
file
processBep
processFilelessProtection
processExploitProtection
command
domain
module
ruleId
ruleIdbBep
behaviorID
fingerprint
pattern
In the same row, in the value column, enter the value to exclude. The format of the exclusion differs depending on the type of exclusion:
Exclusion type
Syntax
File (name or path)
Enter one of the following:
File name
Path to a specific directory
Full path to a specific file
You can use wildcard characters, including:
Asterisk (*): Add the asterisk in a file path to match any amount of characters and any value. For example, adding an exclusion *:/folder will exclude dijorgidrg:/folder or C:folder.
Note
Previous versions of the documentation used double asterisks in wildcard examples. The double asterisk in wildcard examples. The double asterisk syntax is still valid, but single asterisks still work for the exclusion.
Question mark (?): Add a question mark character to match one character and any value. For example, adding an exclusion ?:/folder matches C:folder or D:folder.
Cybereason does not recommend the use of file extension wildcards to exclude all files under a file extension (such as *.exe) as this may expose your system to attacks or breaches. In addition, using file extension wildcards might affect performance. Cybereason recommends excluding specific folders instead of using file extension wildcards.
For items on Windows machines, you can also use environment variables, in file and exclusions. For example, adding an exclusion %ALLUSERSPROFILE%CustomLogFilesfile.exe will exclude the file.exe file but uses the %ALLUSERSPROFILE% variable to identify the user profile folder on machines.
Process
Enter one of the following:
For Behavioral Execution Prevention: The process name, full path to a process, or a folder path for a specific directory to which to exclude ALL processes.
For Fileless Protection: Enter the name of the process including the file extension (for example, processname.exe), or use a regular expression or regular expression pattern exclusion.
For example, to add an exclusion for a script named unnamed_arguments_example3.ps1, you add the exclusion rgx:unnamed_arguments_example_3.ps1.
Likewise, to add a regular expression pattern exclusion for a process named internaltool_v107.exe, you add rgx:(InternalTool_v)*(.exe*). Using this format applies the exclusion to other versions of the tool or process.
Note
Ensure you use specific values (process name, script, etc.) in regular expression-based exclusions to ensure that only a specific process is excluded.
For Exploit Protection: Enter the full path to the process or the full process name.
Note
If you are using Windows versions before the Windows 10 Fall Creators Update (Windows 7 SP1, Windows 8, Windows 8.1, or Windows 10 before the Fall Creators update), you must enter the full path to the process.
Command line
Enter the exact command line syntax to exclude. For example, you could enter a command line like this in quotes: C:\Users\12345\AppData\Local\Microsoft\OneDrive\OneDrive.exe /background.
If you are unsure of the exact command line syntax, locate the MalOp containing the item you want to excuse. In the Process tab in the MalOp details, click Investigate. In the query results that display, the command line syntax displays in the Command line column for the process.
Domain
Enter the domain name.
The exclusion must be a domain name, but not a full URL. For example, you would enter s3.amazonaws.com instead of the URL https://s3.amazonaws.com/example/example.
If you enter a full URL, the Cybereason platform does not apply the exclusion for the domain in the URL.
Floating module
Enter the full module name. For example, you could enter program.inception.
If you are unsure of the module name, in a Malicious use of PowerShell MalOp, open the MalOp details screen, and find the Loaded modules field. The name of the module you need will be found in that field.
Rule ID (for Behavioral Document Protection)
Add the rule ID the Cybereason platform uses for the rule that triggered the false positive detection.
The rules use a format like doc_aut_09 or doc_obf_15.
If you are unsure of the rule name, in the MalOp in question, navigate to the Document section and find the Properties > Detection value field. The detection rule is in that field.
Behavior ID
Add the behavior ID the Cybereason platform uses for the rule that triggered the false positive detection.
The Behavioral ID is a SHA-256 hash value.
If you are unsure of the rule name, in the MalOp in question, navigate to the Document section and find the Properties > Detection value field. The detection rule will be in that field.
Rule ID (for Behavioral Execution Prevention)
The exact text of the rule ID for the behavior to exclude.
The rule ID uses a syntax like accessibility_features.
If you are unsure of the rule ID, in the Malicious process behavior MalOp details screen, locate the Signature field. The rule ID is in that field.
Fingerprint
The exact name for the fingerprint to exclude.
If you are unsure of the fingerprint name, in the MalOp details for the MalOp, in the Description field, find the fingerprint name.
Pattern
The exact pattern name.
If you are unsure of the pattern name, in the Malicious command alert in the Malware alerts screen or in the Pattern field of the MalOp details for the MalOp, find the fingerprint name.
Optionally, in the description column, enter a meaningful description.
Optionally, in the engines column, add the engine that is relevant for your exclusion:
Exclusion type
Value for engines column
file
antiMalware
processBep
behavioralExecutionPrevention
processFilelessProtection
filelessProtection
processExploitProtection
exploitProtection
command
predictiveRansomwareProtection
antiRansomware
domain
filelessProtection
module
filelessProtection
ruleId
antiMalware
ruleIdBep
behavioralExecutionPrevention
behaviorId
antiMalware
fingerprint
antiMalware
pattern
filelessProtection
If you do not add a value in the engines column for each exclusion type, the Cybereason platfomr will add the relevant engine for the exclusion when you upload the CSV file.
In the Import exclusions CSV dialog box, click Browse file and navigate to the location where you saved the file.
Click Import exclusions.
After you import the CSV file, the Cybereason platform validates that the data in the CSV file is correct.
If all the rows and data in the file are correct, you will see a dialog that informs you the number of exclusions that the Cybereason platform added.
If there are errors in the CSV file, the Cybereason platform will display an error message with details on the errors.
If an exclusion already exists and you update the engine for this exclusion, the Cybereason platform edits the existing reputation with the new details. If the exclusion already exists, but you did not specify a protection engine in the CSV file, the Cybereason platform edits the existing exclusion to remove the protection engine for that specific exclusion.
In your sensor policy, click Save and publish to ensure the exclusions take effect.