Ransomware Malops
There are multiple MalOps related to Ransomware:
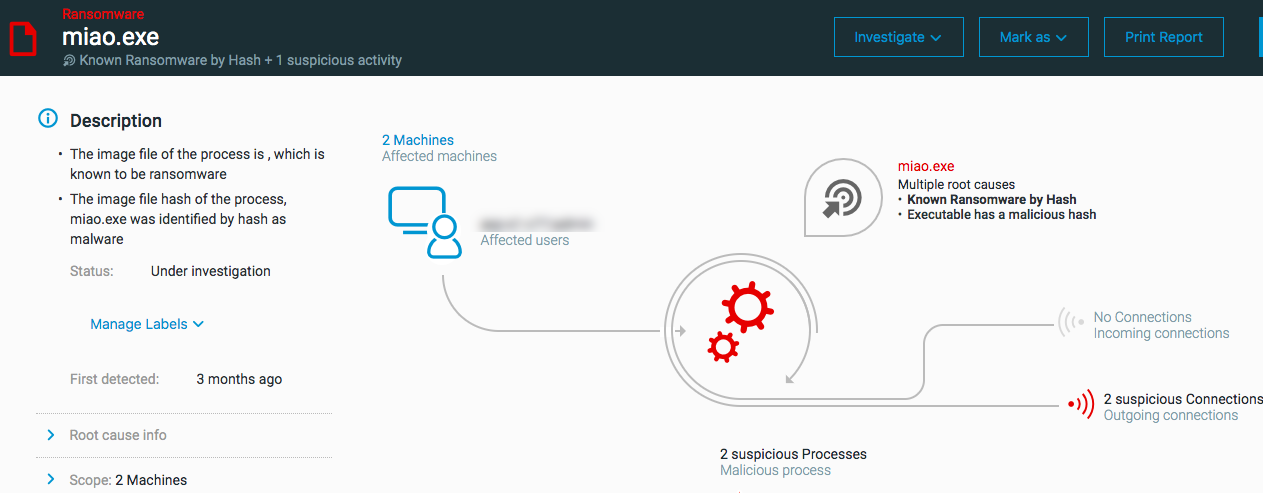
The ‘Cybereason Threat Intelligence identified a loaded module as ransomware’ MalOp is triggered when a process loads a module identified as ransomware by Cybereason Threat Intelligence.
The ‘Cybereason Threat Intelligence identified an executable as Ransomware’ MalOp is triggered when the image file of a process is identified as ransomware by Cybereason Threat Intelligence.
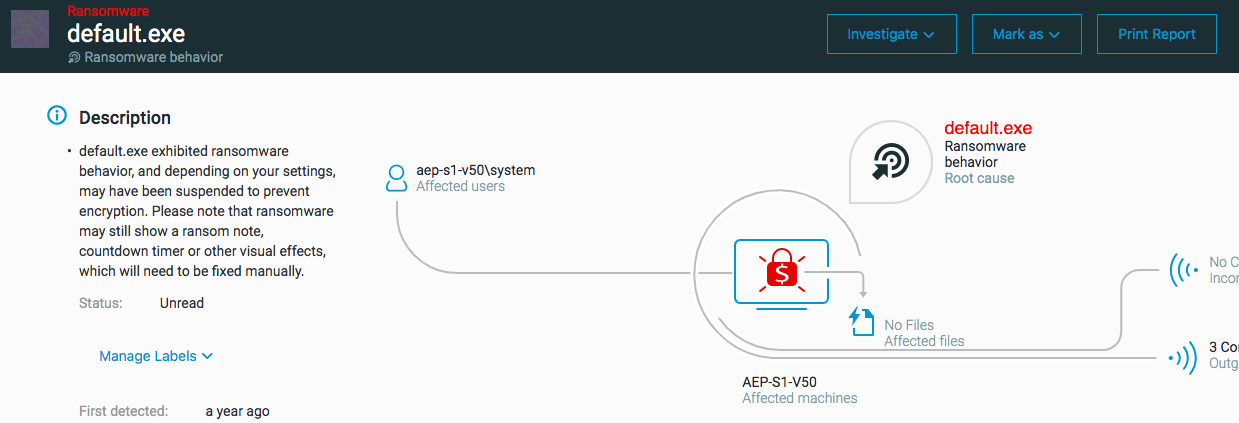
The ‘Ransomware behavior’ MalOp is triggered when the process is found to be performing behavior indicative of ransomware, such as encrypting files, attempting to delete backups, and so forth.
Ransomware detections include behaviors seen in known ransomware or characteristics of known ransomware. The Cybereason platform detects instances where a file, process image file, or a module is classified as ransomware by threat intelligence and instances where processes exhibit behavior similar to ransomware.
These MalOps are part of the Verified group.
Supported OS for the Cybereason Threat Intelligence identified an executable as ransomware Malop and Cybereason Threat Intelligence identified a loaded module as ransomware: Windows, Mac OS, and Linux
Supported OS for the Ransomware behavior Windows
Examples of behavior that can trigger this MalOp:
Identification of a hash value for a file or module as ransomware by Cybereason Threat Intelligence
Ransomware behavior of processes, such as file encryption, shadow copy deletion, or Master Boot Record infection
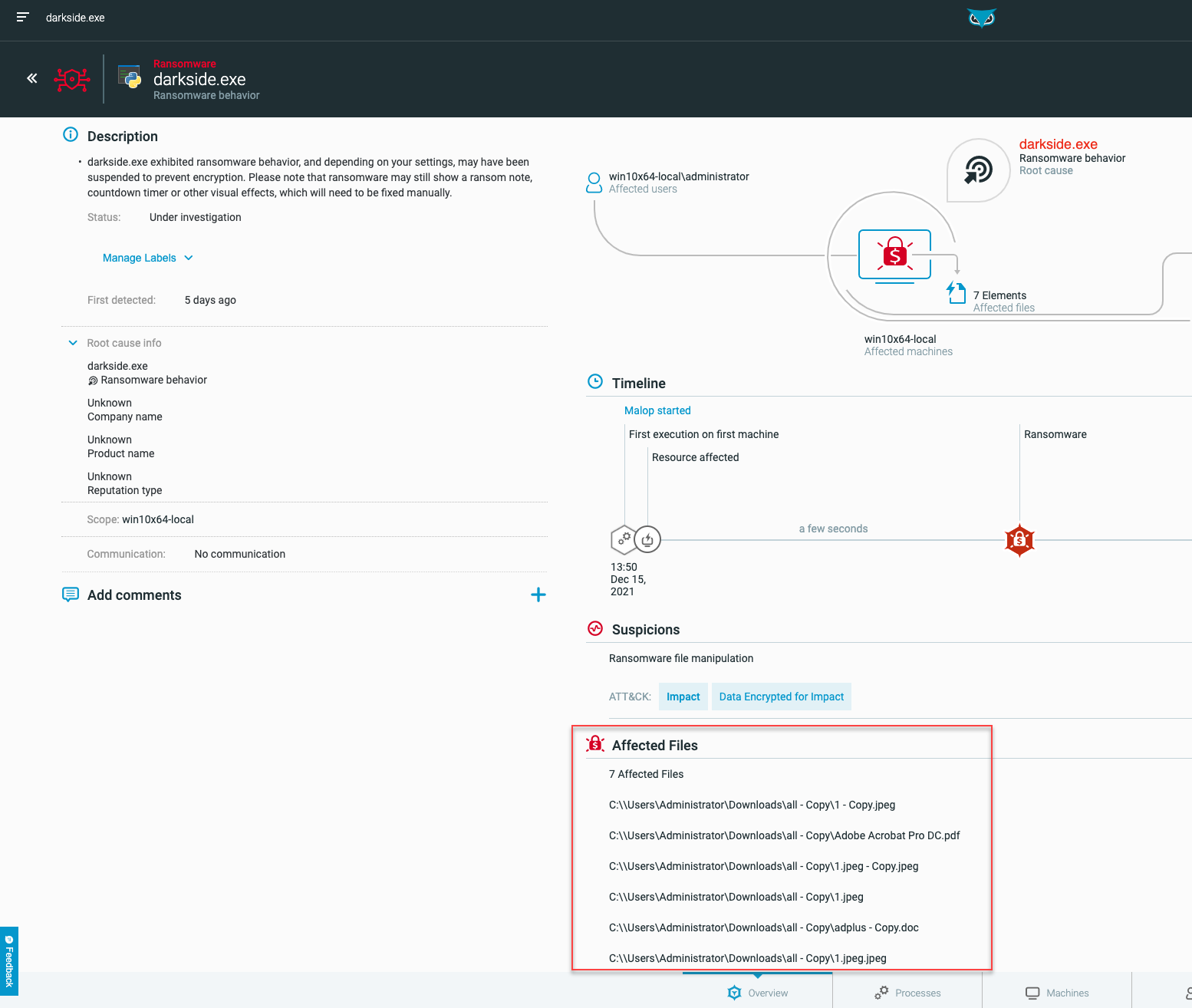
In version 21.2.26x and later, the ‘Ransomware behavior’ MalOp displays a list of files affected by the ransomware. For example:
Next steps
Investigate the process, module, or file depending on what the detection was raised on
Adjust your Anti-Ransomware protection in your Security Profile and on the Sensors as needed to stop the files.
Remediate the file if it has been suspended on the machine.