MITRE ATT&CK Technique Examples
You can create a variety of different queries to find techniques included in the MITRE ATT&CK matrix. This section presents examples of several techniques.
The example queries in this section are meant to be a starting point for your investigations. You may need to update the Features (filters) in each query to use indicators specific to your environment or situation.
Each of these examples is formatted with the individual Element in the query on its own separate line, in bold text. Features (filters) applied to the Element follow the Element name in regular weight text. Each example also contains a description of the goal of the hunt and the explanatory statement of what you want to find.
In this topic:
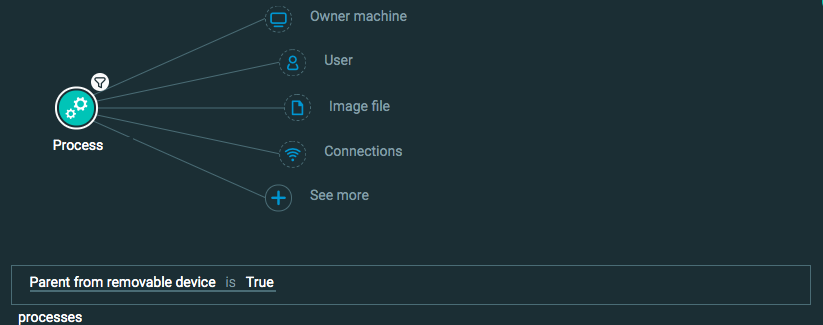
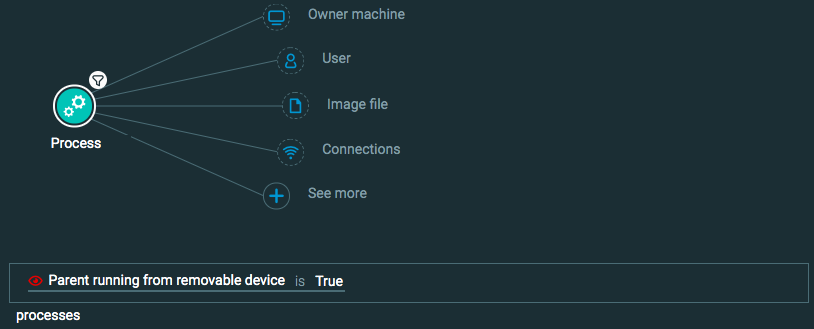
Initial Access: Replication Through Removable Media
Goal: Find if an attacker gets access to my machine through a removable disk.
Explanatory statement: I want to find instances where a process has been launched from a removable device.
Construct one of the following queries:
Query 1:
Process Element -> filter for Parent from removable device is True
Query 2:
Process Element -> filter for Parent running from removable device is True
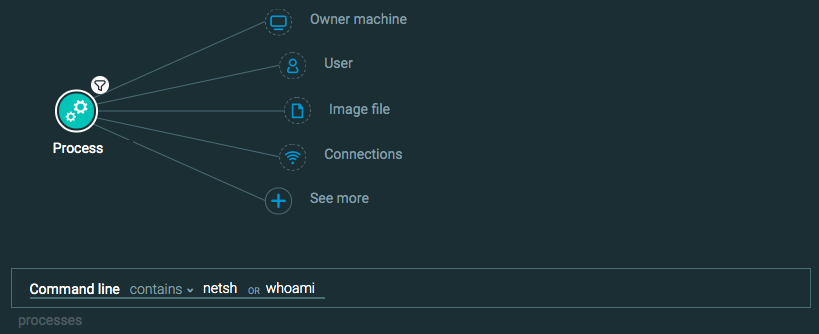
Execution: Command line interface
Goal: Find instances of a process running a command.
Explanatory statement: I want to find examples of <<a command>> running in my environment.
Construct the following query:
Process Element -> filter for Command line contains ______
You can add any command used in the command line as the text in this query.
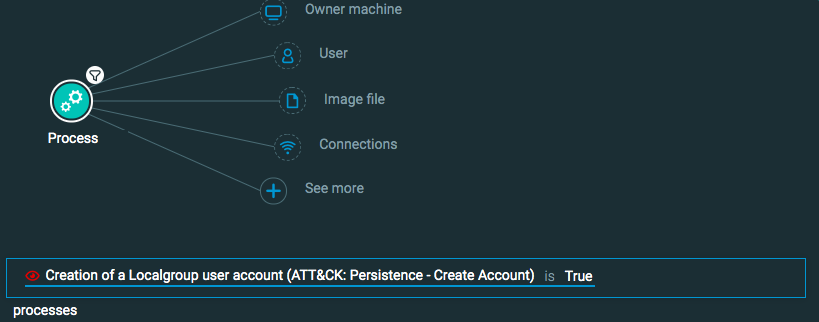
Persistence: Create Account
Goal: Find when a user creates a persistence mechanism through account creation.
Explanatory statement: I want to find instances of account creation that enable an attacker to maintain persistence on a machine.
Construct one of the following queries:
Query 1:
Process Element -> filter for Creation of a localgroup user account is True
Query 2:
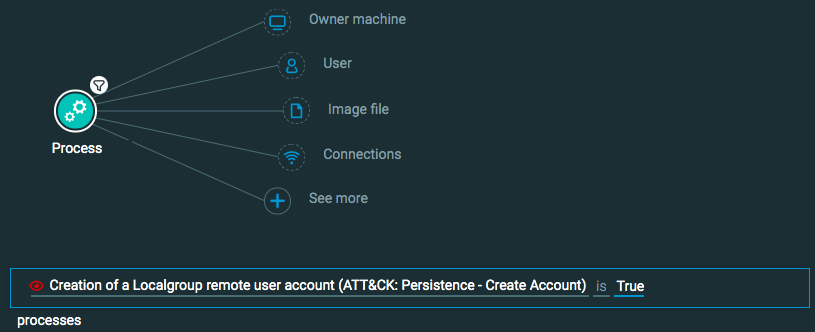
Process Element -> filter for Creation of a Localgroup remote user account is True
Query 3:
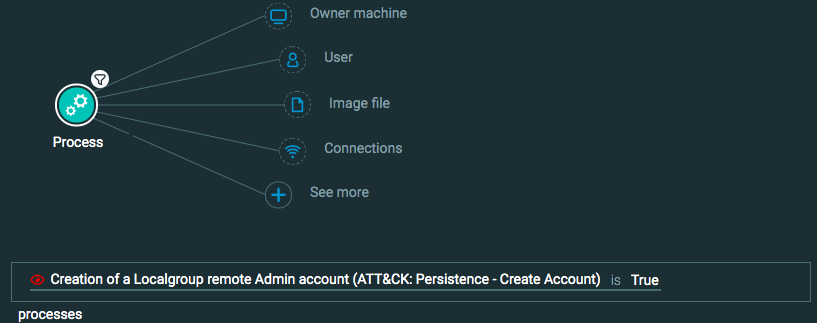
Process Element -> filter for Creation of localgroup remote admin account is True
Defense Evasion: Masquerading
Goal: Find application masquerading as something else.
Explanatory statement: I want to find examples of a process masquerading as a different type of application or file.
Construct one of the following queries:
Query 1:
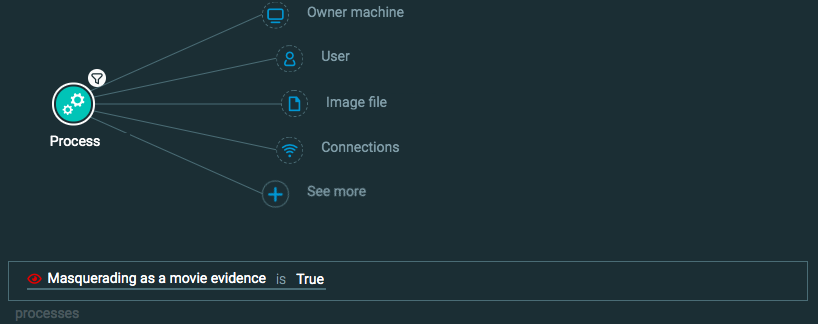
Process Element -> filter for Masquerading as a movie evidence is True
Query 2:
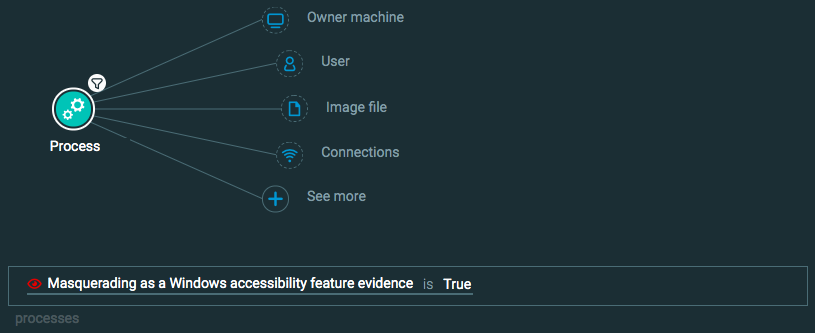
Process Element -> filter for Masquerading as a Windows accessibility feature evidence is True
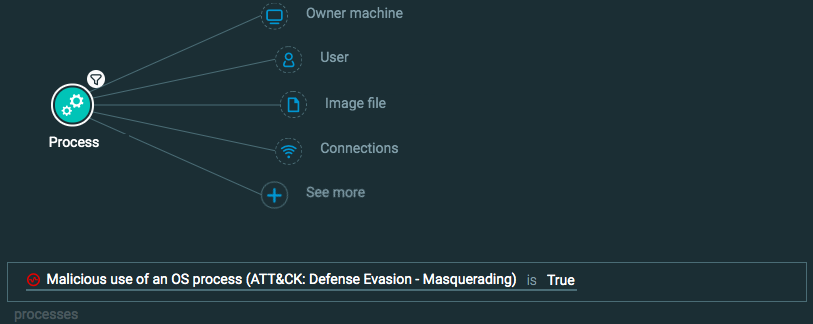
Query 3:
Process Element -> filter for Malicious use of an OS process is True
Credential Access: Credential Dumping
Goal: Find when an attacker performs credential dumping.
Explanatory statement: I want to find examples of a process performing a credential dump from different locations on a machine.
Construct one of the following queries:
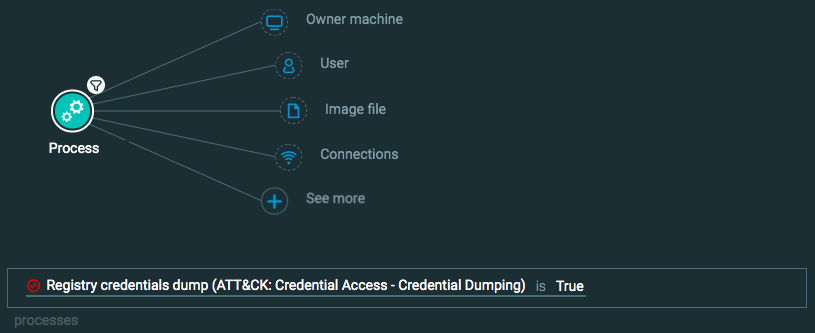
Query 1:
Process Element -> filter for Registry credentials dump is True
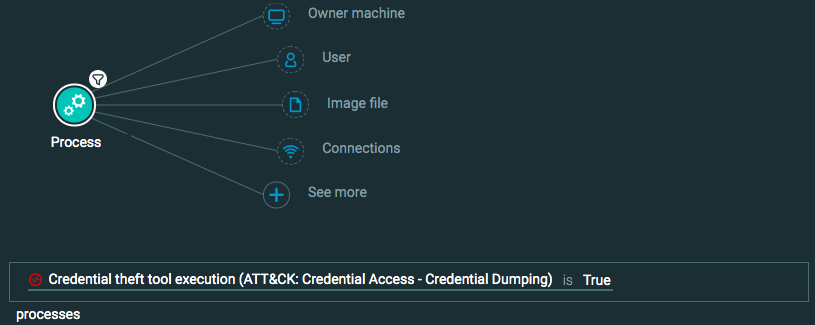
Query 2:
Process Element -> filter for Credential theft tool execution is True
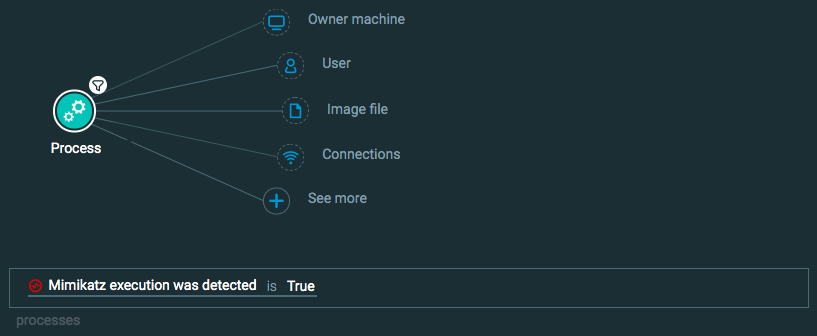
Query 3:
Process Element -> filter for Mimikatz execution was detected is True
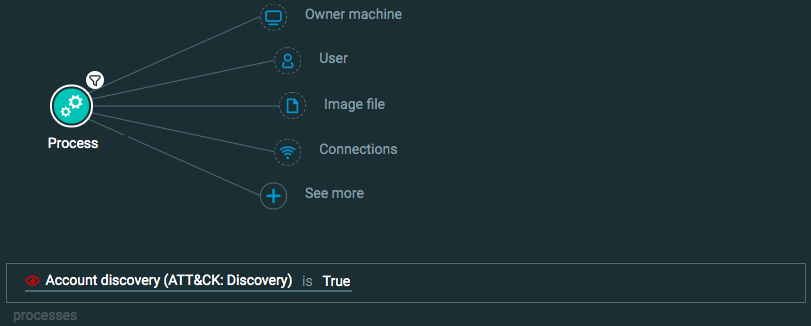
Discovery: Account Discovery
Goal: Find when an attacker is performing reconnaissance on a machine through trying to learn more about accounts on the machine.
Explanatory statement: I want to find examples of processes performing account discovery.
Construct this query:
Process Element -> filter for Account discovery is True
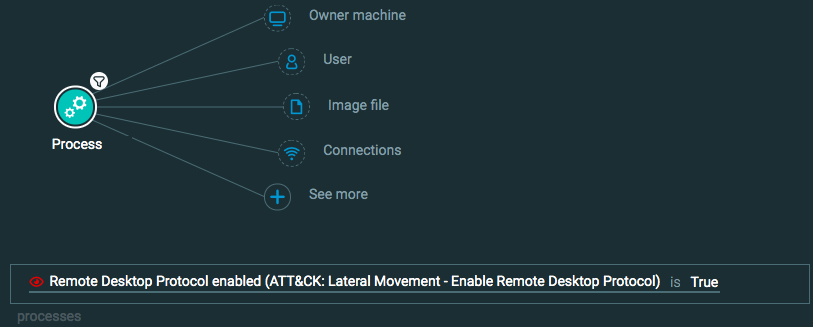
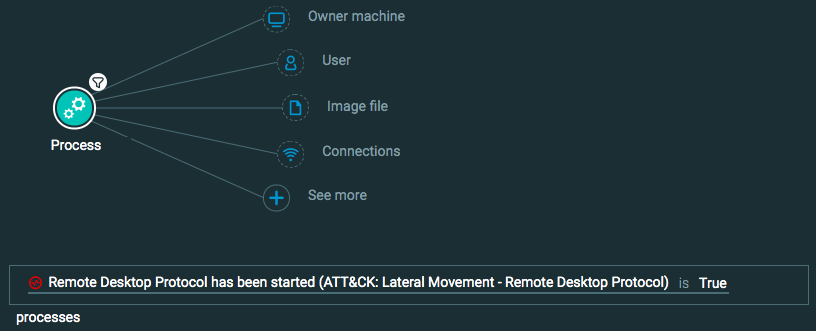
Lateral Movement: Remote Desktop Protocol
Goal: Find use of the Remote Desktop Protocol to move through the network.
Explanatory statement: I want to find examples of when the Remote Desktop protocol was used in my environment.
Construct one of the following queries:
Query 1:
Process Element -> filter for Remote Desktop Protocol enabled is True
Query 2:
Process Element -> filter for Remote Desktop Protocol has been started is True
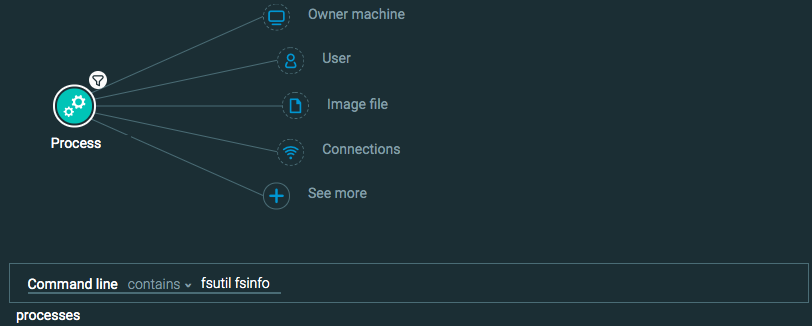
Collection: Data from Local System
Goal: Find attackers collecting information from the local file system.
Explanatory statement: I want to find examples of commands used for collection of information from the local file system.
Construct this query:
Process Element -> filter for Command line is fsutil
Note there are other commands used for collecting information from the file system. This is an example of a common one, but you can substitute other commands in this query as needed.
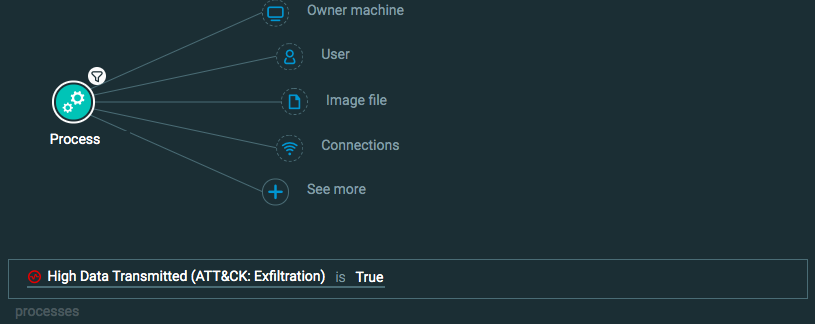
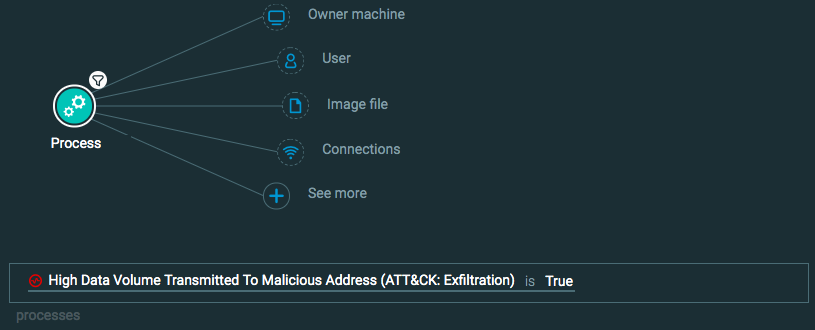
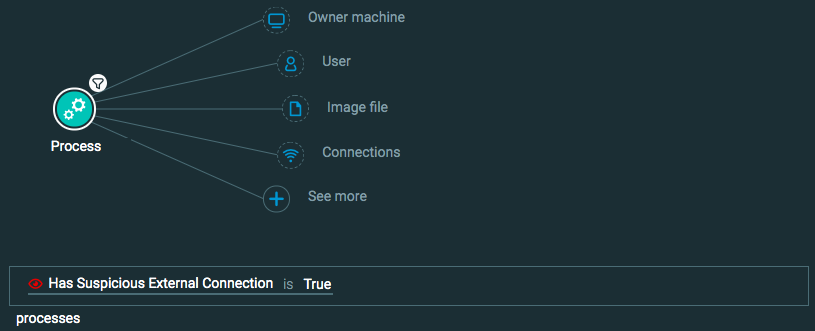
Exfiltration: Exfiltration over Command and Control Channel
Goal: Find data being sent over a command and control connection.
Explanatory statement: I want to find examples of data theft through command and control through instances of a large amount of data being transmitted to questionable addresses.
Construct one of the following queries:
Query 1:
Process Element -> filter for High data transmitted is True
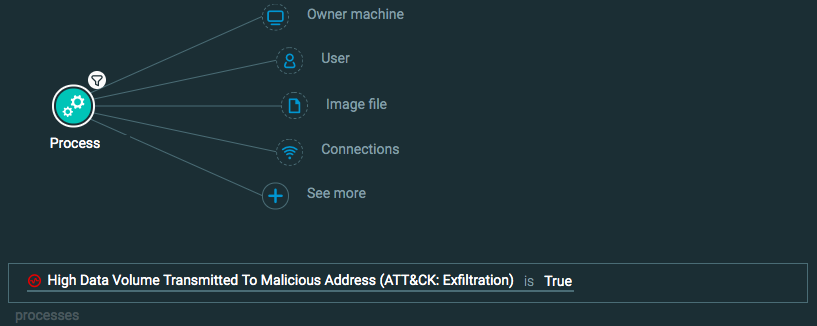
Query 2:
Process Element -> filter for High Data Volume Transmitted to Malicious Address is True
Query 3:
Process Element -> filter for Has suspicious external connection is True
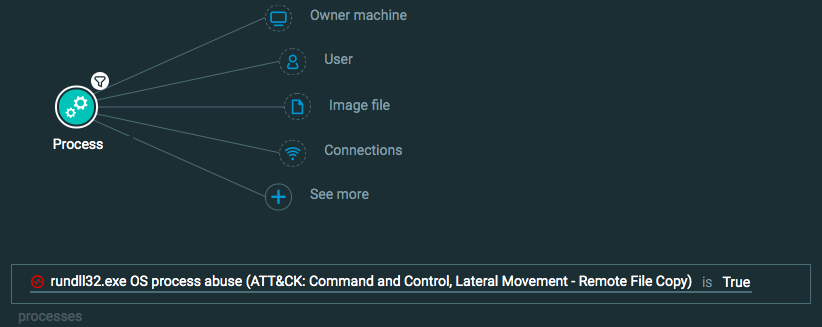
Command and Control: Remote File Copy
Goal: Find a process using command and control to copy files from my environment.
Explanatory statement: I want to find instances of specific processes initiating connections that usually enable copying of files elsewhere.
Construct one of the following queries:
Query 1:
Process Element -> filter for rundll32.exe OS abuse is True
Query 2:
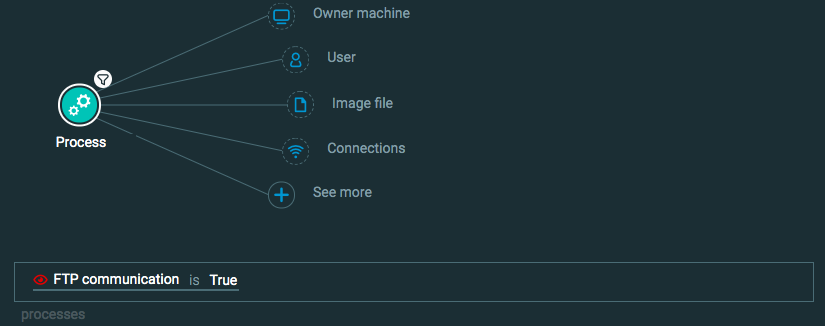
Process Element -> filter for FTP communication is True
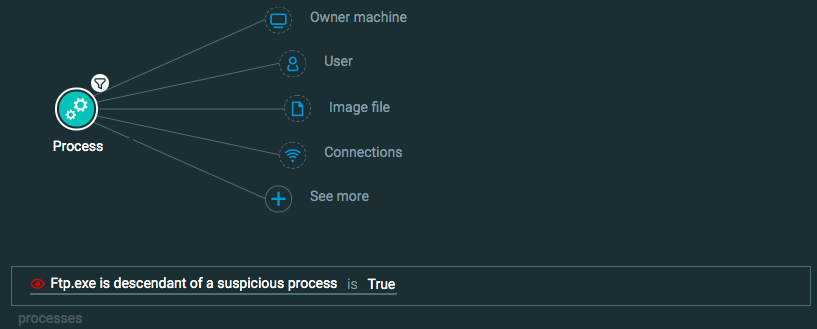
Query 3:
Process Element -> filter for Ftp.exe is descendant of suspicious process is True
Query 4:
Process Element -> filter for High Data Volume Transmitted to Malicious Address is True