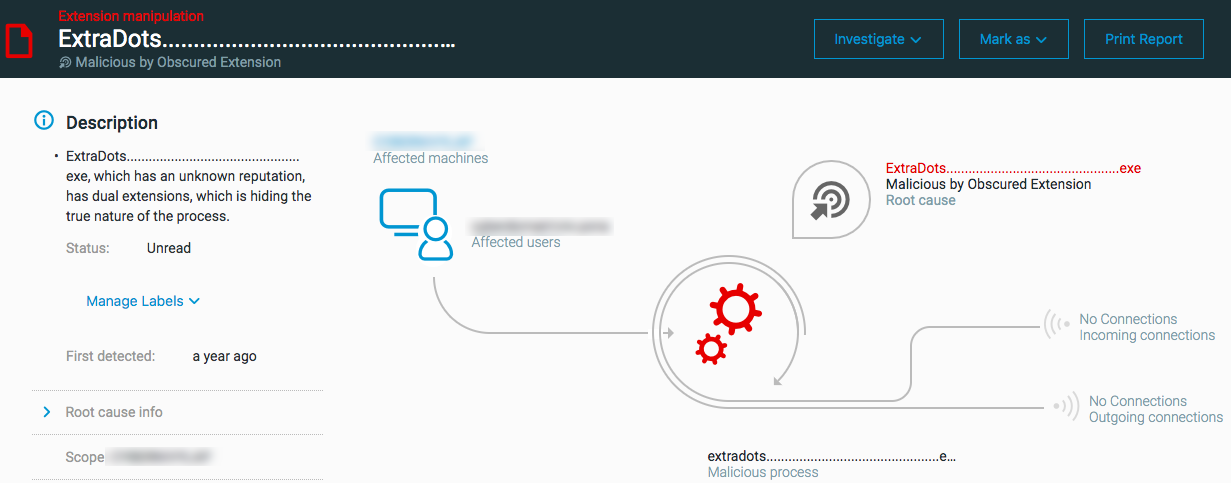
Extension Manipulation MalOps
The MalOp for ‘Malicious by Obscured Extension’ is triggered when a file is found to mask its true extension with multiple extensions. File extension manipulation includes changing file extensions to mask certain behaviors.
This MalOp is part of the Verified group.
Supported OS for this MalOp: Windows and Mac OS
Examples of behavior that can trigger this MalOp:
Dual or multiple extensions on a file
Obscured file extensions
Use of non-executable file extensions on processes
Exploitation of the right-to-left file vulnerability on Windows machines
Masquerading as other file types (like movie files)
Next steps
Investigate the process and file in question.
Examine the process hierarchy to find out what other activities the process is performing.
Check the process hash value against threat intelligence sources.
Check the process for unauthorized network connections.
Investigate to see if there are registry entries associated with the file. Use a query of Malop Process Element -> Suspicious Process Element -> Registry Entry Element to find a process that corresponds to the file.