Remote Shell Utility Use-Case - Unrestricted Mode
The following is a sample use case for how to use the Remote Shell utility in Unrestricted mode. The Remote Shell utility enables you to respond to and remediate malicious activity and MalOps on a single machine.
As an analyst, you want to download a script from the internet and run it using the Remote Shell.
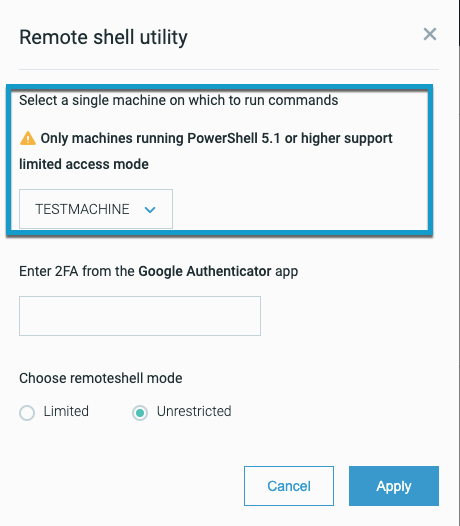
Starting from the Cybereason UI, from the MalOp Details screen, you click Remote Shell. You are then prompted to select your machine:
You also enter your two-factor authentication code.
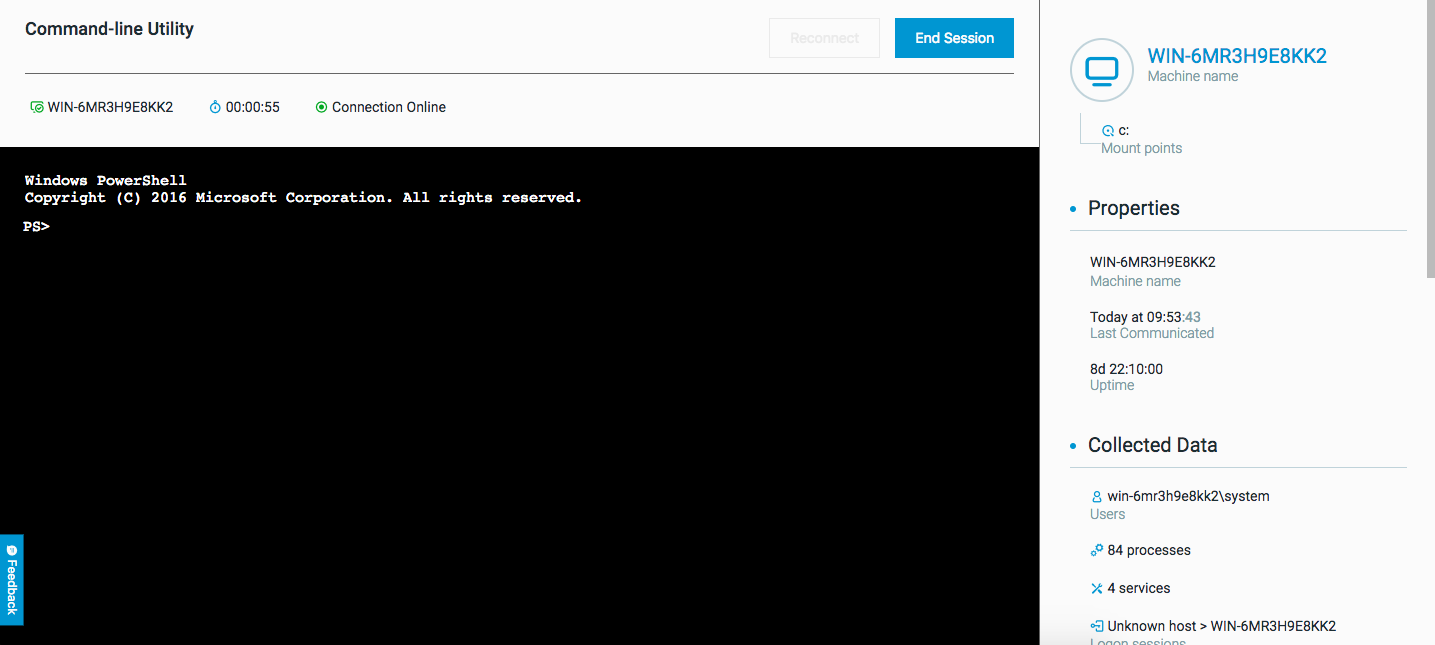
The Remote Utility screen opens directly in the Cybereason platform screen.
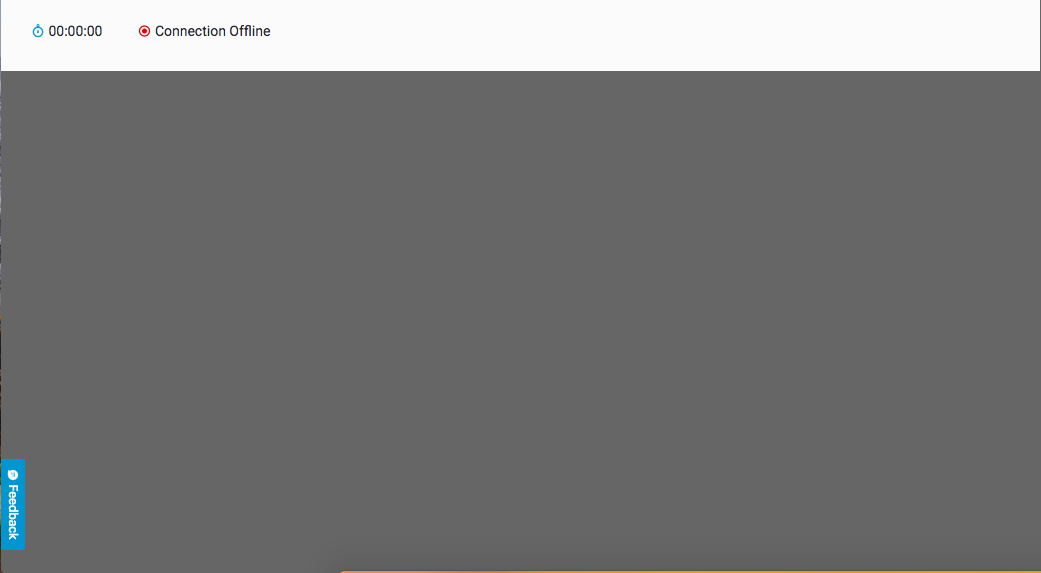
At first, the command line window is empty, without a cursor. This is because your Cybereason server is establishing the connection between itself and the machine and the connection:
Once the status at the top of the window changes to Online, the cursor appears and the command line is ready to use.
To download the script, you run the following command:
Invoke-WebRequest -Uri $url -OutFile $output" (For example : Invoke-WebRequest -Uri "https://www.robvanderwoude.com/files/memory_ps.txt" -OutFile "script.ps1
In addition, you run the following command to enable script execution (a PowerShell requirement):
Set-ExecutionPolicy -ExecutionPolicy Unrestricted
Then, you run the downloaded script using regular PowerShell execution. The script runs and the results return automatically.
If necessary, you can run the following command to block script execution when you are finished:
Set-ExecutionPolicy Restricted
In addition, you would like to take a memory dump from the machine to investigate more. Run the following command:
Powershell -c rundll32.exe C:\Windows\System32\comsvcs.dll, MiniDump 6840 c:\\Temp\\my_dump_file.bin mini
The Remote Shell utility performs the memory retrieval and saves the information to the specified file (my_dump_file.bin).