Credential Theft Queries
Use these examples to find instances of potential credential theft.
The example queries in this section are meant to be a starting point for your investigations. You may need to update the Features (filters) in each query to use indicators specific to your environment or situation.
Each of these examples is formatted with the individual Element in the query on its own separate line, in bold text. Features (filters) applied to the Element follow the Element name in regular weight text. Each example also contains a description of the goal of the hunt and the explanatory statement of what you want to find.
Processes accessing system resources with credential information
Accessing system AuditObject resources is usually a strong indicator of potential credential theft.
Goal: Find credential theft by access of operating system resources with credential details.
Explanatory statement: I want to find evidence of credential theft by finding processes that are accessing the operating system resources that contain credential information.
Construct one of the following queries to find examples of processes accessing system resources (like Audit Objects) that contain credential information.
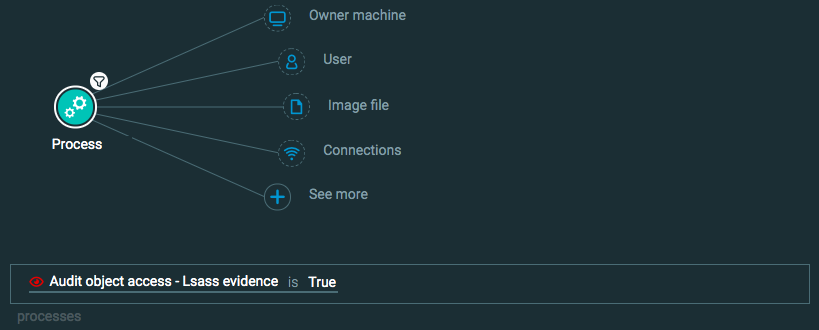
Query 1:
Process Element -> filter for Audit Object access - lsass evidence is True
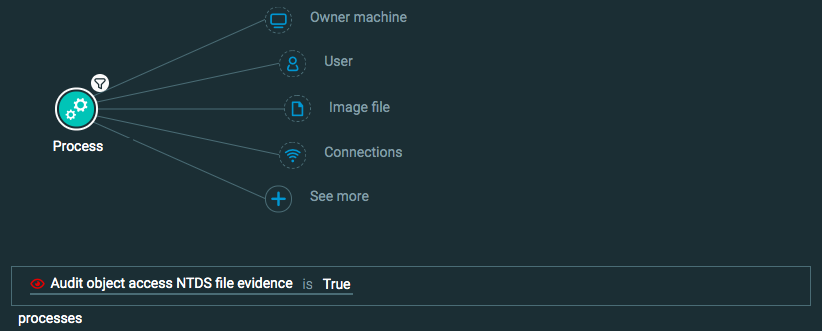
Query 2:
Process Element -> filter for Audit object access NTDS file evidence is True
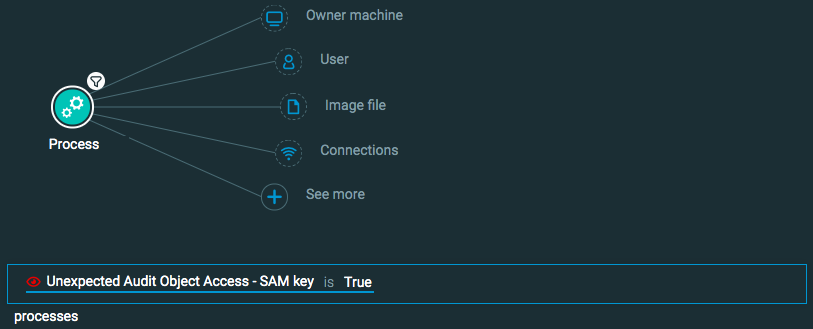
Query 3:
Process Element -> filter for Unexpected Audit Object Access - SAM key is True