Generic Queries
Generic queries may return a high rate of false positives, but they are useful in noisy environments.
The example queries in this section are meant to be a starting point for your investigations. You may need to update the Features (filters) in each query to use indicators specific to your environment or situation.
Each of these examples is formatted with the individual Element in the query on its own separate line, in bold text. Features (filters) applied to the Element follow the Element name in regular weight text. Each example also contains a description of the goal of the hunt and the explanatory statement of what you want to find.
In this topic:
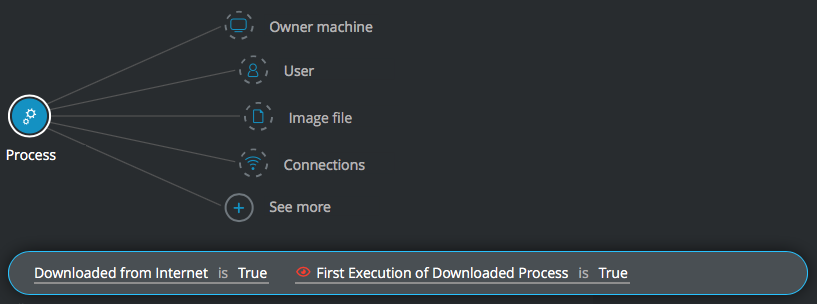
Find binaries users downloaded from the Internet
Goal: Find binary files that were downloaded from the Internet
Explanatory statement: I want to get a list of all binary files downloaded from the Internet.
Construct this query:
Process Element -> filter for Downloaded from Internet is True AND filter for First Execution of Downloaded Process is True
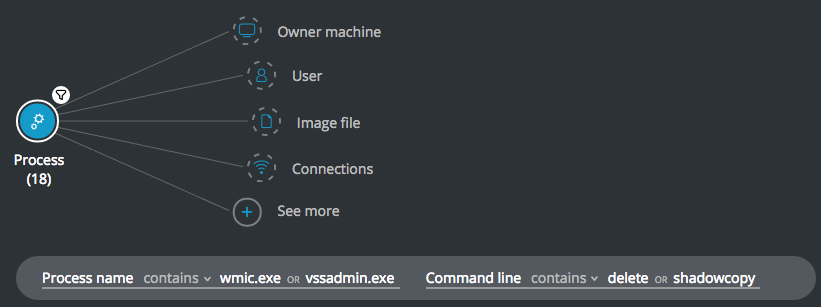
Find attempts to delete Windows shadowfiles
Goal: Find strange admin behavior and potentially some ransomware.
Explanatory statement: I want to find admin processes behaving strangely like ransomware.
Construct this query:
Process Element -> filter for Process name contains wmic.exe OR vssadmin.exe AND filter for Command line contains delete OR shadowcopy
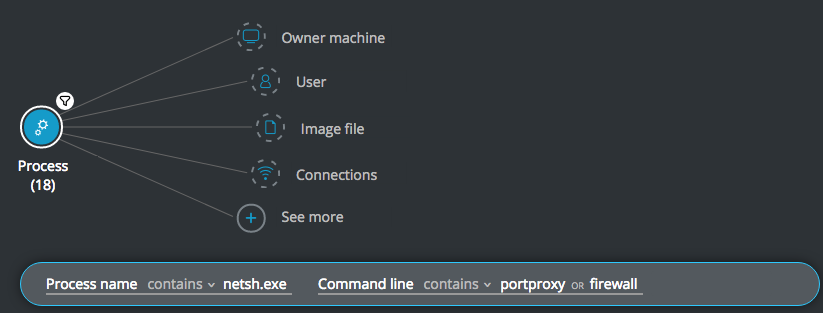
Find attempts to modify the firewall (including port forwarding)
Goal: Find active attackers who are pivoting through your network.
Explanatory statement: I want to find processes attempting to change firewall settings.
Construct this query:
Process Element -> filter for Process name contains netsh.exe and filter for Command line contains portproxy OR firewall