Use the Remote Shell Utility (Secure Mode) - Use-Case
The following is a sample use case for how to use the Remote Shell utility. The Remote Shell utility enables you to respond to and remediate malicious activity and MalOps on a single machine.
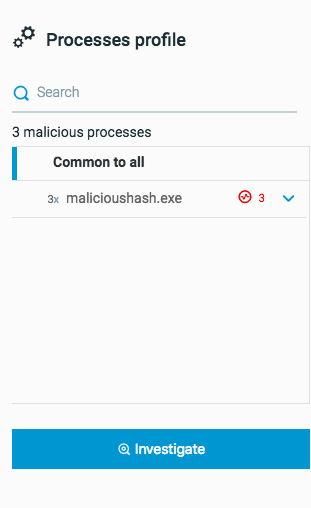
As a analyst, you are investigating a Pass the Hash MalOp. As part of the analysis, you decide to investigate the source process of the MalOp.
In the Malop Details screen, you expand the list of processes, and click Investigate to view details on this process.
From your investigation, you conclude:
This process created a registry autorun key and a scheduled task to persist the process
The process opened the command window (cmd.exe) and the wscript.exe program multiple times.
As a result, you conclude that the process has probably created and run several scripts on the machine. While the built-in remediation options will also help stop the damage this process has done, you want to explore further and investigate the machine in a more in-depth manner.
To do this, you use the Remote Shell utility.
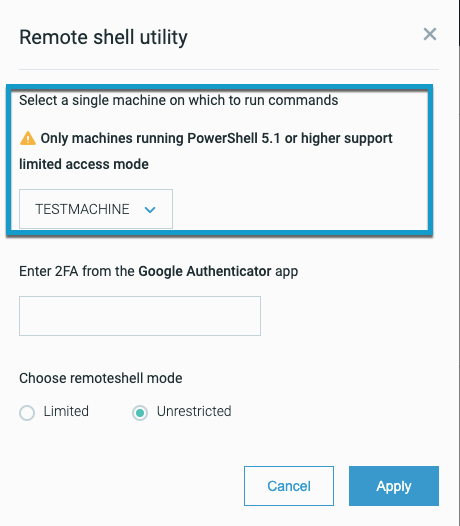
In the Investigation screen, click Remote Shell. You are then prompted to select your machine:
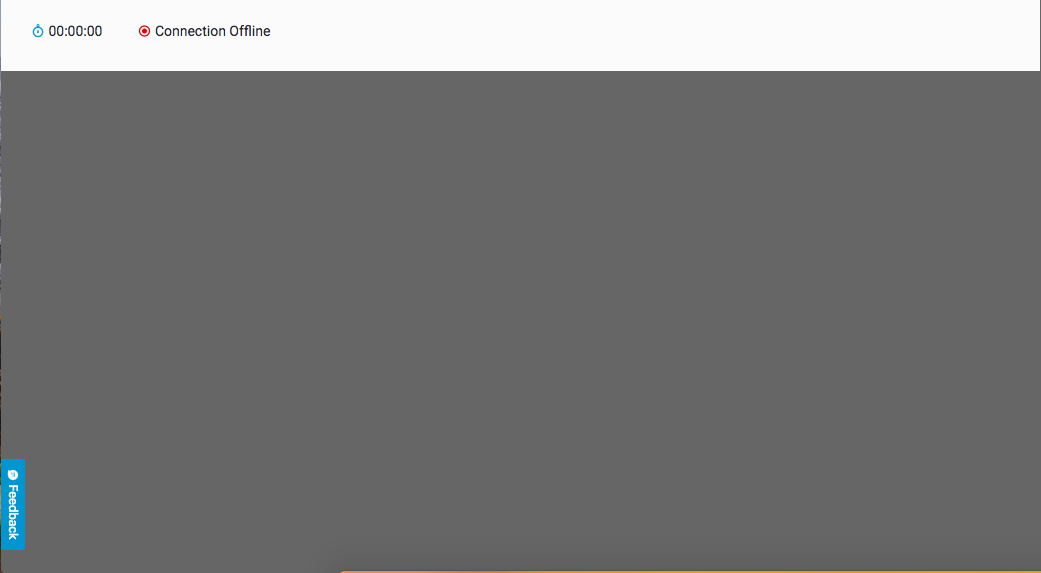
The Remote Utility screen opens directly in the Cybereason platform window.
At first, the command line window is empty, without a cursor. This is because your Cybereason server is establishing the connection between itself and the machine and the connection:
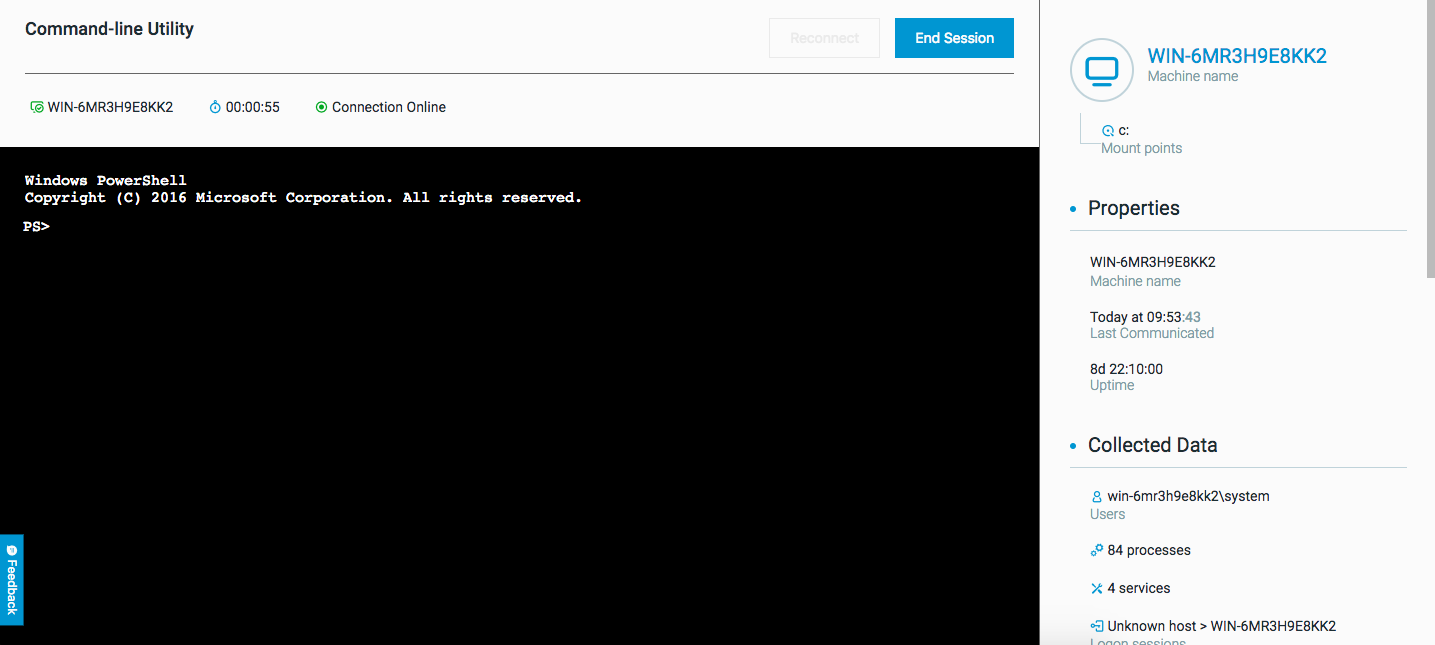
Once the status at the top of the window changes to Online, the cursor appears and the command line is ready to use.
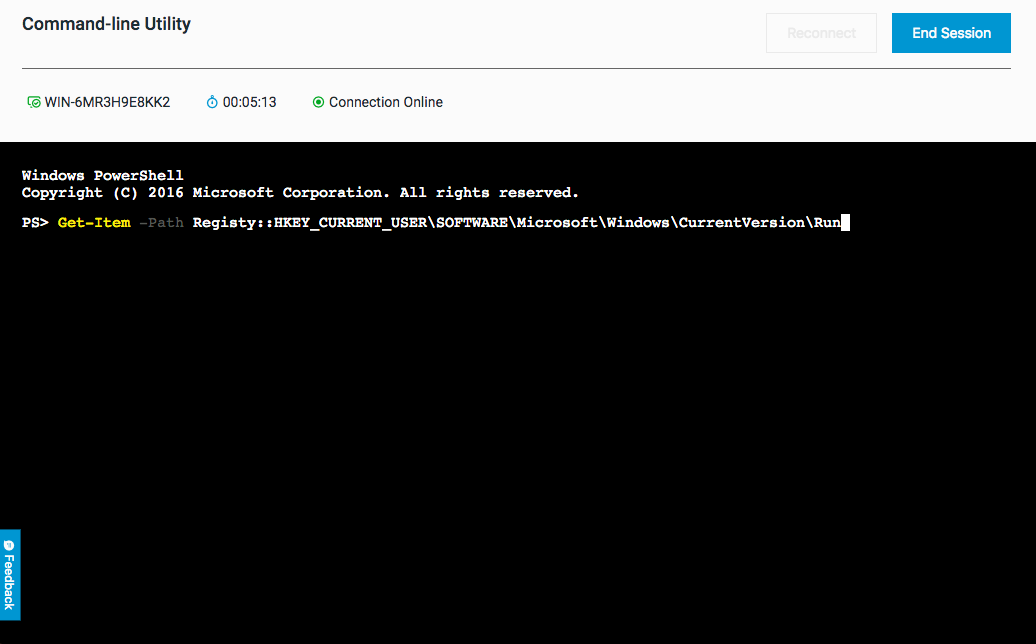
Because you remember that the process in question created a number of registry entries, you run the command to list the registry entries from the key the process used:
Get-Item -Path Registry::HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run
The command returns the list of registry entries created. You read the list of commands and find the ones the process created.
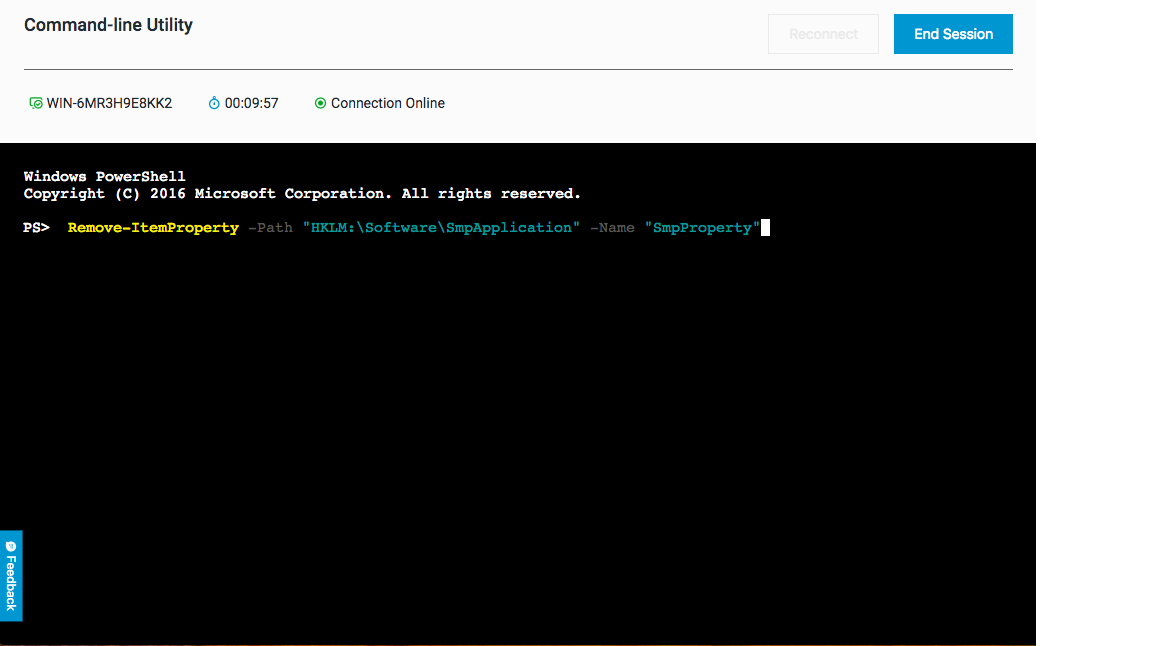
Then, you run a command to delete the necessary entries:
Remove-ItemProperty -Path "HKLM:\Software\SmpApplication" -Name "SmpProperty"
You also do the same for the scheduled tasks the process created.
You then go to the folder containing the malicious file that runs the process is located. Using the Windows API you quarantine the file and explore other files in the same directory. Since you find a number of them worth further investigation, you compress the files into zip file.
After you finish, you return to the Remote Shell window and click End Session to close the connection.
Back in the Cybereason UI, you use the File Search window to locate and download the files.
Your Cybereason WebApp server saves a record of all commands used and responses to the server logs. Users with the System Admin role can retrieve these logs after a session is complete. Sensor logs note any connections to the machine from the Remote Shell utility and system changes such as file modification, etc.).