Use Endpoint Controls - Tutorial
This topic contains step-by-step examples on how to use Endpoint Controls features.
Block USB storage
In this example, the Cybereason platform’s Device control blocks a USB storage device on a specific endpoint that is governed by the relevant policy.
For the purposes of this scenario, the administrator first turns on the Device control toggle, and then a device is inserted. In a scenario where a USB storage device is already mounted onto the endpoint machine when an administrator turns on the Device control toggle, the Cybereason platform dismounts the device, and after a few seconds, the device is not visible under This PC > Devices and drives. In this scenario, the Cybereason platform does not display a notification.
To block USB storage, follow these steps:
In the System > Policies management screen, create a new policy or select your policy.
In your policy, navigate to the Endpoint controls screen.
In your Endpoint Controls screen, sets the Device control toggle to On and the Block mode selected under the USB (Mass storage) section, and saves the policy.
On an endpoint governed by the policy, the end user inserts a USB storage device. The device is visible momentarily under This PC > Devices and Programs while Cybereason dismounts the device.
The USB storage device is no longer visible under This PC > Devices and drives. The end user receives a “USB device was blocked” notification and cannot access the device.
Note
When the USB storage device is no longer visible in Windows, you can view the device details in the Investigation screen under the Mount Point element.
Block FTP access
In this example, the Personal firewall control option is enabled, and a custom rule is applied to block FTP access to a specific IP address and port.
To block FTP access, follow these steps:
In the System > Policies management screen, create a new policy or select your policy.
In your policy, navigate to the Endpoint controls screen.
In the Endpoint controls screen, set the Personal firewall control toggle to On and selects all network profiles (Domains, Private Networks, Public Networks), and saves the policy.
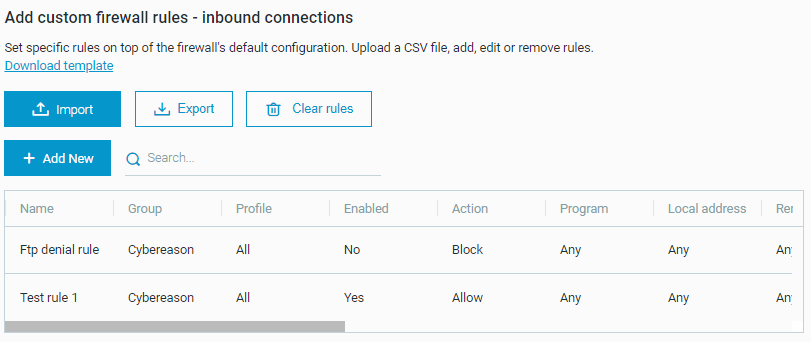
Creates a CSV file for outbound connections and creates a rule that includes the following values:
Name: Ftp denial example
Group: Cybereason
Action: Block
Remote address: 66.220.9.50
Protocol: TCP
Remote Port: 21
Note
This set of fields defines a rule for all endpoints under this policy. According to the rule, all outgoing FTP connection attempts that use the TCP protocol to connect to the 66.220.9.50 IP address on port 21 are blocked.
Under Upload custom rule list - outbound connections, clicks Upload CSV and select the file. The custom rules are visible in a table, indicating that the rules have been uploaded to Cybereason.
Accesses an endpoint to which you have assigned the policy and verify that the rule exists in Windows Firewall, indicating that the rule has been applied.
Note
The rule must also appear under Monitoring > Firewall. Otherwise, the rule is not currently active. The problem may occur if a mistake exists in the CSV file or if the endpoint network profile does not match the rule (for example, if the endpoint is on a public network and the rule is defined for private and domain network profiles).
The administrator attempts to connect to the network via FTP using the command prompt, and connection fails silently.
Note
This example uses the command line to attempt an FTP connection. Unlike third-party tools used for FTP connections, the command line does not generate an error stating that the connection was not successful. When an FTP connection is successful, the user receives a message that is similar to the following message on the command line:
Read only notifications
If you set Device control to Read only mode, Cybereason displays this system tray notification when a device is connected: