Syslog Messages - Events and Severity
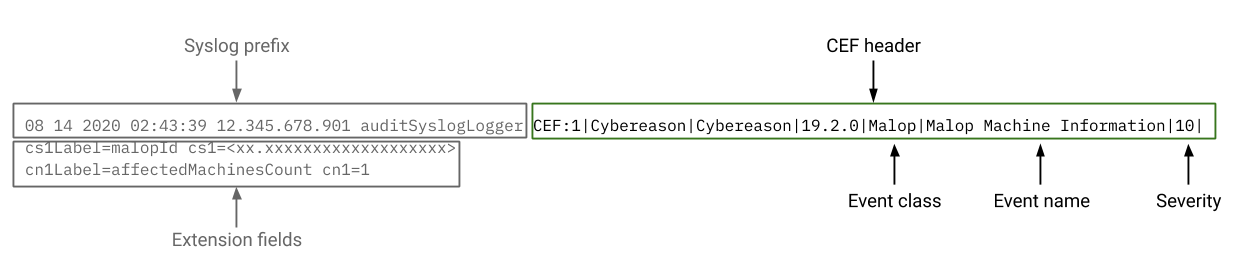
In the syslog message, the CEF header contains the Event class and **Event name fields that describe the event that caused the Cybereason platform sto send a message via syslog.
In the same header, the Severity field lists the relative severity of the event.
In this topic:
Events reported in the syslog
The syslog contains details on a number of events from the Cybereason platform, including:
Login and log out from the platform
Creation of MalOps and malware alerts
Performance of Malop remediation acations
Creation of Behavioral allowisting rules and custom detection rules
Detections from custom detection rules
Sensor policy changes
Sensor setting changes
Remote Shell sessions
Investigation query use
File search operations
Creation of sensor policies and sensor groups
Creation of platform users
See the sections below for the event classes and events for these events.
Event classes
In the header, the Event class field lists a category for the event.
The following Event classes are possible in the syslog:
MALOP
MALWARE
USERACTION
Event names
The Event name field describes the specific event for this syslog message. The following tables list Event names by Event class, along with descriptions of the event that triggered the message.
MalOp event class event names
Event name |
Triggering action |
|---|---|
Malop Created |
The Cybereason platform created a new MalOp. |
Malop Updated |
The Cybereason platform updated an existing MalOp. |
Malop Machine Information |
The Cybereason platform created a new MalOp was created or updated an existing MalOp. |
Malop Updated Machine Information |
The Cybereason platform updated an existing MalOp was updated with new machine information (e.g. new machines added to Malop). The Cybereason platform adds a separate syslog message for each machine associated with the updated MalOp. Note Contact Technical Support to enable this reporting. |
Malware event class event names
Event name |
Triggering action |
|---|---|
Malware Created |
The Cybereason platform created a new malware alert. |
Malware Updated |
The Cybereason platform updated an existing malware. |
UserAction event class event names
The UserAction event class categorizes user events into action groups. Action groups are noted in the event name field of the CEF header, followed by a slash and the event name, as seen in the following example:
CEF:0|Cybereason|Cybereason|2016.5.4|UserAction|MALOP_INVESTIGATION/ChangeMalopState|0|
BEHAVIORAL WHITELISTING action group
Event name |
Triggering action |
|---|---|
AddRule |
A Cybereason user adds a behavioral allowlisting rule. |
EditRule |
A Cybereason user edited a behavioral allowlisting rule. |
UpdateRuleStatus |
A Cybereason user updated the status of a behavioral allowlisting rule. |
ListRules |
The list of rules was retrieved. |
RuleData |
The rule data for a rule was retrieved. |
MatchTest |
A Cybereason user requested to see if a rule matched. |
Preview |
A Cybereason user requested to see the effect of a behavioral whitelisting rule on existing MalOps. |
ListEvents |
The list of events was retrieved for this rule. |
CUSTOM RULES action group
Event name |
Triggering action |
|---|---|
RuleCreated |
A Cybereason user created a custom rule. |
RuleUpdated |
A Cybereason user updated a custom rule. |
DETECTION RULES action group
Event name |
Triggering action |
|---|---|
SuspicionCreated |
The Cybereason platform created a new suspicion based on logic defined in a custom rule. |
DecisionFeatureCreated |
The Cybereason platform created a new decision feature based on logic defined in a custom rule. |
SuspicionUpdated |
The Cybereason platform updated a suspicion generated by a custom rule. |
DecisionFeatureUpdated |
The Cybereason platform updated a Decision feature generated by a custom rule. |
GENERAL action group
Event name |
Triggering action |
|---|---|
Login |
User logs into the Cybereason platform. |
Logout |
User logs out of the Cybereason platform. |
NotificationSettingChange |
User changed their notification settings. |
ChangePassword |
User changed their password. |
ChangeConfigurationSettings |
User changed their configuration settings. |
ChangeConfigurationDetails |
User changed the configuration settings. |
CollectionConfigurationOverride |
User updated a sensor data collection setting. |
CollectionConfigurationOverrideDetails |
User updated a sensor data collection setting. |
CollectionConfigurationOverrideSensor |
User updated a sensor data collection setting. |
RegistryEventsInclusionAdd |
User added a registry events collection inclusion in the Collection configuration section of a sensor policy |
RegistryEventsInclusionModify |
User edited a registry events collection inclusion in the Collection configuration section of a sensor policy |
RegistryEventsInclusionKeep |
User kept a registry event collection inclusion in the Collection configuration section of a sensory policy |
RegistryEventsInclusionDelete |
User deleted a registry events collection inclusion in the Collection configuration section of a sensor policy |
IRToolsDownloadResults |
User downloaded the results from an IR tool execution |
IRToolsDownloadResultsSensor |
User downloaded the results from an IR tool execution |
IRToolsRunCommand |
User ran an IR tool on one or more endpoint machines. |
IRToolsRunCommandSensor |
User ran an IR tool on one or more endpoint machines. |
Note
For the login and logout events, the machineName field will occasionally list the machine’s IP address instead of the machine name.
INVESTIGATION action group
Event |
Triggering action |
|---|---|
DeleteQuery |
User deleted a previously saved investigation query. |
saveQuery |
User saved a investigation query. |
EditQuery |
User edited a saved investigation query. |
Query |
User ran an investigation query. |
FileSearchQuery |
User performed a file search operation. |
GetFile |
User requested to download a file from investigation query results. |
BrowseFolder |
User browsed folders on an endpoint machine from investigation query results. |
MALOP INVESTIGATION action group
Event name |
Triggering action |
|---|---|
ChangeMalopState |
MalOp state was changed due to a change in the MalOp investigation status (for environments using the new Data Platform infrastructure or MalOp status (for environments not using the new Data Platform infrastructure). |
Remediation |
User performed a remediation action for a MalOp. |
RemediationDetails |
User performed a remediation action for a MalOp. |
MachineIsolation |
User isolated a machine associated with a MalOp. |
MachineIsolationDetails |
User isolated a machine associated with a MalOp. |
MalopComment |
User added a comment in a MalOp. |
AbortRemediation |
User stopped a remediation action for a MalOp. |
ManualCustomReputations |
User changed the reputation of an item in the MalOp details. |
CustomReputationsDetails |
User changed the reputation of an item in the MalOp details. |
StopMachineIsolation |
User removed the isolation of a machine associated with a MalOp. |
StopMachineIsolationDetails |
User removed the isolation of a machine associated with a MalOp. |
DeleteMalopComment |
User deleted a comment from a MalOp. |
GenerateReport |
User generated a MalOp PDF report. |
GetFile |
User downloaded, retrieved, or aborted retrieval of a file from the MalOp details. |
GetFileDetails |
User downloaded, retrieved, or aborted retrieval of a file from the MalOp details. |
MalopInboxAccess |
User accessed the Malop inbox screen. |
CreateMalopLabel |
User created a new MalOp label. |
AddMalopLabel |
User added a label to a MalOp. |
RemoveMalopLabel |
User removed a label from a MalOp. |
REMOTE SHELL action group
Event name |
Triggering action |
|---|---|
Connect |
User used the Remote Shell utility to connect to an endpoint machine. |
Disconnect |
User ended a Remote Shell utility session. |
UserInput |
User ran a command in the Remote Shell utility |
SECURITY PROFILE action group
Event name |
Triggering action |
|---|---|
PowerShellProtectionMode |
User changed the Fileless protection mode in the Fileless Protection section of a sensor policy. |
PowerShellDownloadAndExecuteMode |
User changed PowerShell Download and Execute mode in the Fileless Protection section of a sensor policy. |
PowerShellMaliciousDownloadsMode |
User changed PowerShell Malicious Downloads mode in the Fileless Protection section of a sensor policy. |
PowerShellScriptAnalysisMode |
User changed PowerShell Script Analysis mode in the Fileless Protection section of a sensor policy. |
PowerShellScriptAnalysisExclusions |
User added or updated an exclusion for the PowerShell Script Analysis mode in the Fileless Protection section of a sensor policy. |
PowerShellProcessExclusions |
User added or updated process exclusions in the Fileless Protection section of a sensor policy. |
DotNetFloatingModulesMode |
User changed the .NET floating modules mode in the Fileless Protection section of a sensor policy. |
SENSOR MANAGEMENT action group
Event name |
Triggering action |
|---|---|
ManualArchiveInvoked |
User manually archives a sensor. |
ManualUnarchiveInvoked |
User manually removed a sensor from archive. |
SensorArchived |
Sensor was automatically archived due to platform settings. |
SensorUnarchived |
Sensor was automatically removed from archive due to platform settings. |
SensorDeleted |
Sensor was removed from list of sensors in the Sensors screen |
ManualDeleteInvoked |
Sensor was manually removed from list of sensors in Sensors screen. |
SensorDecommissioned |
Sensor was automatically decommissioned due to platform settings |
ManualDecommissionInvoked |
User manually decommissioned a sensor. |
ManualRevertDecommissionInvoked |
User manually restored a sensor from the Decommissioned state. |
SensorRevertDecommission |
Sensor was automatically restored from the Decommissioned state. |
SettingsChanged |
A sensor setting was updated. |
SensorStatusSettingDetails |
User updates settings for the automatic moving of sensors to stale and/or archived status. |
EntityTagsCsvUpload |
User uploads a CSV file with sensor tags. |
EntityTagsCsvSubmit |
User submits a previously uploaded CSV with sensor tags. |
EntityTagsAPISubmit |
User calls the upload tags API. |
EntityTagsApiCalled |
The list of sensor tags was retrieved. |
EntityTagsEvent |
User modifies an entity tag. |
ManualAntiMalwareModesInvoked |
User sets the Anti-Malware modes on a single sensor in the Sensors screen. |
SensorAntiMalwareModesPreview |
User updates the Anti-Malware modes on a single sensor in the Sensors screen. |
CreatePolicy |
User creates a sensor policy. |
AssignPolicy |
User assigns a sensor to a policy. |
UpdatePolicy |
User updates a sensor policy. |
DeletePolicy |
User deletes a sensor policy. |
CreateGroup |
User creates a sensor group. |
AddSensorsToGroup |
User adds one or more sensors to a group. |
RemoveSensorsFromGroup |
User removes one or more sensors from a sensor group. |
CreateGroup |
User creates a sensor group. |
EditGroup |
User edits the details of a sensor group. |
EditGroupsPriority |
User edits the priority order for automatic sensor group assignment logic. |
DeleteGroup |
A sensor deletes a sensor group. |
USER MANAGEMENT action group
Event name |
Triggering action |
|---|---|
Add User |
A new user is added to the Cybereason platform. |
Edit User |
A user admin updated an existing user’s details. |
Delete User |
A user is deleted from the Cybereason platform. |
IR TOOLS action group
Event name |
Triggering action |
|---|---|
DeliverPackage |
User uploaded and deployed an IR tool package to endpoint machines. |
DeliverPackageDetails |
User uploaded and deployed an IR tool package to endpoint machines. |
DeletePackage |
User removed an IR tool package from endpoint machines. |
Severity
For each events, the CEF header also contains a Severit field. This field assigns a value for the event from0-10, where 10 is the most severe. See the table below for severity values for each type of event class:
Event class |
Severity value |
|---|---|
Malop |
10 - for all Malops |
Malware |
|
User action |
0 - for all user actions |