Infection Queries
Hunt for malicious behavior occurring in the infection stage of a cyber attack.
The example queries in this section are meant to be a starting point for your investigations. You may need to update the Features (filters) in each query to use indicators specific to your environment or situation.
Each of these examples is formatted with the individual Element in the query on its own separate line, in bold text. Features (filters) applied to the Element follow the Element name in regular weight text. Each example also contains a description of the goal of the hunt and the explanatory statement of what you want to find.
In this topic:
Phishing
Goal: Search for suspicious behavior from the child shell process (connections, creation of additional children, etc.).
Explanatory statement: I want to find suspicious behavior originating from child shell processes.
Construct this query:
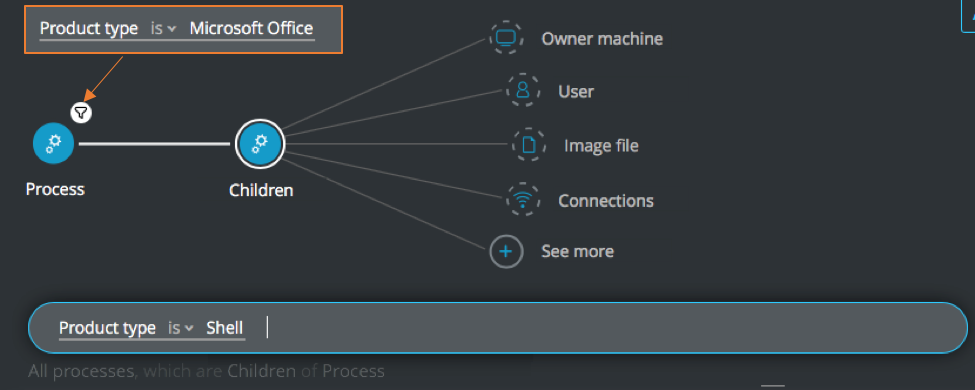
Process Element -> filter for Product type is Microsoft Office THEN
Children Element -> filter for Product type is Shell
First execution of downloaded file
Goal: Find instances of the first execution of downloaded processes
Explanatory statement: I want to find instances of first execution of a process or processes that were downloaded from somewhere.
Construct this query:
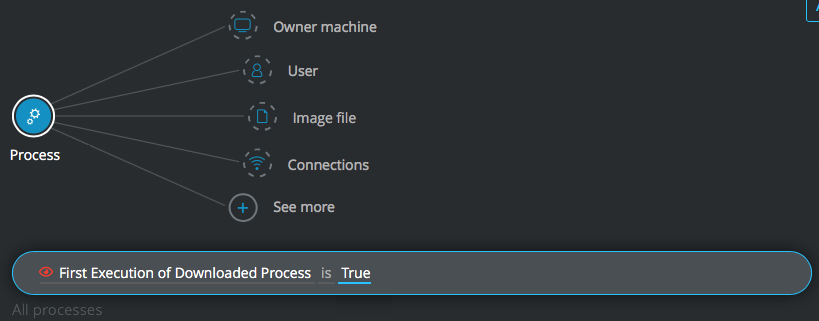
Process Element -> filter for First Execution of Downloaded Process is True
Processes with autorun registry key
Goal: Investigate processes that have an autorun registry key entry
Explanatory statement: I want to look at processes that use an registry key with autorun.
Construct this query:
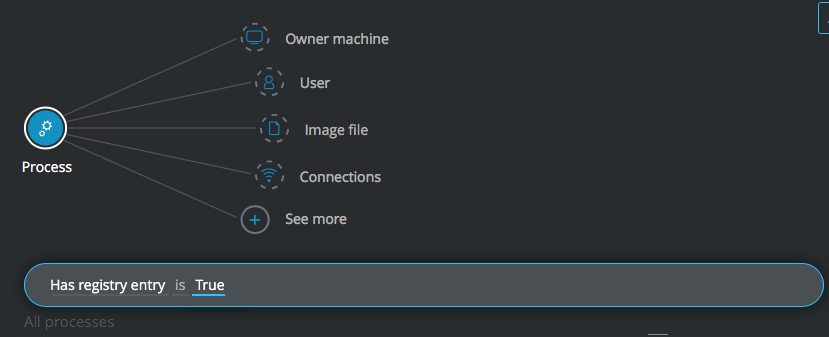
Process Element -> filter for Has registry entry is True
Autostart services
Goal: Search for rare services with an Auto start start type.
Explanatory statement: I want to find services that are not common and that are set to automatically run on machine restart.
Construct this query:
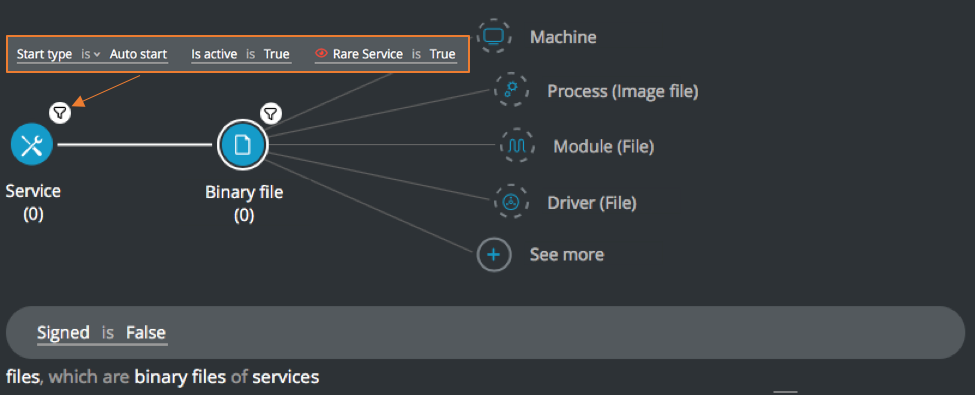
Service Element -> filter for Start type is Auto start AND Is active is True AND Rare Service is True THEN
Binary File Element -> filter for Signed is False
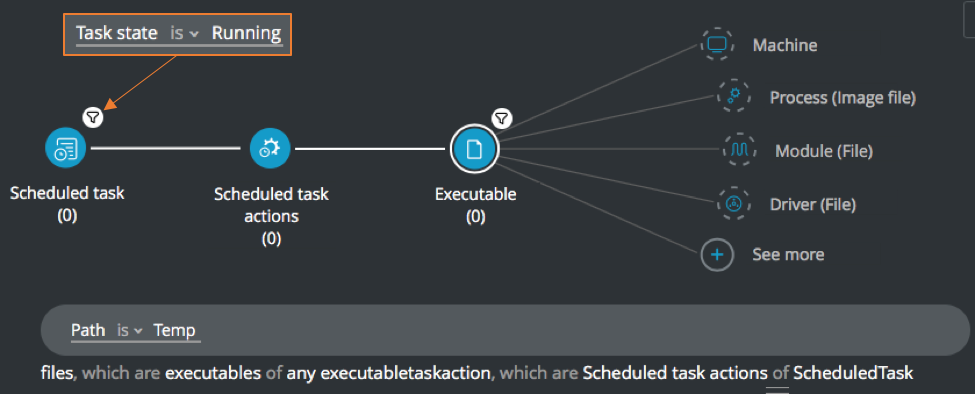
Scheduled task executed from temp
Goal: Review running tasks with actions executed from temp.
Explanatory statement: I want to investigate tasks that are currently running and that have been run from the //temp folder.
Construct this query:
Scheduled task Element -> filter for Task state is Running THEN
Scheduled task actions Element
Executable Element -> filter for Path is Temp
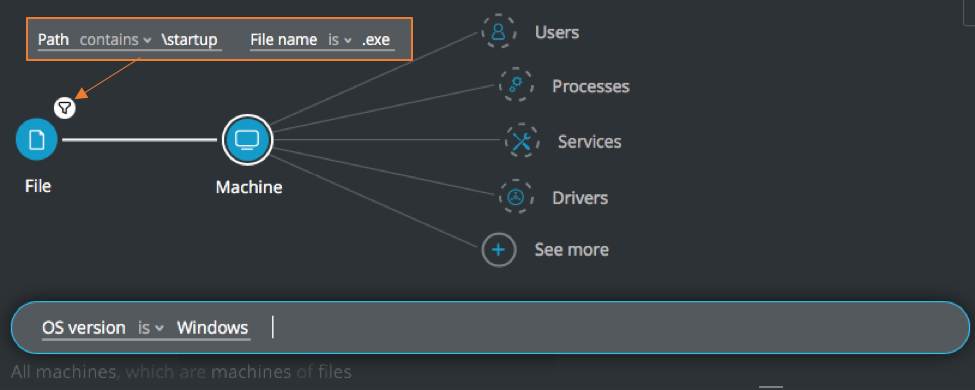
Startup Windows folder
Goal: Search for executable files in a location which usually stores shortcuts.
Explanatory statement: I want to search for executable files from the directories where the operating system normally keeps shortcuts.
Construct this query:
File Element -> filter for Path contains startup AND File name is .exe THEN
Machine Element -> filter for OS version is Windows
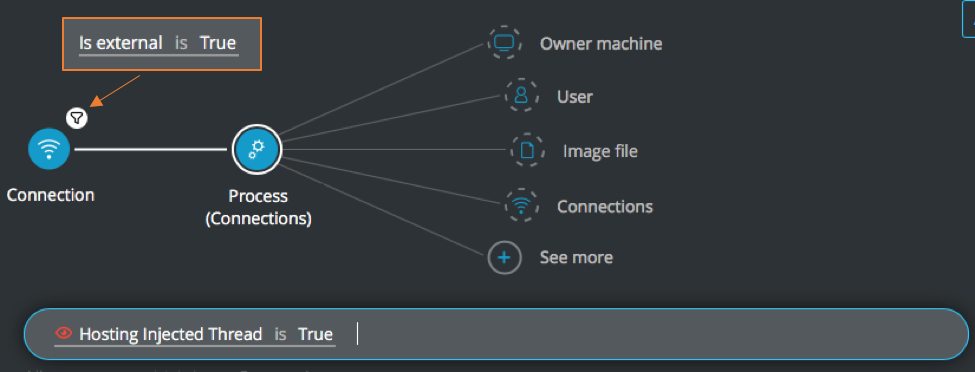
External connections from processes hosting injected threads
Goal: Find external connections coming from processes that host injected threads.
Explanatory statement: I want to find connections to external addresses that originate in processes that have injected threads.
Construct this query:
Connection Element -> filter for Is external is True THEN
Process Element -> filter for Hosting Injected Thread is True
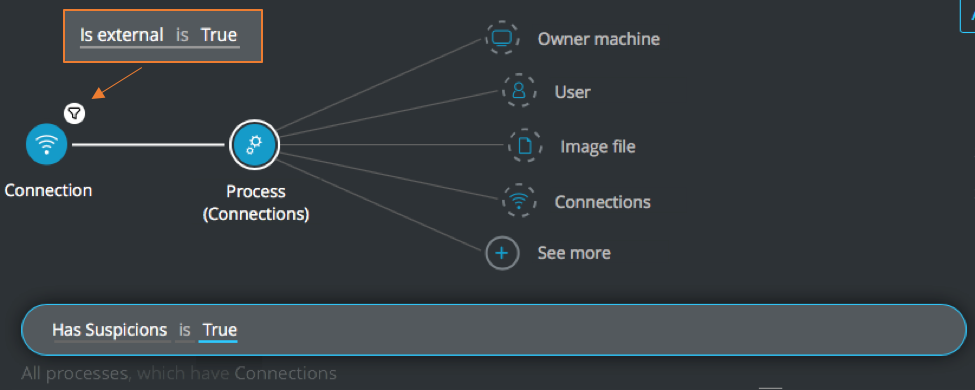
External connections from processes with suspicions
Goal: Find external connections coming from processes that have suspicions.
Explanatory statement: I want to find connections to external sources that are from suspicious processes.
Construct this query:
Connection Element -> filter for Is external is True THEN
Process Element -> filter for Has Suspicions is True
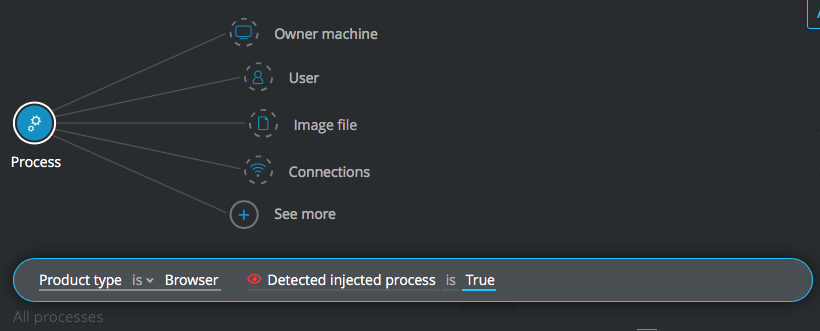
Injection by browser
Goal: Search for processes identified as running code that was injected by a browser process.
Explanatory statement: I want to find processes that have injected code from a browser.
Construct this query:
Process Element -> filter for Product type is Browser AND Detected injecting process is True
Note
Exclude well known browsers using the ! “Not” operator
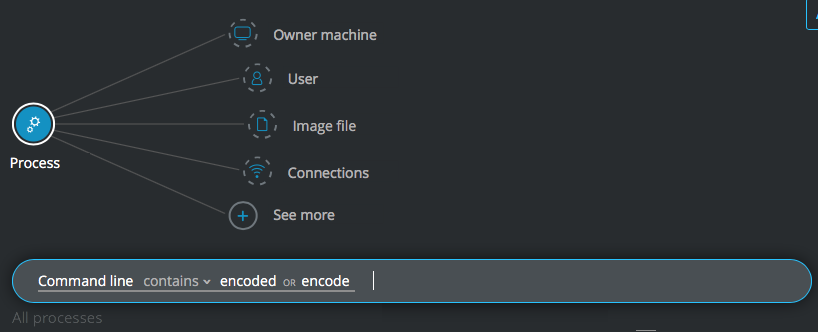
Encoded command
Goal: Search for processes which are not powershell.exe or cmd.exe but are executing PowerShell.
Explanatory statement: I want to find processes that are not PowerShell or the command line that are running PowerShell.
Construct this query:
Process Element -> filter for Command line contains encoded OR encode
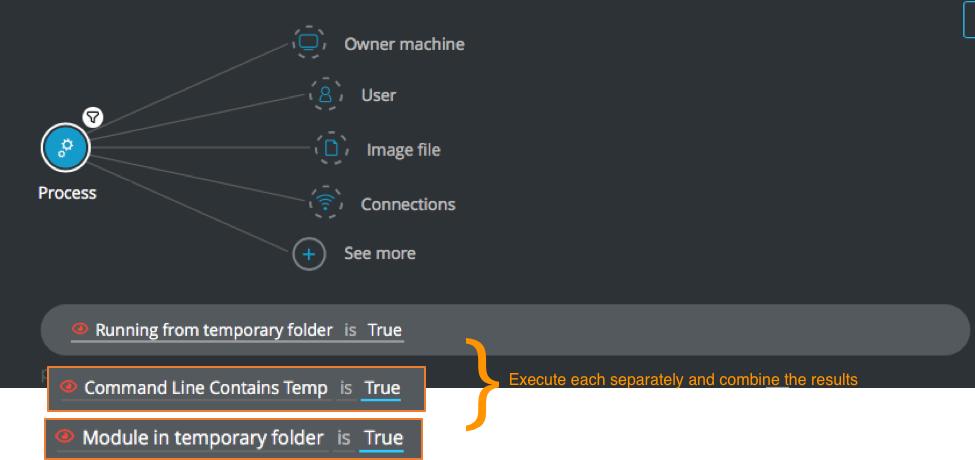
Executed from temp evidence
Goal: Review processes executed from temporary folders, has a command line that contains a parameter of a temporary location, or has a module located in a temporary folder.
Explanatory statement: I want to investigate processes running from a temporary folder that also have a command line parameter pointing to a temporary location or with a module running from a temporary location.
Construct the following three queries:
Process Element -> filter for Running from temporary folder is True
Process Element -> filter for Command Line Contains Temp is True
Process Element -> filter for Module in temporary folder is True
Note
The OR operator in this case will not work, this will require you to execute 3 separate queries or one query which includes all 3 filters.
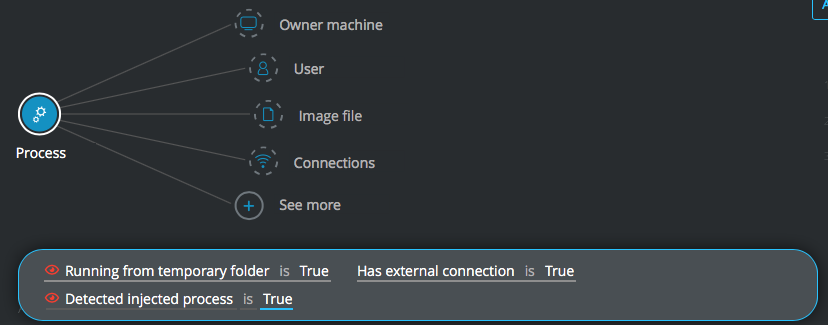
Suspicious temp file
Goal: Review processes running from a temporary folder that have external connections and injected processes.
Explanatory statement: I want to investigate processes running in a temporary folder that are connecting with an address that is external to my organization and that are injected processes.
Construct the following query:
Process Element -> filter for Running from temporary folder is True AND Has external connection is True AND Detected injected process is True
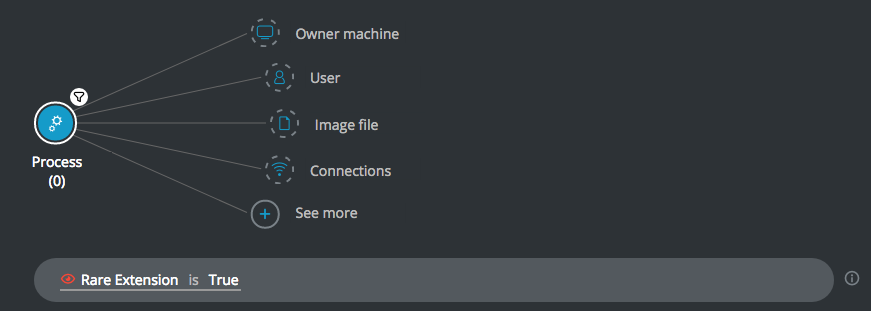
Rare extension
Goal: Search for processes with rare extensions.
Explanatory statement: I want to investigate processes that use unusual or uncommon extensions.
Construct the following query:
Process Element -> filter for Rare Extension is True
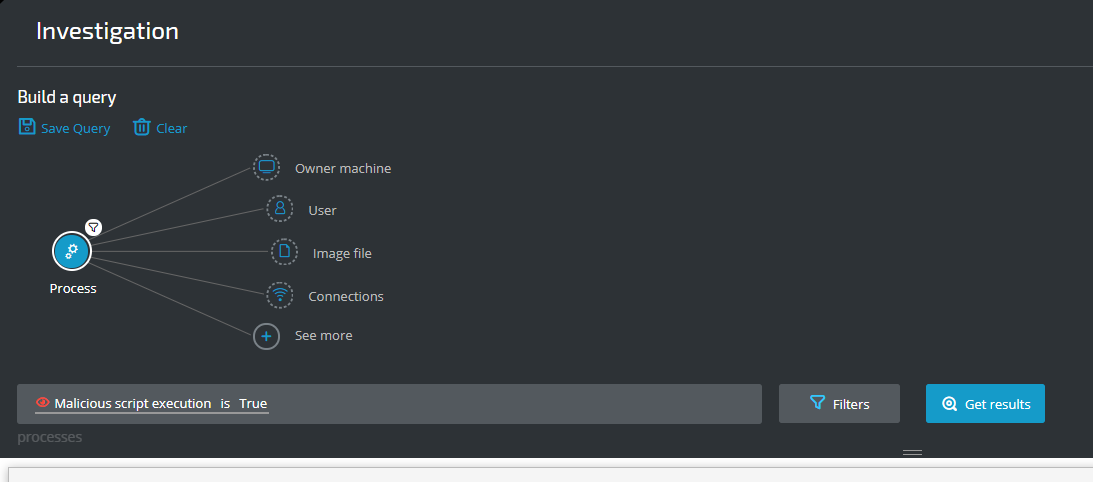
Fileless malware
Goal: Find evidence of fileless malware running on your systems.
Explanatory statement: I want to find instances of fileless malware.
Construct the following query:
Process Element -> filter for Malicious Script Execution