Foothold Queries
Researching foothold helps you find suspicious behavior associated with the foothold stage of an attack. Use these example to help you find attackers attempting to gain a foothold in your system.
The example queries in this section are meant to be a starting point for your investigations. You may need to update the Features (filters) in each query to use indicators specific to your environment or situation.
Each of these examples is formatted with the individual Element in the query on its own separate line, in bold text. Features (filters) applied to the Element follow the Element name in regular weight text. Each example also contains a description of the goal of the hunt and the explanatory statement of what you want to find.
In this topic:
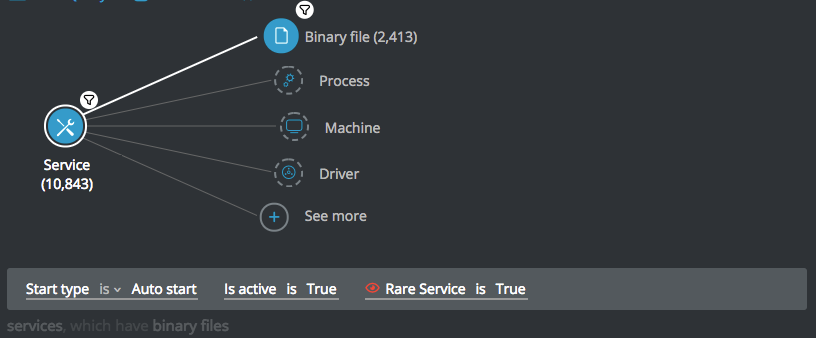
Autorun services
Goal: Locate files that are set to automatically run when the computer starts up, have a binary file that is not signed, and contains what Cybereason defines as rare evidence. This query returns some interesting data, including whether the service triggers the hiddenFile extension or right-to-left evidences.
Explanatory statement: I want to find files that are configured to automatically run when the machine starts, which also have a binary file that is not signed and are associated with services that are not common.
Construct this query:
Service Element -> Filter for Start type is Auto start AND filter for Is Active is True AND filter for Rare Service is True THEN
Binary file Element -> filter for Signed is False
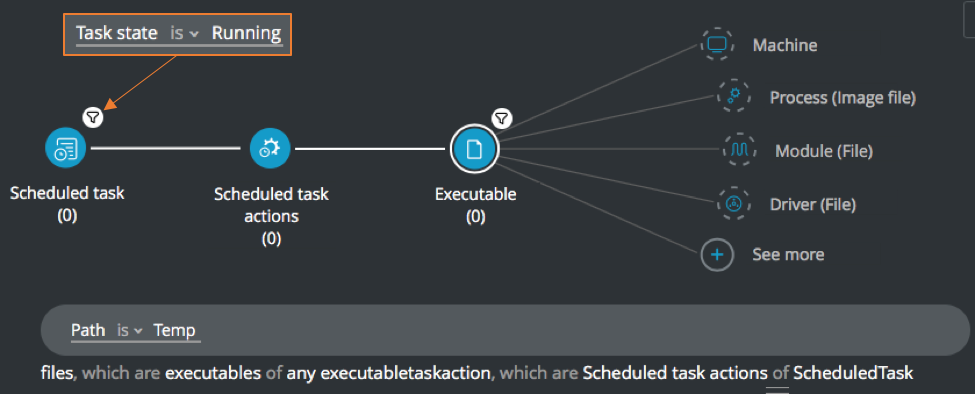
Scheduled tasks executed from the Temp folder
Goal: Identify scheduled tasks running from the C:\Temp folder. Behaviors such as this are often indicative of suspicious behavior as the Temp folder is usually not used for running applications.
Explanatory statement: I want to find scheduled tasks which run from the Temp folder on Windows
Construct this query:
Scheduled task Element -> filter for Task state is running THEN
Scheduled task actions Element -> filter for Path contains Temp