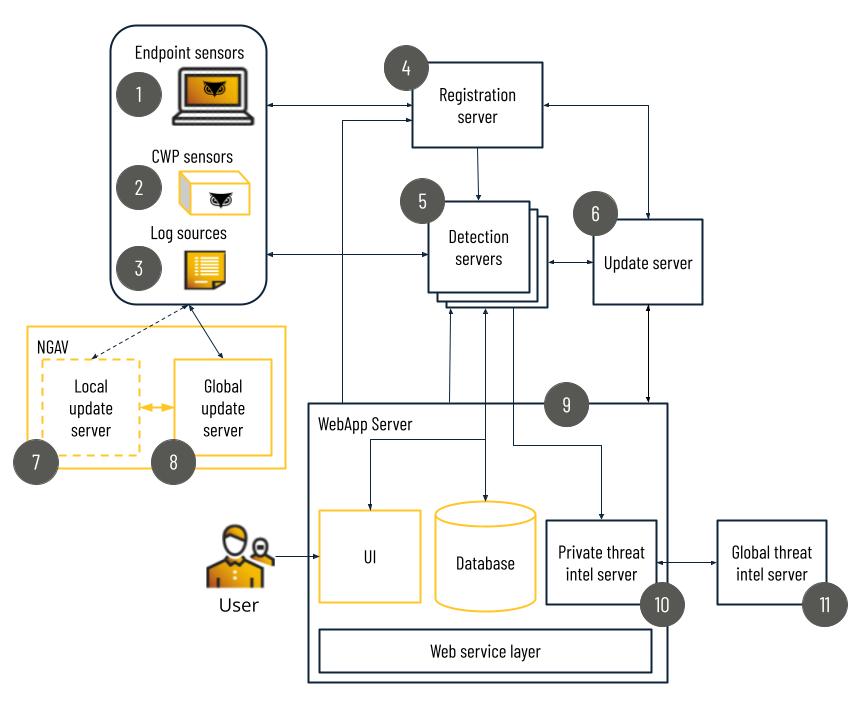
Platform Architecture
Several different components power the Cybereason platform. These components collect and analyze data, detect potentially malicious activity, and enable you to manage your platform assets.
Note
If you are using the new Data Platform model, see the architecture articles in the Data Platform Documentation.
In this topic:
Architecture overview
The following provides a high-level overview of each part of the Cybereason platform.
Note
The NGAV components in the diagram apply to deployments in which you enable the Anti-Malware > Signatures mode.
To learn about how the different pieces of the Cybereason platform communicate, see Communication Between Components.
Data collection components
Data collection components include sensors installed throughout your organization and connected integrations for log source data. The numbers in the following table refer to the diagram above.
Component |
Description |
|---|---|
1 - Endpoint sensors |
You install the endpoint sensor on machines in your organization. Sensors collect data about the events and operations that occur on each endpoint throughout your organization. Sensors send the collected data to Detection servers for analysis. For details, see Sensor Architecture. |
2 - Cloud Workload Protection (CWP) sensors |
You install CWP sensors on Docker containers and Kubernetes clusters in your organization. Like endpoint sensors, these sensors collect data about the events and operations that occur on Docker containers and Kubernetes clusters throughout your organization. The sensors send this data to the Detection server for analysis. |
3 - Log source integrations |
Using Cybereason Connect, you enable the Cybereason platform to retrieve and analyze log source data from numerous supported integrations. The Cybereason platform reads and analyzes specific parts of the logs and includes this data with other data in the Detection Server to find patterns of behavior across all parts of your organization and network. |
Management and analysis/detection servers
The Cybereason platform includes a number of servers that help you analyze collected data for patterns of behavior and manage your platform. The numbers in the following table refer to the diagram above.
Component |
Description |
|---|---|
4 - Registration server |
The Registration server enables you to perform load management for Detection servers by automatically assigning sensors to specific Detection servers. Upon installation, the Registration server maps sensors to Detection servers using a capacity-aware round-robin allocation method or the application of assignment rules you specify for sensors. When a sensor is assigned to a Detection server, the sensor maintains the connection with the Detection server and sends the sensor’s endpoint data to that Detection server Note A Registration server is installed for all customer deployments. However, for trials, it is possible to deploy the Cybereason platform without a Registration server. For more information about the Registration server, see Registration server FAQ. |
5 - Detection server |
Detection servers perform data collection, recording, and data analysis of the data received from the sensors. Detection servers use the built-in CMC Engine to collect, record, and analyze data from the sensors. The CMC Engine communicates with the Global and Private Threat Intel servers to determine the classification for all analyzed activity. In addition to the CMC Engine, each Detection server hosts a 1 TB partition containing the following:
Detection servers facilitate sensor management actions, such as starting or stopping data collection and updating software Work with Customer Success to deploy Detection and Registration servers. the Cybereason platform provisions Detection servers for cloud deployments, and assists with on-premises deployments. |
6 - Update server |
The Update server is shared among all customers and contains server and sensor update packages, new versions of the Cybereason platform, and security patches. So as not to interrupt your current working environment, your Detection, Registration, and WebApp servers retrieve the necessary data and software updates from the Update server when you choose to apply the updates. |
7 - NGAV Local update server |
If you use NGAV and have a large number of endpoints, you can install one or more NGAV Local Update servers in your network. This server delivers Anti-Malware signature updates to your organization’s endpoints more quickly, since it resides on the internal network. This capability can be especially significant during the first-time enabling of Anti-Malware > Signatures mode on sensors, during which the full signature database (~200 MB) is deployed to each endpoint. Using the NGAV Local update server can help to avoid potential traffic issues on the external network. You can install more than one NGAV Local update server if necessary. For more information about configuring the NGAV Local update server, see NGAV Local Update Server. |
8 - NGAV Global update server |
The NGAV Global update server is a Cybereason server in the cloud that delivers frequent signature updates to the Cybereason Anti-Malware > Signatures component on each endpoint. Important To allow communication with this server, see Enable communication with the Cybereason Global Update servers (all OSs). |
9 - WebApp Server |
The WebApp server contains a wide variety of data, including:
When you interact with the UI, the WebApp server queries the Detection servers for the necessary information. In this way, the WebApp server operates as a single management point for Cybereason components in your organization. |
10 - Private Threat Intel Server |
The Private Threat Intel server is specific to your environment. The server hosts your organization’s custom reputation information (allowlists and blocklists) and compares those settings with data it receives from the Detection servers. The Private Threat Intel server is also the platform’s link to outside intelligence sources. If the Private Threat Intel server does not make a definitive judgment on data received from the Detection servers, it queries the Global Threat Intel server, which contains globally-recognized information on malware. Results received from the Global Threat Intel server are recorded in the Private Threat Intel server for 24 hours, eliminating the need to repeatedly query remote sources about the same information in a short period of time. 24 hours after an entity was checked, Cybereason rechecks the IP, hash, or domain against the threat intelligence resources to verify the classification is current. |
11 - Global Threat Intel server |
Cybereason uses a shared Global Threat Intel server to compare data in your in-memory graph to globally recognized threat sources to determine the reputation of a given file, IP address, or domain. The Global Threat Intel server is updated daily, ensuring your data is checked against the most recent threat information in the cybersecurity industry. The Global Threat Intel server uses artificial intelligence algorithms running on live global intel data to determine if objects are malicious or benign and categorize them accordingly. Information gained from the Global Threat Intel server is fed to your Private Threat Intel server, which communicates the findings to your Detection servers. 24 hours after an entity was checked, Cybereason rechecks the IP, hash, or domain against the threat intelligence resources to verify the classification is current. |
Server overview videos
The following video describes the Cybereason Detection and Registration servers:
The following video describes the Threat Intel servers:
Microservices
Microservices perform MalOp decision-making, asset tagging, and sensor management. This enables a more distributed component layout and improves scalability making future versions of Cybereason more efficiently and reliable for upgrades.
Cybereason installs and manages microservices for Cloud customers. For information regarding microservers for on-premises servers, contact Customer Success.