Penetration Queries
Penetration vectors help you find suspicious behavior associated with the penetration stage of an attack. Use this examples to help you find attackers who have penetrated your network or are trying to penetrate your organization’s network.
The example queries in this section are meant to be a starting point for your investigations. You may need to update the Features (filters) in each query to use indicators specific to your environment or situation.
Each of these examples is formatted with the individual Element in the query on its own separate line, in bold text. Features (filters) applied to the Element follow the Element name in regular weight text. Each example also contains a description of the goal of the hunt and the explanatory statement of what you want to find.
In this topic:
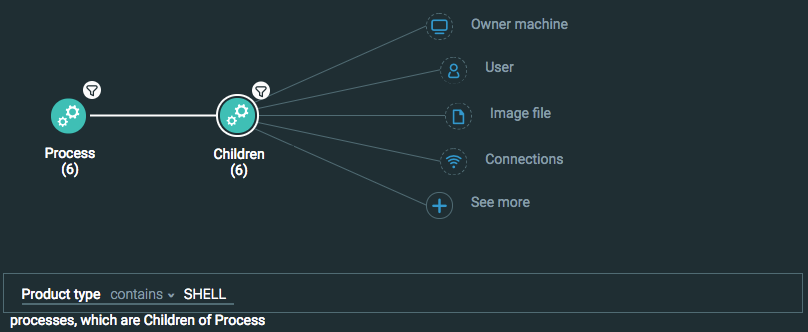
Child Shell processes
Goal: Locate suspicious behavior originating in child shell process, such as initiating connections, creation of additional children, and so forth.
Explanatory statement: I want to find suspicious behaviors that come from child shell processes.
Construct this query:
Process Element -> filter for Product type is Microsoft Office THEN
Children Element -> filter for Product type is Shell
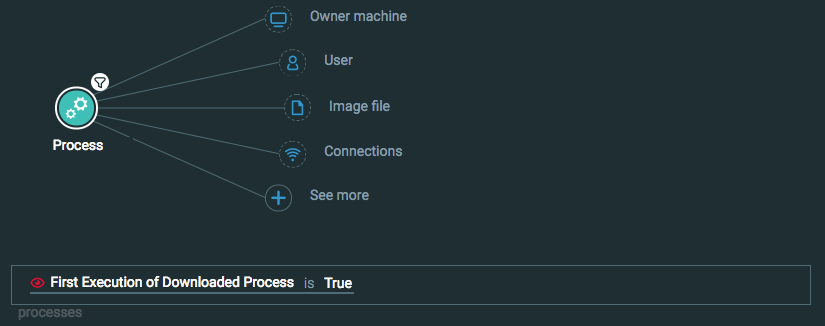
First Execution of a downloaded process
Goal: Review the behavior of a downloaded process after it runs for the first time. The results include information such as whether the process has Suspicions, what the parent processes are, when the processes were created, and so forth.
Explanatory statement: I want to investigate the behavior of a process that was downloaded after that process runs for the first time.
Construct this query:
Process Element -> filter for First Execution of Downloaded Process is True
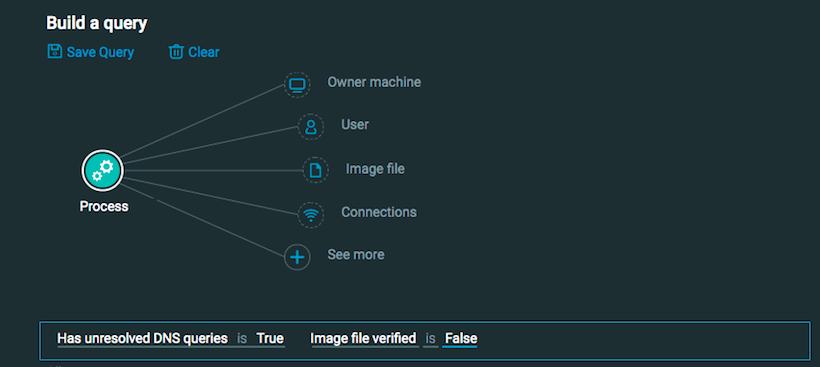
DGA
Goal: Search for malicious characteristics of a process. The results return information including the process tree, command line arguments, and file path for each process.
Explanatory statement: I want to look at some malicious characteristics of a process, such as the fact that it has unresolved DNS queries or the image file is not verified.
Construct this query:
Process Element -> Has unresolved DNS queries is True AND Image file verified is False