Communication Between Components
As part of their standard activity, the different components in the Cybereason platform frequently communicate with each other to share and sync data to ensure that the platform shares the full information for detection and asset management purposes. Each of the servers communicate with each other, and also with the endpoint machine servers.
Communication between servers and sensors in the Cybereason platform takes place over TLS. Depending on how you configure your environment, communications go through port 443 or 8443. Communication between the WebApp server and the Global Threat Intel server always goes through port 443. For the purposes of this documentation, we assume the following configuration:
Sensors and Detection servers communicate through port 443.
Detection servers and WebApp server communicate through port 8443.
This topic details the various types of communication between the different platform components.
In this topic:
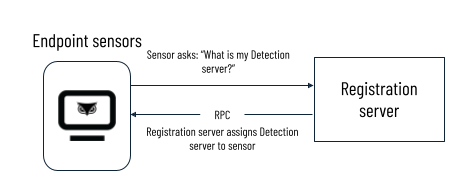
Sensors to Registration server
The sensors connect to the Registration server on initial connection. Each sensor asks the Registration server with which Detection server it should communicate. The Registration server uses a capacity-aware round-robin load balancing method to assign sensors to Detection servers. The Registration server communicate the assignments back to the sensor through a Remote Procedure Call.
Sensors contact the Registration servers after installation only if they have issues communicating with their assigned Detection server.
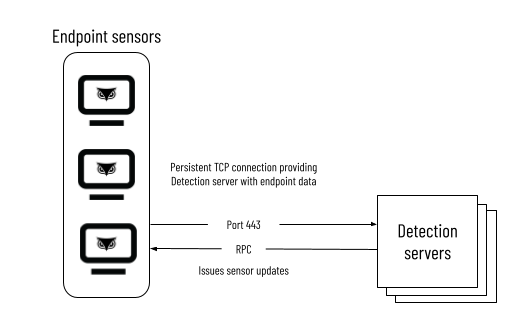
Sensors to Detection servers
Sensors communicate with their Detection server through port 443 via proprietary bi-directional RPC protocol over a persistent TCP connection. The Detection servers can throttle the amount of data sensors send to avoid overload. Throttled data is resent again. In addition, the sensors send only the changes in the data, in chunks at various times. If sensors require an update, the Detection server issues the update (which it pulled from the Update server) to the sensor through a Remote Procedure Call. The Detection server is also tasked with stopping or starting sensor data collection.
Note
In the Cybereason platform, Detection servers do not communicate directly with each other.
The sensors and Detection server communicate through different methods depending on whether or not your configuration includes a Registration server, as illustrated in the following table:
Registration server |
Communication method |
|---|---|
Yes |
Sensor contacts the Registration server, which assigns the sensor to a Detection server. |
No |
Sensor communicates directly with the Detection server that was provided as part of the installation package. |
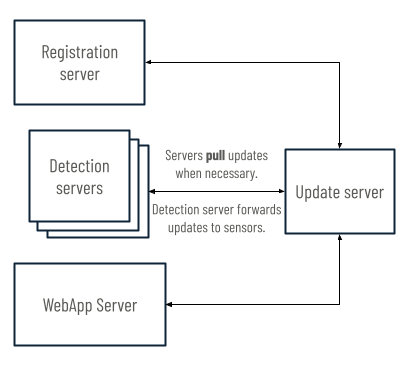
Update server to other servers
All Cybereason customers share the Global Update server. This server also hosts any updates for the Cybereason platform. To avoid unwanted system changes, updates are not automatically deployed to Cybereason servers and sensors. Instead, the Detection servers, Registration server, and WebApp server can pull updates from the Global Update server when necessary.
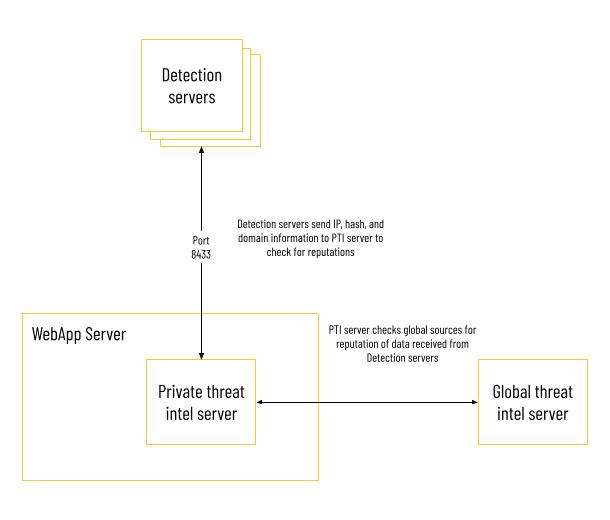
Detection servers to Global and Private Threat Intel servers
For the Cybereason platform to leverage threat intelligence services, the Detection servers need to send sensor information to the Private Threat Intel server. The Detection servers send IP, hash, and domain information to the Private Threat Intel server, which checks the data against the organization’s personal blocklist and allowlist.
If the Private Threat Intel server does not respond with a definitive classification for the data from the Detection server, it checks the data against the external Global Threat Intel server, which hosts globally-recognized malware information.
24 hours after an entity was checked, the Cybereason platform rechecks the IP, hash, or domain against the threat intelligence resources to verify the classification is current.
Detection servers to WebApp server and Microservices
The WebApp server retrieves information from the Detection servers when a user performs an action in the UI. The Detection servers send sensor data to the Private Threat Intel server. The UI receives data from the database. Microservices communicate with Detection servers and the WebApp server. Microservices perform MalOp decision-making, asset tagging, and sensor management.
Note
Cybereason opens port 7075 on Detection servers for communication with the WebApp server on malware information.
See Platform Architecture for more information about the Cybereason platform’s architecture.