Scanning Queries
The following examples show how to hunt for malicious behavior occurring in the scanning stage of a cyber attack.
The example queries in this section are meant to be a starting point for your investigations. You may need to update the Features (filters) in each query to use indicators specific to your environment or situation.
Each of these examples is formatted with the individual Element in the query on its own separate line, in bold text. Features (filters) applied to the Element follow the Element name in regular weight text. Each example also contains a description of the goal of the hunt and the explanatory statement of what you want to find.
In this topic:
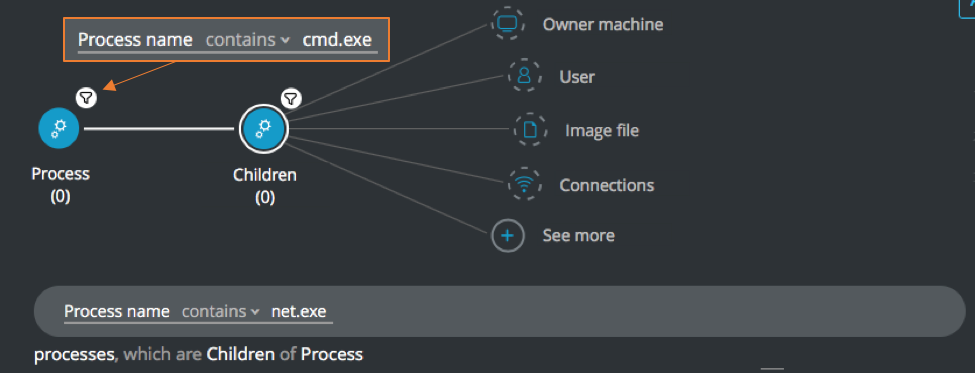
Processes executing extensive net commands
Goal: Find command line processes with child processes executing net commands.
Explanatory statement: I want to find processes that use commands to launch child processes to run net commands.
Construct this query:
Process Element -> filter for Process name contains cmd.exe THEN
Children Element -> filter for Process name contains net.exe
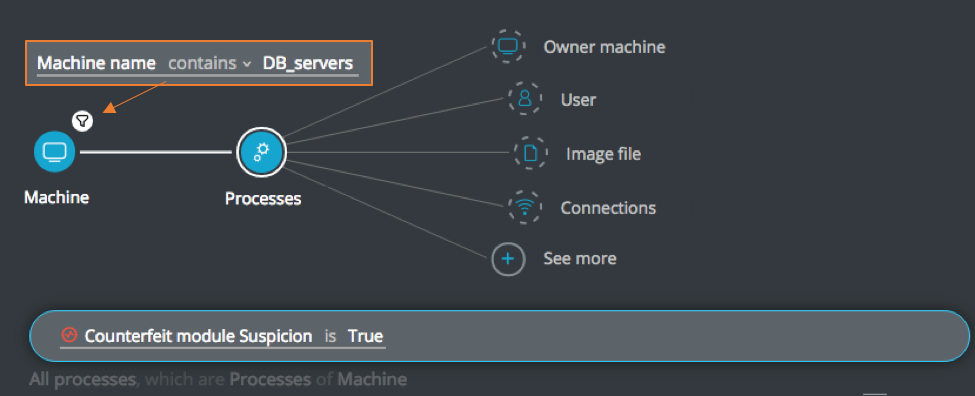
Fake module suspicion
Goal: Investigate machines running processes with counterfeit modules.
Explanatory statement: I want to find machines that have processes which run counterfeit modules.
From the list of assets you gathered in the asset mapping, query for the following suspicious behaviors:
DB_servers = [“serverName1”, “serverName2”,….]
Web_servers = [“serverName1”, “serverName2”,….]
Mail_servers = [“serverName1”, “serverName2”,….]
Construct this query for every servers list.
Machine Element -> filter for Machine name contains DB_servers THEN
Processes Element -> filter for Counterfeit module Suspicion is True
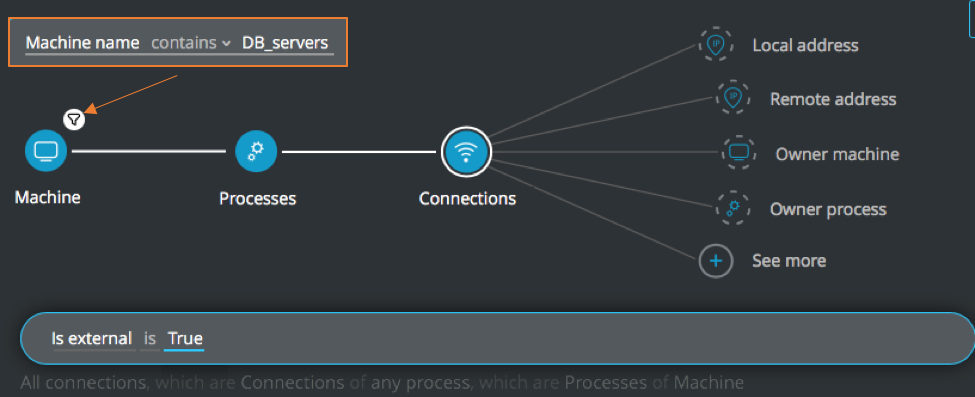
Database external connection
Goal: Investigate machines running processes with external connections.
Explanatory statement: I want to find machines that have processes making a connection to addresses outside my organization.
From the list of assets you gathered in the asset mapping, query for the following suspicious behaviors:
DB_servers = [“serverName1”, “serverName2”,….]
Web_servers = [“serverName1”, “serverName2”,….]
Mail_servers = [“serverName1”, “serverName2”,….]
Construct this query for every servers list.
Machine Element -> filter for Machine name contains DB_servers THEN
Processes Element THEN
Connections Element -> filter for Is external is True